Is Chrome.exe a virus? In most cases, Chrome.exe isn’t a virus. It’s a safe and trusted process used by Google Chrome’s web browser. Chrome.exe runs multiple instances of Chrome.exe in your Task Manager (and here’s why).
Should I discard Chrome exe?
Is Chrome.exe a virus? In most cases, Chrome.exe isn’t a virus. It’s a safe and trusted process used by Google Chrome’s web browser. Chrome.exe runs multiple instances of Chrome.exe in your Task Manager (and here’s why).
How do I get rid of Chrome exe virus?
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall. In the uninstall programs window, look for “Chrome.exe virus”, select this entry and click “Uninstall” or “Remove”.
Is a file ending in exe a virus?
For every app or program you run on a Windows PC, the file that actually makes the computer run the program is the .exe. .Exe files can also be used to distribute viruses and other types of malicious software (or “malware”) that infect devices and steal information.
How do I get rid of Chrome exe virus?
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall. In the uninstall programs window, look for “Chrome.exe virus”, select this entry and click “Uninstall” or “Remove”.
Why do I have so many chrome exe?
You may have noticed that Google Chrome will often have more than one process open, even if you only have one tab open. This occurs because Google Chrome deliberately separates the browser, the rendering engine, and the plugins from each other by running them in separate processes.
How do I remove Chromium virus from Windows 10?
#1) Click on the “Windows” button and search for “Control Panel”. #2) Click on “Programs”, and then click on “Uninstall a program”, as shown in the image below. #3) Now, locate “Chromium” from the list of programs and right-click on it, then click on “Uninstall”.
Why does Chrome keep telling me I have a virus?
The Google Chrome pop-up virus is a common and frustrating malware on Android phones. The most common cause for this virus is downloading apps from third-party or unknown sources which contain the malware. The most important thing is to NOT tap anywhere on the pop-up!
Where is Chromedriver exe located?
You can download the chromedriver.exe from this link: https://sites.google.com/a/chromium.org/chromedriver/downloads. You will also find links to previous versions of cromedriver.
Where is Chromedriver exe in Windows?
You can drop the chromedriver.exe in your virtual environment’s bin/ directory. Then try running the Python script with the virtual env’s interpreter. Show activity on this post. My chromedriver package was installed in my Python folder.
How can I tell if an exe is a virus?
Scan the EXE With VirusTotal Another way to find out if the EXE is legit is to scan it with VirusTotal. You simply upload the suspicious file on the VirusTotal website, and this online scanner will check it for all types of malware.
Can exe files be hacked?
One of the most common tricks used by hackers is to get unsuspecting users to click on a malicious .exe file which leads to malware being downloaded onto a computer. They’re usually sent to you as an email attachment with the email offering some form of compelling inducement to get you to open the attachment.
Do I need Svchost exe?
Svchost.exe is a required Windows file and is used to load needed DLL files used with Microsoft Windows and Windows programs that run on your computer.
Should I discard Chrome exe?
Is Chrome.exe a virus? In most cases, Chrome.exe isn’t a virus. It’s a safe and trusted process used by Google Chrome’s web browser. Chrome.exe runs multiple instances of Chrome.exe in your Task Manager (and here’s why).
How do I get rid of Chrome exe virus?
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall. In the uninstall programs window, look for “Chrome.exe virus”, select this entry and click “Uninstall” or “Remove”.
Should I let Google Chrome run in the background?
Since Chrome is already running in the background, there is less that has to take place behind the scenes before your new browser window appears. This makes the browser feel quick, even on slower machines. Running in the background also allows any Chrome extensions you might have installed to continue to operate.
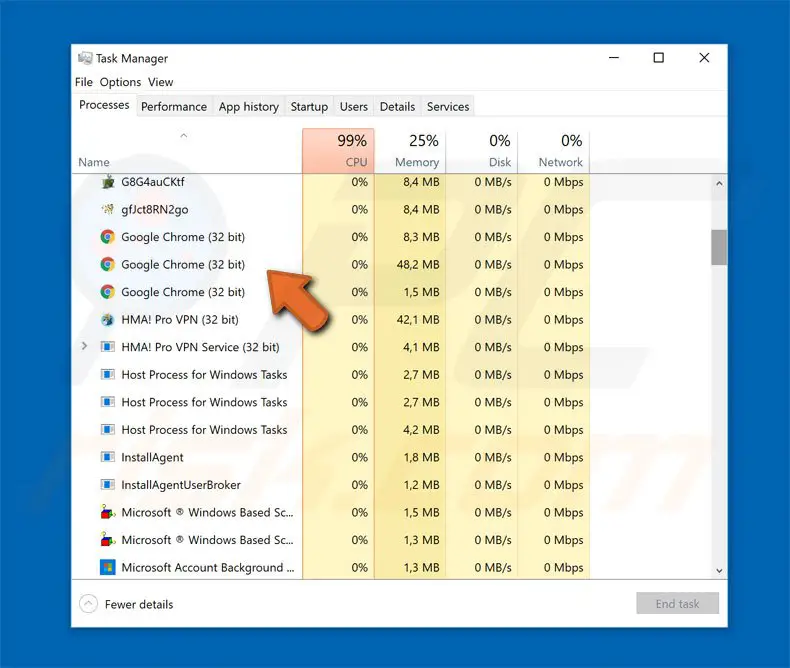
Why are there multiple Google chromes in Task Manager?
Google chrome uses multi-process architecture to prioritize performance while using the browser. This is the reason why the task manager shows multiple google chrome processes.
Why is Google Chrome taking up so much CPU?
Explaining Chrome’s CPU Usage These typically relate to your browsing behavior, including having too many tabs open at once, too many apps or browser extensions running and streaming high-quality video. Likewise, auto-playing videos, animations and excessive ads can also cause these problems.
Does Chromium send data to Google?
In other words, Ungoogled Chromium doesn’t send your data back to Google, because it doesn’t contain any Google code at all.
What is the difference between Chrome and Chromium?
Chromium is an open-source and free web browser that is managed by the Chromium Project. In comparison, Google Chrome is a proprietary browser developed and managed by Google. Unlike Chromium, Google Chrome offers built-in support for media codecs like MP3, H. 264, and AAC, as well as Adobe Flash.
How can you tell a fake virus warning?
The Federal Trade Commission (FTC) warns that the scareware scam has many variations, but there are some telltale signs: You may get ads that promise to “delete viruses or spyware,” “protect privacy,” “improve computer function,” “remove harmful files,” or “clean your registry.”
Is the Google virus warning real?
Google Security Alert/Warning is a fake alert issued by malicious websites. Like all social engineering, it’s designed to trick users into making an unsafe decision online. Chrome and Android devices have security alerts, but they aren’t labeled “Google Security Alert”.