A port or berth will be unsafe if the ship is unable to reach the port safely. For example a port may be considered unsafe even if the ship suffers damage during its passage on a river or channel when approaching a port.
What is an unsafe port?
A port or berth will be unsafe if the ship is unable to reach the port safely. For example a port may be considered unsafe even if the ship suffers damage during its passage on a river or channel when approaching a port.
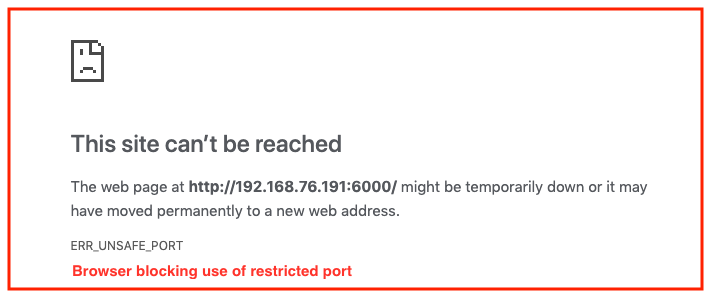
Is 6000 an unsafe port?
6000 is considered an unsafe port by Chrome.
What ports does Chrome consider unsafe?
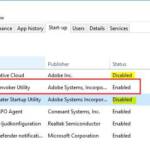
Google chrome considers 6000 as an unsafe port. HERE is a list of unsafe ports which are not allowed by browser. Use any other port or 5000 as I have used in the project. Make sure to use the same port in src/utils/constants.
What ports does Chrome consider unsafe?
Google chrome considers 6000 as an unsafe port. HERE is a list of unsafe ports which are not allowed by browser. Use any other port or 5000 as I have used in the project. Make sure to use the same port in src/utils/constants.
What ports are suspicious?
Ports 80, 443, 8080 and 8443 (HTTP and HTTPS) HTTP and HTTPS are the hottest protocols on the internet, so they’re often targeted by attackers. They’re especially vulnerable to cross-site scripting, SQL injections, cross-site request forgeries and DDoS attacks.
What ports do hackers look for?
Though the number of commonly hacked ports has constantly grown in the past years, it is important to keep in mind that most attackers are looking first in probing ports 22 [SSH] and 80 [HTTP]. For instance, port 22 [SSH] is a common port constantly probed by hackers on the Internet using brute force attacks.
Is port 666 used?
Port 666 Details. Doom game (ID Software) uses this port. Dark and Light [game] uses this port. Because of the cool connotations, this port is also used by numerous trojan horses/backdoors.
Is port 22 unsafe?
As such, Port 22 is subject to countless, unauthorized login attempts by hackers who are attempting to access unsecured servers. A highly effective deterrent is to simply turn off Port 22 and run the service on a seemingly random port above 1024 (and up to 65535).
Is port 445 safe to open?
Avoid Exposing SMB Ports Ports 135-139 and 445 are not safe to publicly expose and have not been for a decade.
Is it safe to open 443 port?
HTTPS is secure and is on port 443, while HTTP is unsecured and available on port 80. Information that travels on the port 443 is encrypted using Secure Sockets Layer (SSL) or its new version, Transport Layer Security (TLS) and hence safer.
Is port 8080 vulnerable?
Port 8080 and 8088 — HTTP Alternative Because these two ports are HTTP alternatives for web traffic, they inherently do not have encryption embedded during data communication. This makes all web traffic communicated over the network susceptible to being sniffed and intercepted by threat actors.
Is port 23 unsecure?
Port 23, Telnet There is no justification for using this ancient and insecure means of text-based communication. All the information it sends and receives through port 23 is sent in plain text. There is no encryption at all.
Why is port 22 blocked?
There could be several reasons behind the error like the SSH service is inactive, the port is blocked by ufw firewall, the server is using a different port, or because of some IP conflict.
Why is port 21 blocked?
Some routers and firewalls block FTP port 21 due to security reasons, so it’s essential to check the port’s connection before performing the File Transfer Protocol. You might also want to check out our articles on solving FTP issues like solving error 421 – too many connections and ECONNREFUSED.
Is port 22 unsafe?
As such, Port 22 is subject to countless, unauthorized login attempts by hackers who are attempting to access unsecured servers. A highly effective deterrent is to simply turn off Port 22 and run the service on a seemingly random port above 1024 (and up to 65535).
Is port 8080 vulnerable?
Port 8080 and 8088 — HTTP Alternative Because these two ports are HTTP alternatives for web traffic, they inherently do not have encryption embedded during data communication. This makes all web traffic communicated over the network susceptible to being sniffed and intercepted by threat actors.
What is an unsafe port?
A port or berth will be unsafe if the ship is unable to reach the port safely. For example a port may be considered unsafe even if the ship suffers damage during its passage on a river or channel when approaching a port.
What ports does Chrome consider unsafe?
Google chrome considers 6000 as an unsafe port. HERE is a list of unsafe ports which are not allowed by browser. Use any other port or 5000 as I have used in the project. Make sure to use the same port in src/utils/constants.
What are the 2 possible signs that you have been hacked?
Some of the warning signs that you’ve been hacked include: You receive emails or text messages about login attempts, password resets, or two-factor authentication (2FA) codes that you didn’t request. You see logins from devices and locations you don’t recognize in your account activity or sign-in logs.
What is a 7777 port?
Side note: UDP port 7777 uses the Datagram Protocol, a communications protocol for the Internet network layer, transport layer, and session layer. This protocol when used over PORT 7777 makes possible the transmission of a datagram message from one computer to an application running in another computer.
Is port 444 used?
The port 444 is standard for SNPP servers, and it is free to use from the sender’s point of view. Maximum message length can be carrier-dependent. Once connected, a user can simply enter the commands to send a message to a pager connected to that network.