A breached phone might be giving all its processing power over to the hacker’s shady applications. This can cause your phone to slow to a crawl. Unexpected freezing, crashes, and unexpected restarts can sometimes be symptoms. You notice strange activity on your other online accounts.Malware and fraudulent apps sometimes use malicious code that tends to drain a lot of power. Your phone runs abnormally slowly. A breached phone might be giving all its processing power over to the hacker’s shady applications. This can cause your phone to slow to a crawl.
Can you tell if your phone is hacked?
Poor performance: If your phone shows sluggish performance like crashing of apps, freezing of the screen and unexpected restarts, it is a sign of a hacked device. Unrecognised apps: If you notice any unrecognised applications downloaded on your device, it could be the work of a hacker.
Can you Unhack your phone?
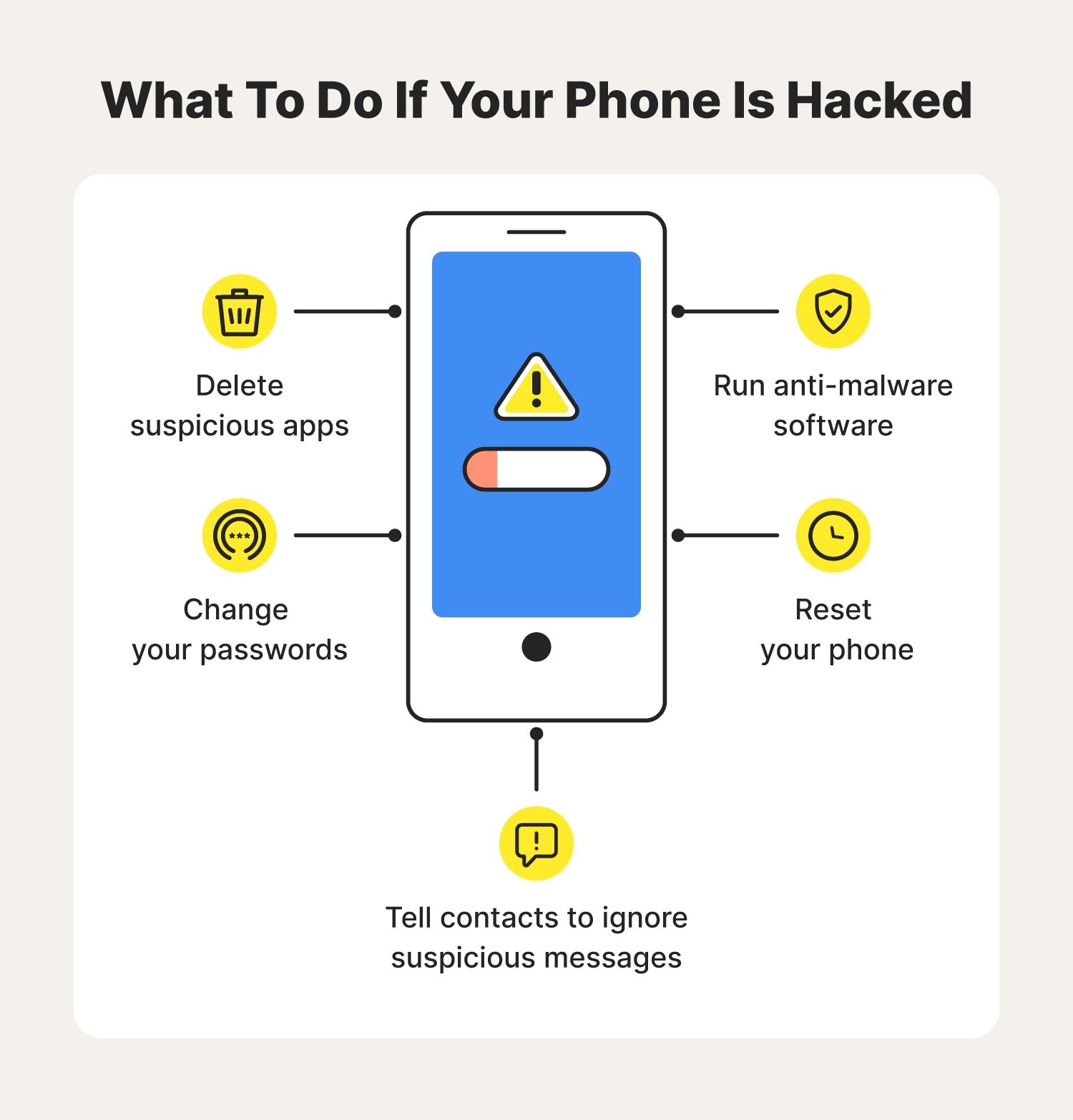
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
Should you turn your phone off if its been hacked?
At a time of widespread digital insecurity, it turns out that the oldest and simplest computer fix there is – turning a device off then back on again – can thwart hackers from stealing information from smartphones.
Can you tell if your phone is hacked?
Poor performance: If your phone shows sluggish performance like crashing of apps, freezing of the screen and unexpected restarts, it is a sign of a hacked device. Unrecognised apps: If you notice any unrecognised applications downloaded on your device, it could be the work of a hacker.
Can resetting your phone remove hackers?
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device. Follow the instructions below to reset your iPhone or Android.
Can hackers see you through your phone camera?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Who is accessing my phone?
To check your mobile data usage on Android, go to Settings > Network & Internet > Data Usage. Under Mobile, you’ll see the total amount of cellular data being used by your phone. Tap Mobile Data Usage to see how your data use has changed over time. From here, you can identify any recent spikes.
Can someone hack your phone just by knowing your number?
Two-factor authentication. It’s important to reiterate that it’s not possible for someone to just simply type your number into some shady software and click “HACK”. There is usually a process of tricking you into doing something as mentioned above.
Can I tell if my iPhone is hacked?
How can I tell if my iPhone has been hacked? The easiest way to tell if your iPhone has been hacked is by running a full device scan with top-tier antivirus security software. This will check your iPhone for any suspicious apps or activity and alert you to any unusual behaviors that may have gone unnoticed.
Who is accessing my phone?
Open the Android Settings app. Tap “Mobile Network” (It’s in the “Network & Internet” section.) On the Mobile Network screen, tap “App Data Usage.” Here, you can view your current cellular app data usage.
Can you tell if your phone is hacked?
Poor performance: If your phone shows sluggish performance like crashing of apps, freezing of the screen and unexpected restarts, it is a sign of a hacked device. Unrecognised apps: If you notice any unrecognised applications downloaded on your device, it could be the work of a hacker.
Can you tell if your phone is being monitored?
Yes, there are signs that will tell you when your phone is being monitored. These signs include overheating of your device, the battery draining fast, receiving odd text messages, hearing weird sounds during calls, and random reboots of your phone.vor 4 Tagen
Is there an app to stop hackers?
Norton is the leading antivirus app for Android and iOS devices and will protect your phone against all types of cyberthreats, including phishing links, identity theft, viruses, malware, and more.
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.
How do I know if my phone is linked to another device iPhone?
Sign in to appleid.apple.com,* then select Devices. If you don’t see your devices right away, click View Details and answer your security questions. Click any device name to view that device’s information, such as the device model, serial number, and OS version.
What can hackers do?
Hijack your usernames and passwords. Steal your money and open credit card and bank accounts in your name. Ruin your credit. Request new account Personal Identification Numbers (PINs) or additional credit cards.
Can someone hack my phone from a text message?
Android phones can get infected by merely receiving a picture via text message, according to research published Monday. This is likely the biggest smartphone flaw ever discovered.
Is the virus warning on my iPhone real?
Apple Security Alert is a fake pop-up message which states that your iOS device was hacked and that your personal information is at risk. Users can get this alert by visiting a suspicious website or get redirected if they have a potentially unwanted program (PUP) installed on their Mac or iPhone.
How do I scan my phone for malware?
To check for malware on your Android device, go to the Google Play Store app and click the three-line icon in the top-left left corner of your screen. Then Google Play Protect and tap the scan button.
Can you get a virus on your phone by visiting a website?
Can phones get viruses from websites? Clicking dubious links on web pages or even on malicious advertisements (known as malvertising) can download malware to your cell phone. Similarly, downloading software from these websites can also lead to malware being installed on your Android phone or iPhone.
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.
How can your phone be hacked?
Physical access is the easiest way for a hacker to corrupt your phone. Theft and a single day of effort could result in your phone being breached. If you can keep your phone with you, a hacker will have to work much harder to get into it. Always use a passcode lock and use complex passwords.
What are the consequences of a hacked phone?
Cybercriminals’ strategies are constantly evolving, and once a device is breached, it’s in their hands. From playing online poker to going on shopping sprees using your payment information, the consequences of a hacked phone are more than annoying—they’re dangerous.
Is it possible to hack into an iPhone?
Phone hacking can happen to all kinds of phones, including Androids and iPhones. Since anyone can be vulnerable to phone hacking, we recommend that all users learn how to identify a compromised device. One or more of these could be a red flag that some has breached your phone: Your phone loses charge quickly.
Are you vulnerable to phone hacking?
Unfortunately, anyone can be vulnerable to phone hacking. It doesn’t matter whether you use an Android or iPhone; it can happen to any smartphone. The information located on your device can be highly attractive to both cybercriminals and even acquaintances.