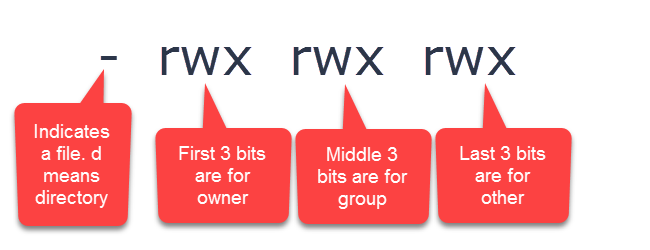
The Permission Types that are used are: r – Read. w – Write. x – Execute.
What are 3 different types of permissions in Linux?
The type of permission: +r adds read permission. -r removes read permission. +w adds write permission.
What are the three file access permissions?
UNIX-based systems such as Linux used POSIX-style access control lists. This means files have three permission modes: read (r), write (w), and execute (x). These modes can be assigned either using the letters just listed or they also have equivalent numbers. Read is 4, write is 2, and execute is 1.
What are basic permissions?
Basic permissions provide a simpler and less granular way to set permissions. Another way to think of it is that basic permissions are groups of advanced permissions. The basic permissions are: Full Control: Users can read, modify, add, move, and delete files, as well as their associated properties and directories.
What are the two types of permissions?
Each permission that exists can be assigned one of two ways: explicitly or by inheritance. For this reason, permissions are referred to as explicit permissions and inherited permissions. Explicit permissions are permissions that are set by default when the object is created, or by user action.
What are four basic permissions?
There are four categories (system, owner, group, and world) and four types of access permissions (Read, Write, Execute and Delete). The categories are not mutually disjoint: World includes Group, which in turn includes Owner.
What are the 3 types of files in Unix?
The seven standard Unix file types are regular, directory, symbolic link, FIFO special, block special, character special, and socket as defined by POSIX.
What are the 3 permissions for directories and files and what do they mean?
Permissions for directories Read permission means that the user may see the contents of a directory (e.g. use ls for this directory.) Write permission means that a user may create files in the directory. Execute permission means that the user may enter the directory (i.e. make it his current directory.)
What are access permissions?
User permissions, part of the overall user management process, are access granted to users to specific resources such as files, applications, networks, or devices.
What are the 5 different file and folder permissions?
There are basically six types of permissions in Windows: Full Control, Modify, Read & Execute, List Folder Contents, Read, and Write.
What is standard permission?
A standard permission set consists of a group of common permissions for a particular feature associated with a permission set license. Using a standard permission set saves you time and facilitates administration because you don’t need to create the custom permission set.
What are permission levels?
Permission levels are a set of permissions that a particular user or group is allowed to perform specific actions. Each permission levels consist of a number of detailed permissions (such as: Create Alerts, Delete Items, etc).
Why are permissions important?
Asking permission can improve the way people listen to each other. It can help build relationships by demonstrating respect and appreciation for friends, co-workers and family members.
What are the types of file permission explain with example?
Each file and directory has three types of permission: Read: You can view and read the content of the file, but can not edit or modify the file. You can list the content of the directory with “read” permission. Write: You can read and edit the content of the file.
What is user right permission?
User rights and permissions are the levels of access granted to users (company employees), enabling them to perform specific tasks and access resources on your network such as data files or applications.
What are access rights and permissions?
Access Rights are the permissions an individual user or a computer application holds to read, write, modify, delete or otherwise access a computer file; change configurations or settings, or add or remove applications.
What are four basic permissions?
There are four categories (system, owner, group, and world) and four types of access permissions (Read, Write, Execute and Delete). The categories are not mutually disjoint: World includes Group, which in turn includes Owner.
What are permission levels?
Permission levels are a set of permissions that a particular user or group is allowed to perform specific actions. Each permission levels consist of a number of detailed permissions (such as: Create Alerts, Delete Items, etc).
What is standard permission?
A standard permission set consists of a group of common permissions for a particular feature associated with a permission set license. Using a standard permission set saves you time and facilitates administration because you don’t need to create the custom permission set.
What are the 2 types of folders?
Basic folders are the typical choice. They fit just about any filing system at a standard 9.5 inches. Hanging file folders are your smaller option, but this is because they sacrifice space to come equipped with hooks to hang inside your drawers.
What is formal permission?
1. authorization granted to do something; formal consent. to ask permission to leave the room.
What is direct permission?
Direct permissions are assigned to users directly by product administrators. For example, an Analytics user who has the Administrator role can assign the Editor role directly to other users. Inherited permissions can be assigned via: Another direct permission in the same product.