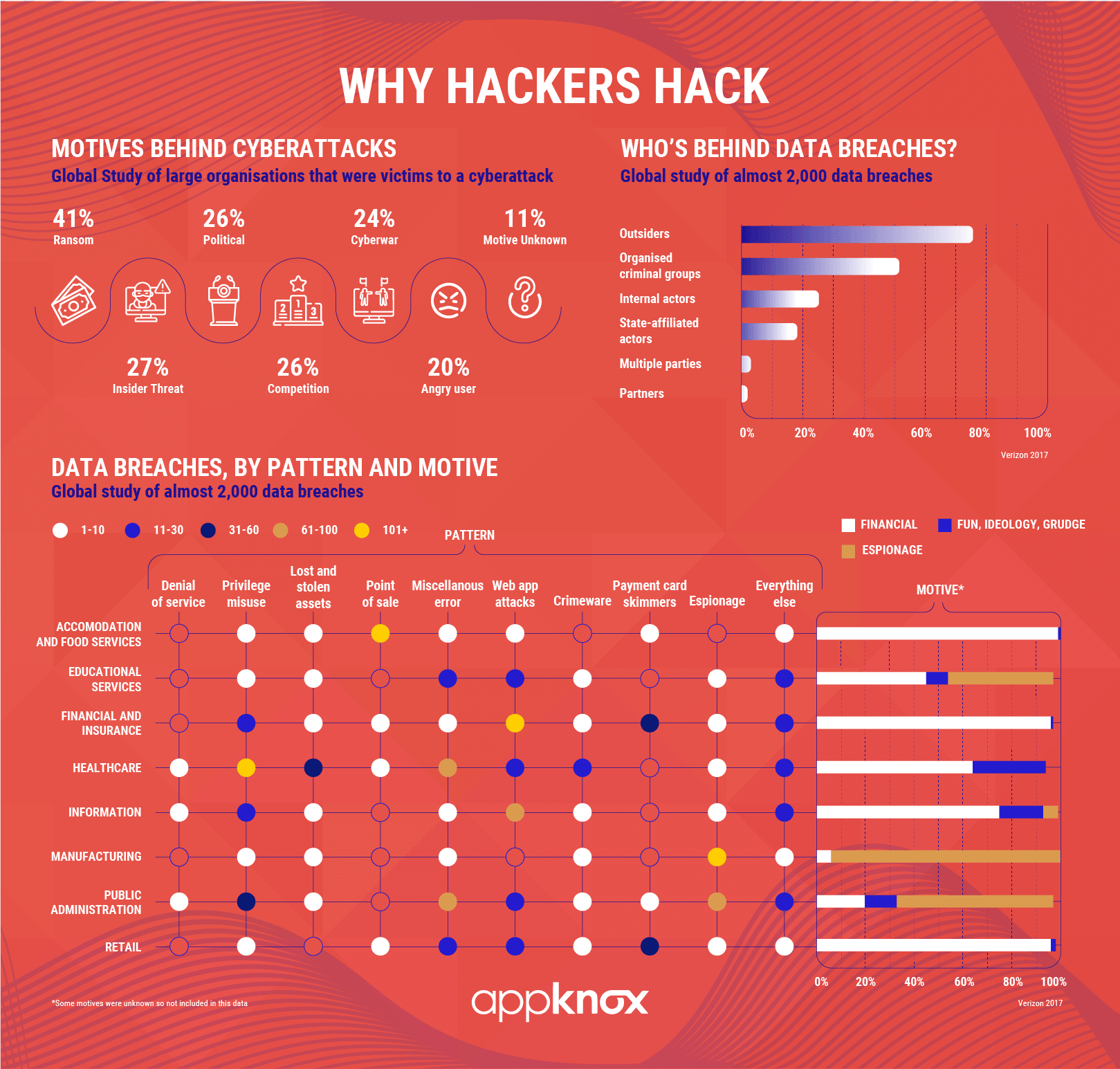
Some common reasons for hacking include basic bragging rights, curiosity, revenge, boredom, challenge, theft for financial gain, sabotage, vandalism, corporate espionage, blackmail, and extortion. Hackers are known to regularly cite these reasons to explain their behavior.
What do hackers usually look for?
The goal might be financial gain, disrupting a competitor or enemy, or theft of valuable data or intellectual property. Their clients might be nation-states, companies interested in corporate espionage, or other criminal groups looking to resell what the hackers steal.
What is usually hackers only intention?
One of the most common reasons for hackers to hack is to steal or leak information. This could be data and information about your customers, your internal employees or even private data specific to your business. These are cases where hackers typically go after big targets in order to get the most attention.
What do most hackers use to hack?
Some of the most famous hacking tools in the market are Nmap (Network Mapper), Nessus, Nikto, Kismet, NetStumbler, Acunetix, Netsparker, and Intruder, Nmap, Metasploit, Aircrack-Ng, etc.vor 6 Tagen
What do hackers usually look for?
The goal might be financial gain, disrupting a competitor or enemy, or theft of valuable data or intellectual property. Their clients might be nation-states, companies interested in corporate espionage, or other criminal groups looking to resell what the hackers steal.
How do hackers know who to target?
Such data may include passwords, usernames, and personal information that includes full names and addresses. With easily accessible personal data, hackers can go online and start draining bank accounts and commit all sorts of identity theft crimes.
How do hackers trick you?
The process of getting tricked into giving your sensitive information to a hacker is called phishing. Phishing is the fraudulent attempt to obtain sensitive information, or data, such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication.
How do hackers get away with it?
Hackers will often use secure software such as a proxy server to hide their identity and funnel their communications through lots of different countries in order to evade detection. Other technologies like Tor and encryption enable them to add multiple layers to mask their identity.
What can hackers take from you?
Hackers illegally access devices or websites to steal peoples’ personal information, which they use to commit the crimes like theft. Many people shop, bank, and pay bills online. People also store financial information, like credit card or bank account numbers, on their devices.
What is the most hacked thing?
Do hackers use coding to hack?
Access Hardware: Hackers use C programming to access and manipulate system resources and hardware components such as the RAM. Security professionals mostly use C when they are required to manipulate system resources and hardware. C also helps penetration testers write programming scripts.vor 6 Tagen
Why do hackers hack for fun?
As a result, they can make money in multiple ways. Another method they can use to gain cash is selling essential data on the dark web. Other than financial gains, there are different motivations such as taking personal revenge, desire to learn, and the main topic of our article, which is hacking for fun and profit.
What is the most hacked thing?
What data is most valuable to hackers?
Personal data While passport information sells for the most amount of money, Social Security numbers are the most valuable to hackers, as these can be used for tax fraud, opening credit accounts, and other malicious activities.
What do hackers usually look for?
The goal might be financial gain, disrupting a competitor or enemy, or theft of valuable data or intellectual property. Their clients might be nation-states, companies interested in corporate espionage, or other criminal groups looking to resell what the hackers steal.
Can hackers see you?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Can a hack be traced?
Most hackers will understand that they can be tracked down by authorities identifying their IP address, so advanced hackers will attempt to make it as difficult as possible for you to find out their identity.
Why do hackers keep targeting me?
Most hackers are on the lookout for one thing: money. They may not be hunting for it directly, but that is typically the end goal of most hackers, except state-sponsored hackers that are after secret information. Bearing in mind this goal, hackers will tend to target someone they either think or know has money.
Can hackers hack with phone number?
“In today’s world, it is extremely easy for hackers to wreak havoc on your life using your cell phone number,” says Hari Ravichandran, CEO of consumer cybersecurity company Aura. To protect your sensitive information, you should always think twice before sharing your phone number—especially in a public setting.
What are 3 reasons that hackers hack?
Some common reasons for hacking include basic bragging rights, curiosity, revenge, boredom, challenge, theft for financial gain, sabotage, vandalism, corporate espionage, blackmail, and extortion. Hackers are known to regularly cite these reasons to explain their behavior.
What do hackers do for a living?
Today, the term “hacker” is more frequently used to describe someone who discovers and exploits a computer system weakness or vulnerability. Hackers use vulnerabilities to block system access, gather information, or gain access to more computers in a network.
How hard is it to catch a hacker?
First up, catching a hacker is very, very difficult. Even a novice can hide their identity using “obfuscation” technologies. Leo Taddeo, a former New York FBI special agent in charge of fighting cyber crime, explains the problem. “Hackers use tools to disguise their IP address,” he says.