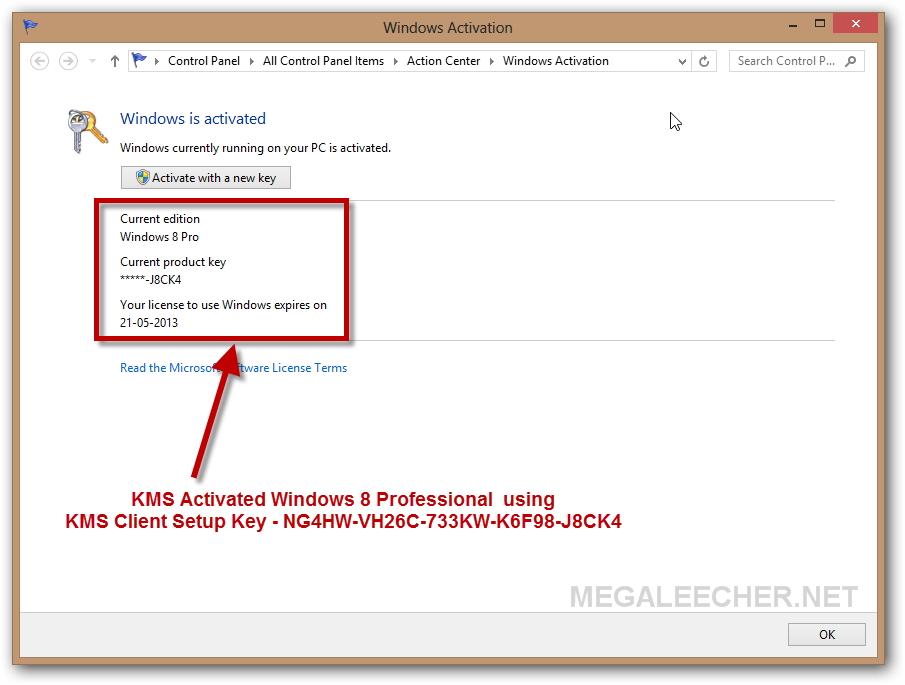
Key Management Service in Windows 10 Installing a KMS host key on a computer running Windows 10 allows you to activate other computers running Windows 10 against this KMS host and earlier versions of the client operating system, such as Windows 8.1 or Windows 7.
What is the use of KMS activator?
Key Management Service in Windows 10 Installing a KMS host key on a computer running Windows 10 allows you to activate other computers running Windows 10 against this KMS host and earlier versions of the client operating system, such as Windows 8.1 or Windows 7.
Is KMS activator legal?
No, they are not legal. Be aware of those KMS, some of them might include virus/malware that might damage your PC.
Are KMS activator safe?
Angelo B37. Microsoft’s Defender will find the KMS activater as a threat and other antivirus software will also do it. We have no information if this kind of tools have malware, we simply advise not to use it. If you do want to use illegal software please use it at your own risk.
Is KMS activator a virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
Is KMS activation permanent?
KMS activations are valid for 180 days, a period known as the activation validity interval. KMS clients must renew their activation by connecting to the KMS host at least once every 180 days to stay activated.
How do I activate KMS?
Open the command prompt, type slmgr /ipk followed by the 25-digit KMS host product key and press Enter. Then, use slmgr /ato to activate the host key.
Is KMS CMD activation safe?
Yes… its safe but its depends upon you which windows activator you are using. some time we try to download windows activator from random source and there may be chances of viruses enter in your system. so follow best one.
How does Kmspico Activator work?
A KMS client connects to a KMS server (the activation host), which contains the host key the client uses for activation. Once KMS clients are validated, the Microsoft product on those clients contacts the server every 180 days (6 months) to maintain its validity.
Can KMS server control your PC?
AFIK the KMS Server has no other rights or privileges on your computer.
Is KMSpico a virus?
KMSpico is a potentially harmful file since it might contain a virus; hence, it would infect the computer in this scenario, and it would be required to destroy it once it has been downloaded.
Can I delete KMSpico after activation?
Yes you can remove KMSpico but dont do it. You may have activated windows or ms office with kmspico now you think that it is useless, no its not like this, to keep your windows activated do not remove kmspico. If you remove it then your windows will go again in trail mode.
Is AutoKMS a malware?
AutoKMS is Malwarebytes’ generic detection name for hacktools that are intended to enable the illegal use of Microsoft products like Windows and Office.
Does KMSPico have Trojan?
There are many people who are wondering if KMSPico is a virus or not. The answer to this question is not as simple as it may seem. While KMSPico is not technically a virus, there is a possibility that it could infect your computer with malware if you download and install it from an untrustworthy source.
Is kms Pico a virus?
KMSpico is a potentially harmful file since it might contain a virus; hence, it would infect the computer in this scenario, and it would be required to destroy it once it has been downloaded.
How does an office Activator work?
MAK activation is used for one-time activation through Microsoft-hosted activation services, either via the internet or by telephone. MAK activation requires that a MAK is installed on a client computer and instructs that computer to activate itself against those services.
What is Microsoft KMS license?
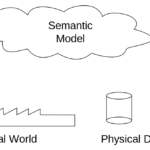
The Key Management Service (KMS) is an activation service that allows organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation.
What is KMS client key?
To use KMS, you need to have a KMS host available on your local network. Computers that activate with a KMS host need to have a specific product key. This key is sometimes referred to as the KMS client key, but it is formally known as a Microsoft Generic Volume License Key (GVLK).
How long is KMS activation?
Any Windows client that configured to use ‘KMS Client Channel’ will be activated against the new KMS host automatically within 2 hours (as this is the ‘KMS Activation Interval’ default value).
Do I need a KMS server?
KMS hosts do not need to be dedicated servers, and KMS can be co-hosted with other services. You can run a KMS host on any physical or virtual system that is running a supported Windows Server or Windows client operating system.
What happens if I dont activate Windows?
But what if you don’t activate windows? Not activating windows will not cripple your ability to use the software. In fact, the only difference between an activated and unactivated Windows operating system is the ability to customize the look and feel of your user interface.
What is KMS service?
KMS (Key Management Service) is one of the methods to activate Microsoft Windows and Microsoft Office. Activation ensures that the software is obtained from and licensed by Microsoft. KMS is used by volume license customers, usually medium to large businesses, schools, and non-profits.