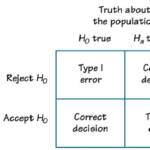
“IMessages between two Apple devices are considered encrypted communication and cannot be intercepted, regardless of the cell phone service provider,” the agency’s intelligence note.
Is iMessage really private?
Apple’s iMessage for iPhone, iPad, and Mac always uses end-to-end encryption. Only the sender and receiver of the messages can see their contents. Photos, videos, and other file attachments are also encrypted. What’s more, Apple’s FaceTime service also uses end-to-end encryption for voice and video calls, too.
Can iPhone messages be tracked?
Yes, it’s definitely possible for someone to spy on your text messages and it’s certainly something you should be aware of – this is a potential way for a hacker to gain a lot of private information about you – including accessing PIN codes sent by websites used to verify your identity (such as online banking).
Can iMessage be tracked by government?
According to the FBI’s “Lawful Access” guide, if served with a court order or a search warrant, Apple must hand over basic subscriber information as well as 25 days’ worth of data about queries made in iMessage, such as what a targeted user looked up in iMessage and also which other people searched for that targeted …
Can iMessages be tracked on phone bill?
Answer: A: No, iMessages don’t show on your bill. They are sent as data. You’ll see how much data you used over the month.
Can anybody see your iMessages?
Unless someone is still logged into your Apple ID on their device, they can’t read your iMessages or text messages. If you’re concerned, change your Apple ID password and disable iMessage on the other devices.
Can police read iMessages?
Law enforcement can retrieve messages via Google / iCloud backups. The chart shows that subpoenas will not grant access to message content for six of the nine secure messaging apps. The three that do give up “limited” content are iMessage, Line and WhatsApp.
Can police recover deleted iMessages?
Keeping Your Data Secure So, can police recover deleted pictures, texts, and files from a phone? The answer is yes—by using special tools, they can find data that hasn’t been overwritten yet. However, by using encryption methods, you can ensure your data is kept private, even after deletion.
Does Apple keep iMessage history?
The information is stored on the Apple servers, but it’s encrypted and therefore Apple cannot decrypt the data and turn it over pursuant to a legally authorized request.
Can text messages be traced by police?
Your text messages and phone calls can be intercepted, recorded and interfered with by the police using an ‘IMSI catcher’, a device deployed to track all mobile phones switched on and connected to the network in a specific area.
Can FBI read your iMessage?
Can governments spy on iMessage?
A recently discovered FBI training document shows that US law enforcement can gain limited access to the content of encrypted messages from secure messaging services like iMessage, Line, and WhatsApp, but not to messages sent via Signal, Telegram, Threema, Viber, WeChat, or Wickr.
Is iMessage more secure than WhatsApp?
Because it uses end-to-end encryption, WhatsApp is inherently the safer option than other messaging apps. Yes, that includes Facebook Messenger, Instagram Messages, Snapchat, and even regular old iMessage.
Can your phone carrier see your iMessages?
iMessages are DATA. Data that is encrypted. None of the carriers can track or read your iMessages.
Can iMessage be tracked through WiFi?
The initial contact for iMessage is initiated via normal SMS, and does not travel through the wifi network.
How long are iMessages saved?
For example, on an Apple device, you can choose to keep messages for 30 days, 1 year or forever.
Is iMessage more secure than SMS?
All Android devices use SMS messages, but this security issue affects iPhone and Android users alike, experts say. Although Apple’s iMessage system is more secure than SMS, iPhone owners must still deliver SMS messages to those who do not have Apple devices.
Can your ISP see your iMessages?
No. Your iMessages are secure, unless someone has your Apple ID and password, they won’t be able to read them. This means your ISP nor Apple can read your iMessages.
Are iMessages encrypted over WIFI?
iMessages are texts, photos, or videos that you send to another iPhone, iPad, iPod touch, or Mac over Wi-Fi or cellular-data networks. These messages are always encrypted and appear in blue text bubbles.
How do I make my iPhone messages private?
Open the Settings app and scroll down to and tap Messages. 6. Scroll down and turn on the toggle next to Filter Unknown Senders under the “MESSAGE FILTERING” heading.
Can iPhone iMessage be hacked?
Experts say that just receiving an iMessage from a hacker using this exploit can be enough to leave users’ personal data exposed. “It’s like being robbed by a ghost,” Hubbard wrote.
Can someone see what I’m doing on my iPhone?
If your iPhone backs everything up to your iCloud account, then someone can spy on your activity by accessing your iCloud account from any web browser. They would need your Apple ID username and password in order to do this, so if you know that a third party has that information, there are a few steps you should take.