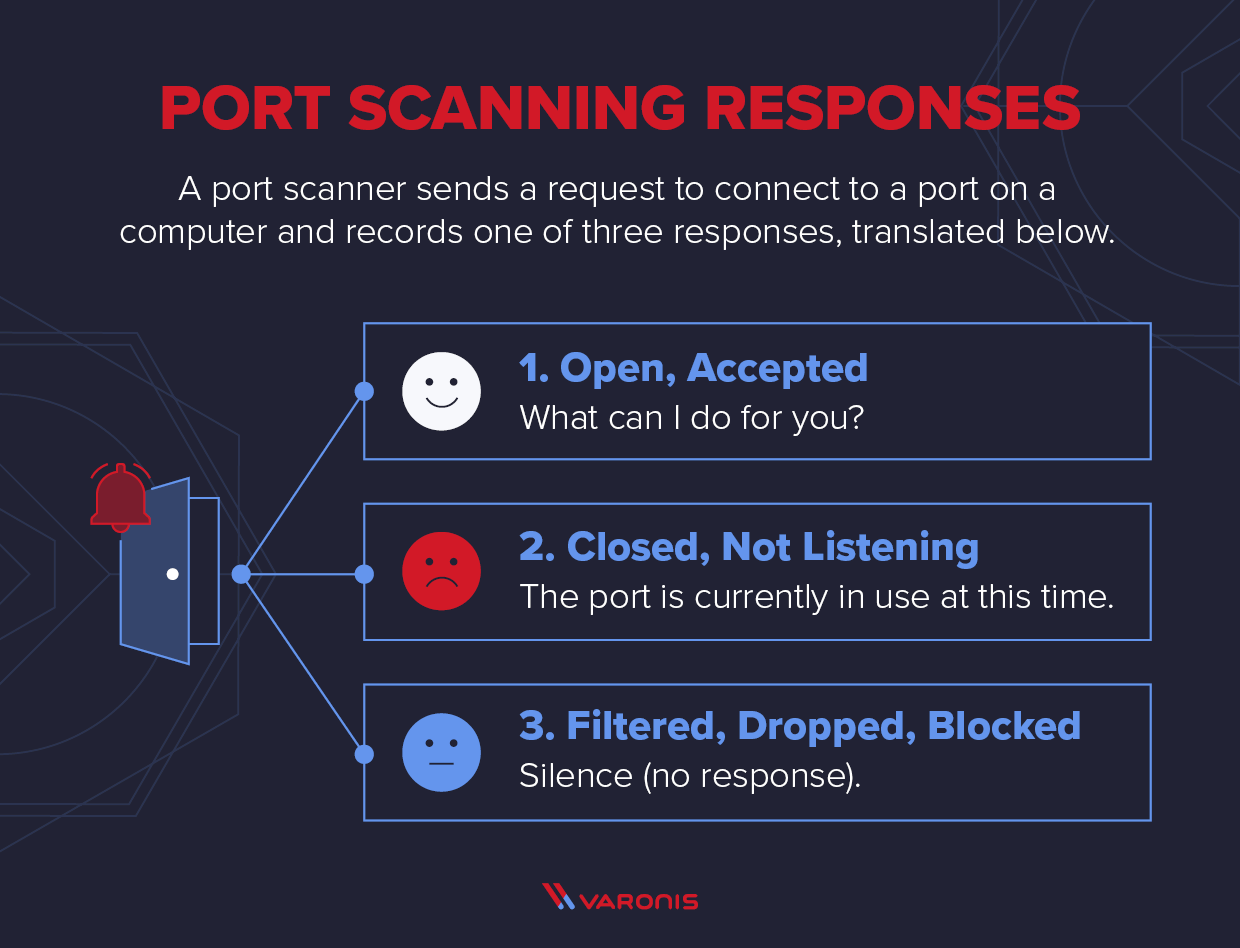
During a port scan, hackers send a message to each port, one at a time. The response they receive from each port determines whether it’s being used and reveals potential weaknesses. Security techs can routinely conduct port scanning for network inventory and to expose possible security vulnerabilities.
Can you get hacked through an open port?
Is port forwarding a security risk? If not setup properly, port forwarding and open ports can create an attack surface that are commonly used by hackers to gain access to systems. Keep your ports closed and don’t port forward!
What can an attacker do with open ports?
Attackers use open ports to find potential exploits. To run an exploit, the attacker needs to find a vulnerability. To find a vulnerability, the attacker needs to fingerprint all services that run on a machine, including what protocols it uses, which programs implement them, and ideally the versions of those programs.
What ports should never be open?
Ports 80, 443, 8080 and 8443 (HTTP and HTTPS) They’re especially vulnerable to cross-site scripting, SQL injections, cross-site request forgeries and DDoS attacks.
Is a port open if it is listening?
So, opening a port means making it available to the outside if an application is listening. If it isn’t, it will show as “closed” on nmap scans.
Can port 443 be hacked?
No. “Port 443” can not be hacked. Neither can any other port.
What are 3 reasons that hackers hack?
Some common reasons for hacking include basic bragging rights, curiosity, revenge, boredom, challenge, theft for financial gain, sabotage, vandalism, corporate espionage, blackmail, and extortion. Hackers are known to regularly cite these reasons to explain their behavior.
Should I close open ports?
If you have unnecessary router ports open, it could become a security or privacy risk, as hackers could be provided remote access. The best solution is to close unused ports via the router itself. Make sure your network is operating properly and that you set aside your router’s IP address, password, and network name.
What can be done with open port?
An open port is a network port that accepts traffic either using TCP or UDP and allows communication with underlying server technologies. Open ports are required when hosting remote services to which end-users can connect.
Is there danger in port forwarding?
Port forwarding usually means leaving a gap in your security. This can potentially be dangerous because hackers could also use this to penetrate your network. Consequently, there are some documented cases when an opened port was used as an attack vector.
Is an open port a vulnerability?
Vulnerabilities of open ports As mentioned at the outset, open ports provide a more extensive “attack surface” or opportunity for an attacker to find vulnerabilities, exploits, misconfigurations, and other risks due to the allowed network communication over a specific network port.
Can port 443 be hacked?
No. “Port 443” can not be hacked. Neither can any other port.
What can a hacker do with port 80?
– [Instructor] Hackers use ports to get in and attack a system and also to get out of a system without being noticed. Port 80 is a default port for HTTP. Several attacks use port 80 to gain access to backend services, and include buffer overflows, SQL injections, and cross-site scripting.
Is port 8080 a security risk?
Port 8080 and 8088 — HTTP Alternative Because these two ports are HTTP alternatives for web traffic, they inherently do not have encryption embedded during data communication. This makes all web traffic communicated over the network susceptible to being sniffed and intercepted by threat actors.
What are unsafe ports?
A port or berth will be unsafe if the ship is unable to reach the port safely. For example a port may be considered unsafe even if the ship suffers damage during its passage on a river or channel when approaching a port.
Is port scanning a threat?
Port scanning is a method attackers use to scope out their target environment by sending packets to specific ports on a host and using the responses to find vulnerabilities and understand which services, and service versions, are running on a host.
Can hackers see your screen?
Hackers can gain access to your computer monitor — a cybersecurity expert shows us how easy it is.
Can hackers see through your camera?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
What can a hacker do with port 80?
– [Instructor] Hackers use ports to get in and attack a system and also to get out of a system without being noticed. Port 80 is a default port for HTTP. Several attacks use port 80 to gain access to backend services, and include buffer overflows, SQL injections, and cross-site scripting.