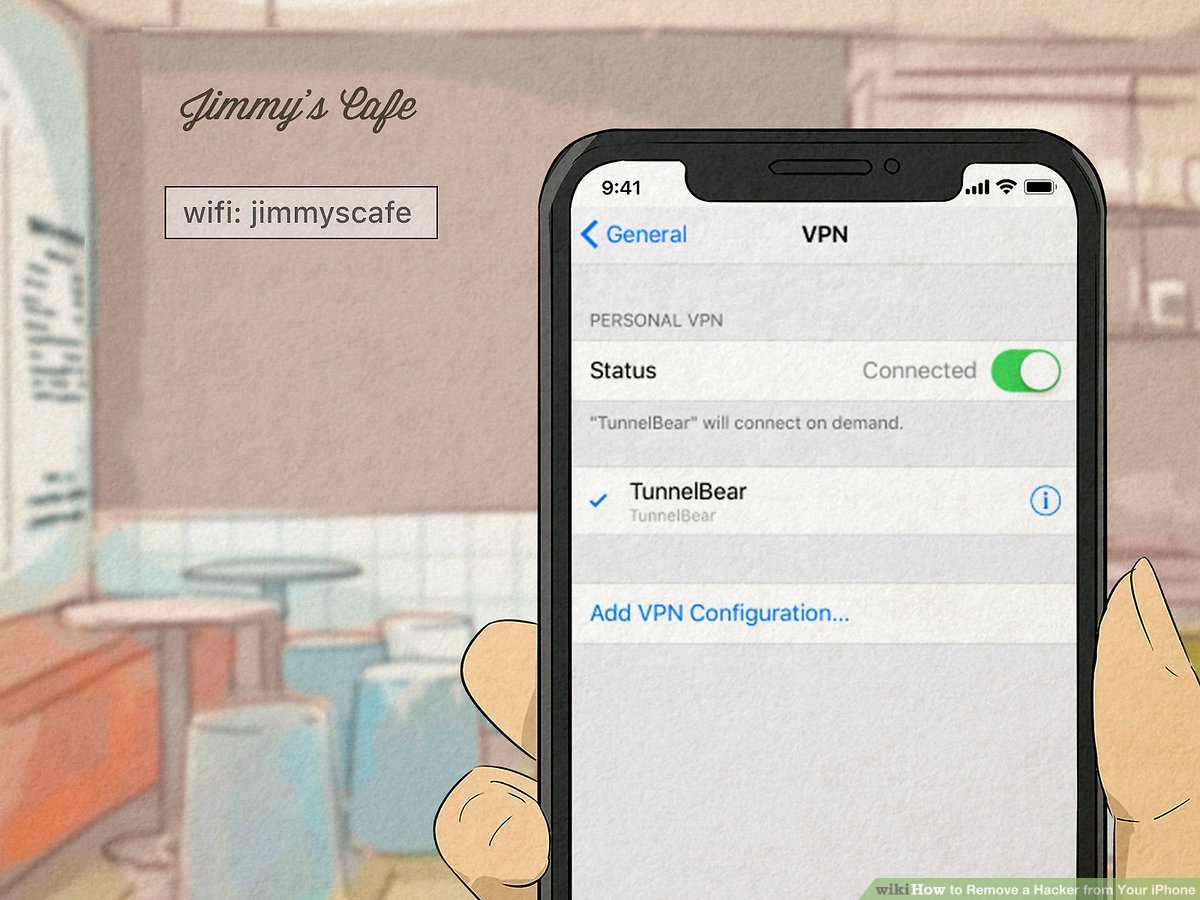
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device.
Does restarting your phone get rid of hackers?
With such a powerful tool at their disposal, Marczak said rebooting your phone won’t do much to stop determined hackers. Once you reboot, they could simply send another zero-click. “It’s sort of just a different model, it’s persistence through reinfection,” he said.
Can virus be removed by factory reset?
Disadvantages of Factory Resetting Not all malware and viruses can be removed by resetting a device to factory mode; that is, it cannot remove a few viruses or malware stored in the rooted partition of the device through this method.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
Will a factory reset remove spyware?
A factory reset will delete everything on your phone, including the spyware. Make sure you have a backup of your phone before you do this to prevent losing your photos, apps, and other data. You’ll need to restore your phone to a backup from before you started experiencing the spyware issues.
Should I factory reset my hacked phone?
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device. Follow the instructions below to reset your iPhone or Android.
Will getting a new phone stop a hacker?
Regularly rebooting phones won’t stop the army of cybercriminals or spy-for-hire firms that have sowed chaos and doubt about the ability to keep any information safe and private in our digital lives. But it can make even the most sophisticated hackers work harder to maintain access and steal data from a phone.
Does factory reset remove ransomware?
Like a lot of things in life, it depends. If a ransomware attack only targeted certain file types, such as Office files, a reset would eradicate those infected files and your machine would recover in a clean state.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.
How I know if my phone is hacked?
Poor performance: If your phone shows sluggish performance like crashing of apps, freezing of the screen and unexpected restarts, it is a sign of a hacked device. Unrecognised apps: If you notice any unrecognised applications downloaded on your device, it could be the work of a hacker.
Does spyware work if phone is off?
A device that is infected with malware or spyware can track your location even if your location settings are turned off.
Should I reset my iPhone if hacked?
If you suspect your iPhone has been hacked, you should reset your phone to its factory settings. What do you have to do to prevent another attack? Never connect to a free Wi-Fi Do not jailbreak your phone Delete any apps on your phone you do not recognize Do not download illegitimate apps, like the flashlight app.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.
How would I know if my phone has been compromised?
“The most common signs of a device being compromised are that the battery gets drained faster than usual, you experience spikes in your internet data usage although your browsing habits haven’t changed, your GPS feature or internet (either Wi-Fi or mobile data) can be enabled or disabled by itself, and random ad pop- …
Is my phone still hacked?
Signs Your Phone Has Been Hacked Your phone is running slower than usual. You notice strange activity on your online accounts, like unfamiliar logins, new account signups, or password reset emails. You see unfamiliar calls or texts. You get more pop-ups than usual; this could be a sign of adware.
What happens if my IP address is hacked?
But, if a hacker knows your IP address, they can use it to seize very valuable information, including your location and online identity. Using this information as a starting point, they could potentially hack your device, steal your identity, and more.
What does *# 21 do to your phone?
We rate the claim that dialing *#21# on an iPhone or Android device reveals if a phone has been tapped FALSE because it is not supported by our research.
What happens if a virus gets on your phone?
Phones can get a wide variety of viruses. Viruses on personal devices could delete your data, increase your phone bill, attempt to make unauthorized purchases, or gather private information and use it for malicious purposes —such as blackmailing or identity theft.
Will a factory reset remove malware Android?
The malware is on your recovery partition The recovery partition is part of the hard drive where your device’s factory settings are stored. In rare cases, this can become infected with malware. Hence, doing a factory reset will not clear the virus.
Will restoring remove malware?
No, since some malware can hide in files that System Restore does not modify. You need to scan your system with an offline scanner such as the ESET Sysrescue offline scanner.
Does formatting remove all viruses?
If your computer is infected with a virus, formatting or erasing the hard drive and starting over often removes any virus. However, if backups of your computer were made and backed up the virus, your computer can be re-infected if not protected by an antivirus program.
Is it possible to unlock ransomware?
Typically, without the cyber criminals’ interference – decryption is impossible (except for seriously flawed ransomware). Despite paying – victims often do not receive the promised decryption tools. Removing Unlock ransomware will prevent it from encrypting more data, but it will not restore already compromised files.