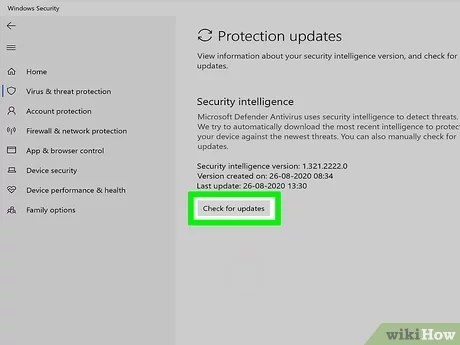
Your computer can be used to attack other computers. Sometimes hackers will take over a computer, sometimes thousands of them, to launch an attack on a website they’ve targeted.
What happens when a hacker get remote access to my computer?
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
Can hackers see your computer screen?
Researchers at DEF CON say computer monitors can be hacked to actively snoop on you, covertly steal data and even manipulate what you see on the screen. The list of ways we can be spied upon seems nearly endless, but you can add one more to that list: active screen snooping via your vulnerable monitor.
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Does shutting down computer stop hackers?
‘If hackers have made a connection but not yet managed to install software then yes, shutting down your computer will cut them off,’ says Darren. ‘However if a hacker has already managed to install remote access software, simply shutting down will not be enough. ‘
How can I tell if someone is connected to my computer?
Go to the control panel and click on “System and Security” and “Administrative Tools”. Then click “Event Viewer”. On the left side, an option “Security” will appear, click on it and wait for a window with all logon events to show.
Can hackers hear you?
We’ve been warned about hackers taking control of cameras on your computer screen, that is still a concern, but hackers are also listening to you via your smart devices. The device itself might not be recording your conversation, but a hacker could be.
Can hackers see through your camera?
Are hackers really spying on people through their phone cameras and webcams? The short answer: Yes. Webcams and phone cameras can be hacked, giving bad actors complete control over how they function. As a result, hackers can use a device’s camera to both spy on individuals and search for personal information.
Is someone spying on my computer?
To open the Activity Monitor, hit Command + Spacebar to open Spotlight Search. Then, type Activity Monitor and press Enter. Check over the list for anything you don’t recognize. To close out a program or process, double click, then hit Quit.
Can WIFI be hacked remotely?
You might be surprised how easy it is to hack into your home Wi‑Fi network nowadays. For very little money, a hacker can rent a cloud computer and most often guess your network’s password in minutes by brute force or using the powerful computer to try many combinations of your password.
Open task manager by right-clicking on the taskbar and choosing Task Manager. If there’s a suspicious process, that’s the monitoring app. Question: Can my company see what I do on my computer? Answer: Your company can see your device activities and track them if they provide you with that computer.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Can hackers see you through your phone camera?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Why do people cover their computer camera?
Cybercriminals can access these cameras, and because of their positions — facing your living room, kitchen, or office — they can expose your privacy and sensitive conversations. That’s why it’s a good idea to cover up your webcam or take other steps to improve your internet security.
Can someone see you through your phone camera?
Yes, you can be spied upon through the camera of your smartphone. There are several applications that can be found online that assist in spying on someone through their cell phone camera.
How do hackers know my password?
Another popular way to get hold of your passwords is via malware. Phishing emails are a prime vector for this kind of attack, although you might fall victim by clicking on a malicious advert online (malvertising), or even by visiting a compromised website (drive-by-download).
What can a hacker see on your phone?
Hackers can use keyloggers and other tracking software to capture your phone’s keystrokes and record what you type, such as search entries, login credentials, passwords, credit card details, and other sensitive information.
Can a hacker control my phone?
Skilled hackers can take over a hacked smartphone and do everything from making overseas phone calls, sending texts, and using your phone’s browser to shop on the Internet. Since they’re not paying your smartphone bill, they don’t care about exceeding your data limits.
Can someone spy on you through WIFI?
By just listening to existing Wi-Fi signals, someone will be able to see through the wall and detect whether there’s activity or where there’s a human, even without knowing the location of the devices. They can essentially do a monitoring surveillance of many locations. That’s very dangerous.”
What software prevents hackers?
Firewalls. A firewall is a software program or piece of hardware that blocks hackers from entering and using your computer. Hackers search the internet the way some telemarketers automatically dial random phone numbers.
What are remote access attacks?
What Does Remote Attack Mean? A remote attack is a malicious action that targets one or a network of computers. The remote attack does not affect the computer the attacker is using. Instead, the attacker will find vulnerable points in a computer or network’s security software to access the machine or system.
Should I be worried if someone has my IP address?
No, you shouldn’t worry if someone has your IP address. If someone has your IP address, they could send you spam or restrict your access to certain services. In extreme cases, a hacker might be able to impersonate you. However, all you need to do to fix the problem is change your IP address.