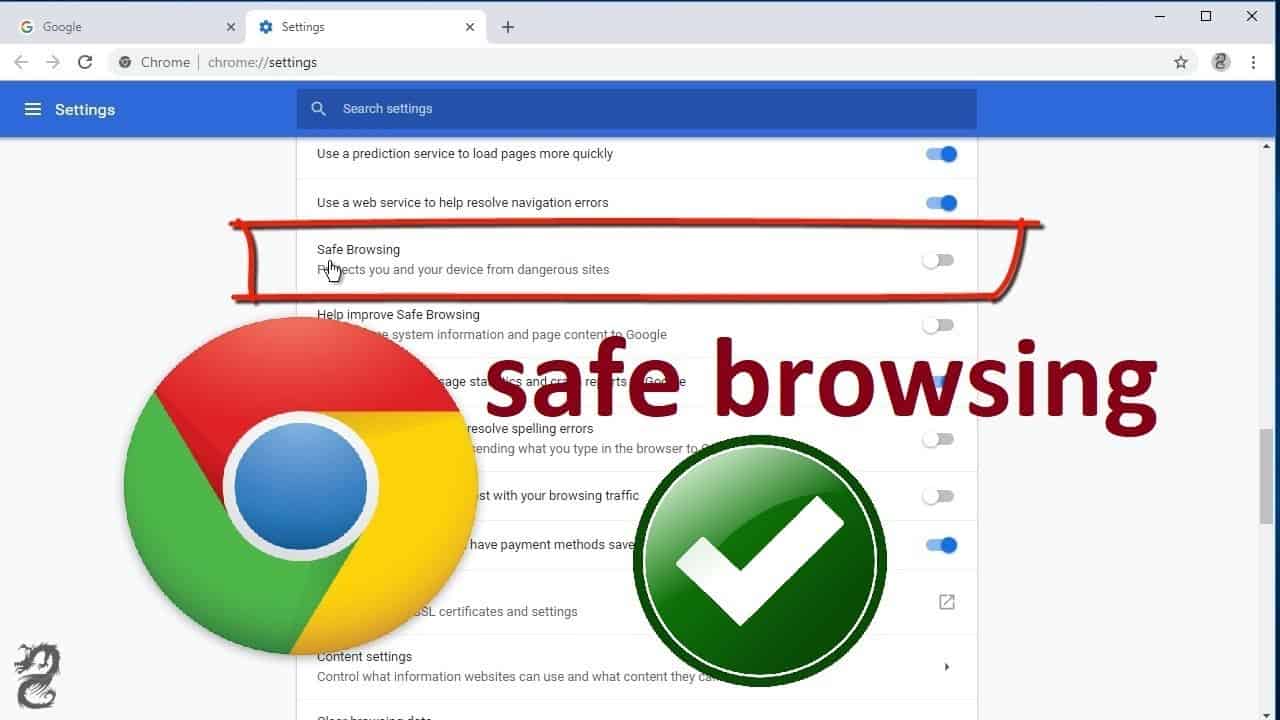
Google Chrome — Google maintains the most comprehensive database of malicious websites and frequently updates Chrome. Vivaldi — Blocks ads on abusive sites by default, collects little user data, and protects users with Google Safe Browsing.
Is Google Chrome more secure?
Luckily, Chrome is one of the most secure browsers available. It comes with many built-in features to ensure your online safety, but you might not be familiar with all of them.
What is the safest and most secure browser?
Brave is arguably one of the best web browsers for all-around security. The open source browser includes a built-in ad blocker, a script blocker, automatically upgrades to HTTPS, blocks all third-party storage and protects against browser fingerprinting.
Which browser do hackers use?
Almost every ethical hacker and security researcher prefers the Mozilla Firefox browser for web-based application penetration testing.
Should I use Chrome or Google?
Those who are looking to find out information based on keywords or phrases will want to just use the Google search bar, but those who are looking to have multiple tabs open or are looking for a particular website will want to choose Google Chrome.
Has Google Chrome been hacked?
G oogle has announced that Google Chrome has been successfully hacked as it discovers 30 security flaws–seven of which pose a “high” threat to users. In a blog post, Google revealed that a new update will make improvements for Windows, Mac, and Linux, to fix the security issues after the hack.
Which browser is safe for online banking?
The Edge browser in Windows 10 is a new sandboxed app, so it’s much better for banking than Internet Explorer. Otherwise, Chrome is the most secure alternative, because it runs in Google’s own strong sandbox. Some security companies also provide add-ons, such as Kaspersky Safe Money and Bitdefender Safepay.
Is Safari safer than Chrome?
It may have been true then, but it’s not true anymore. In fact, Safari beats Chrome on the Mac because it’s more energy-efficient, better at protecting your privacy, and it seamlessly works with the Apple ecosystem.
Is Google safe to use?
Google Chrome is a very intuitive internet browser. It is relatively easy to use and secure. Additionally, Google Chrome comes with built-in transparency protection. The safe browsing features warn users when they run into phishing or malware sites.
Which browser is safer Chrome or Firefox?
Google Chrome is by all accounts a secure browser, with features like Google Safe Browsing, which helps protect users by displaying an impossible-to-miss warning when they attempt to navigate to dangerous sites or download dangerous files. In fact, both Chrome and Firefox have rigorous security in place.
Is Firefox safer than Google?
Firefox is a more private and secure browser than Chrome, but Chrome is faster and contains more features. Is Firefox Safer Than Chrome? Both browsers are safe, but Firefox’s tracking protection is more comprehensive than Chrome’s.
What is the most unsafe browser?
According to a study done by researchers at Trinity College, Yandex and Edge are the two worst browsers for security. The study also found that Edge sends users’ hardware ID, IP address, and location to back-end servers which over time can reveal your identity.
What is a dark web hacker?
The dark web brings to mind images of malicious agents sneaking around online in search of illegal drugs, personal information and the newest ransomware software. Its origins, however, lie with the U.S. government as a means for sharing sensitive information.
Which browser is best for bug bounty?
Limitations: The bounty is offered only for bugs in Mozilla services, such as Firefox, Thunderbird and other related applications and services.
What is the fastest and most secure web browser?
1. Google Chrome. If you’re looking for a fast internet browser, Chrome is the best browser for raw speed.
Is Google getting rid of Chrome?
What’s the difference between Chrome and Google?
Google is the parent company that makes Google search engine, Google Chrome, Google Play, Google Maps, Gmail, and many more. Here, Google is the company name, and Chrome, Play, Maps, and Gmail are the products. When you say Google Chrome, it means the Chrome browser developed by Google.
Should I get rid of Chrome?
The tech giant recently issued a warning to its 2.6billion users about a security flaw in the browser that could be exploited by hackers. While Google has maintained that it is working hard to protect users’ security, cyber experts say it’s time to leave Chrome behind.
What is Chrome’s strongest security?
Advanced Protection is Google’s strongest account security, which comes with some restrictions on your account: You need your security key to sign in on any new device.
How I know my phone is hacked or not?
Poor performance: If your phone shows sluggish performance like crashing of apps, freezing of the screen and unexpected restarts, it is a sign of a hacked device. Unrecognised apps: If you notice any unrecognised applications downloaded on your device, it could be the work of a hacker.
Can Chrome passwords be hacked?
Hackers can steal your Google Chrome or Microsoft Edge login password through malware, experts claim. Dangerous malware can steal your Google Chrome or Microsoft Edge login password stored in the browsers. Dangerous malware can steal your Google Chrome or Microsoft Edge login password stored in the browsers.