Restoring your system to its original factory settings will wipe out any back doors hackers established into your device. However, restoring your phone to a back-up where the back doors were already installed could preserve the hacker’s way into the device.If your iPhone was hacked, this will remove anything the hacker has installed that helps them keep access to your phone. When you restore from a backup, you’re also resetting your iPhone. This erases everything on your iPhone!
Can resetting iPhone remove hacker?
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device. Follow the instructions below to reset your iPhone or Android.
Should I reset my iPhone if hacked?
If you suspect your iPhone has been hacked, you should reset your phone to its factory settings. What do you have to do to prevent another attack? Never connect to a free Wi-Fi Do not jailbreak your phone Delete any apps on your phone you do not recognize Do not download illegitimate apps, like the flashlight app.
Will factory resetting an iPhone remove spyware?
Does a factory reset remove spyware? Restoring your iPhone to its factory settings will wipe it completely clean, removing spyware and other malware in the process.
Does resetting iPhone remove viruses?
In short, yes, a factory reset will usually remove viruses … but (there’s always a ‘but’ isn’t there?) not always. Due to the wide variety and ever-evolving nature of computer viruses, it’s impossible to say for sure that a factory reset will be the answer to curing your device from malware infection.
Should I reset my iPhone if hacked?
If you suspect your iPhone has been hacked, you should reset your phone to its factory settings. What do you have to do to prevent another attack? Never connect to a free Wi-Fi Do not jailbreak your phone Delete any apps on your phone you do not recognize Do not download illegitimate apps, like the flashlight app.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.
Does shutting down your phone get rid of hackers?
Turns out that shutting off a device still isn’t enough to stop the hackers anymore. A team of cybersecurity researchers at the Technical University of Darmstadt in Germany have discovered that iPhones can still be infected with malware when they’re powered down.
Can iPhone be hacked remotely?
It might surprise you, but yes, it is possible to remotely hack an iOS device. On the bright side; however, it will almost certainly never happen to you.
Can spyware stay on phone after factory reset?
Chances of malware surviving a factory reset are very, very small, but not zero. If you have rooted your phone, there is a small chance that malware can copy itself to the system partition, so it would survive a factory reset.
Can malware survive a factory reset?
Disadvantages of Factory Resetting Data that is deleted cannot be recovered if backup for it does not exist. Not all malware and viruses can be removed by resetting a device to factory mode; that is, it cannot remove a few viruses or malware stored in the rooted partition of the device through this method.
Will a factory reset get rid of spyware?
A factory reset will delete everything on your phone, including the spyware. Make sure you have a backup of your phone before you do this to prevent losing your photos, apps, and other data. You’ll need to restore your phone to a backup from before you started experiencing the spyware issues.
What happen when I reset all settings on iPhone?
Reset All Settings: All settings—including network settings, the keyboard dictionary, location settings, privacy settings, and Apple Pay cards—are removed or reset to their defaults. No data or media are deleted.
What does iPhone reset network do?
Resetting network settings on your Apple® iPhone® resets Wi-Fi networks and passwords, cellular settings, and VPN settings.
What can hackers do to my phone?
When a hacker gets into your phone, they will try to steal access to your valuable accounts. Check your social media and email for password reset prompts, unusual login locations or new account signup verifications. You notice unfamiliar calls or texts in your logs. Hackers may be tapping your phone with an SMS trojan.
Should I reset my iPhone if hacked?
If you suspect your iPhone has been hacked, you should reset your phone to its factory settings. What do you have to do to prevent another attack? Never connect to a free Wi-Fi Do not jailbreak your phone Delete any apps on your phone you do not recognize Do not download illegitimate apps, like the flashlight app.
What does *# 21 do to your phone?
We rate the claim that dialing *#21# on an iPhone or Android device reveals if a phone has been tapped FALSE because it is not supported by our research.
Can someone hack your phone just by knowing your number?
Two-factor authentication. It’s important to reiterate that it’s not possible for someone to just simply type your number into some shady software and click “HACK”. There is usually a process of tricking you into doing something as mentioned above.
Can your iPhone get hacked by clicking on a link?
Dangerous email. Enticing you to click on a link in a text messages or an email is a common avenue hackers use to steal your information or to install malware on your smartphone. This is called a phishing attack. The hacker’s goal is to infect your iPhone with malware and likely breach your data.
Can someone else access my iPhone?
If your iPhone backs everything up to your iCloud account, then someone can spy on your activity by accessing your iCloud account from any web browser. They would need your Apple ID username and password in order to do this, so if you know that a third party has that information, there are a few steps you should take.
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.
How to delete hacked iPhone completely?
Erase everything from the hacked iPhone. 1 Open the Settings app and tap General. 2 Tap Reset. 3 Select Erase All Content and Settings. 4 Enter your iPhone passcode when asked and confirm. 5 After reset, set up your iPhone, and any malicious data on it will be gone. You will practically have an internally new iPhone.
Does Restoring your iPhone make it more vulnerable to hackers?
Restoring your iPhone can be a quick fix for clearing any inroads that hackers have already made into your device. However, it will also make your device more vulnerable until you bring its security patches up to date. Restoring your system to its original factory settings will wipe out any back doors hackers established into your device.
How to protect your iPhone from hacking?
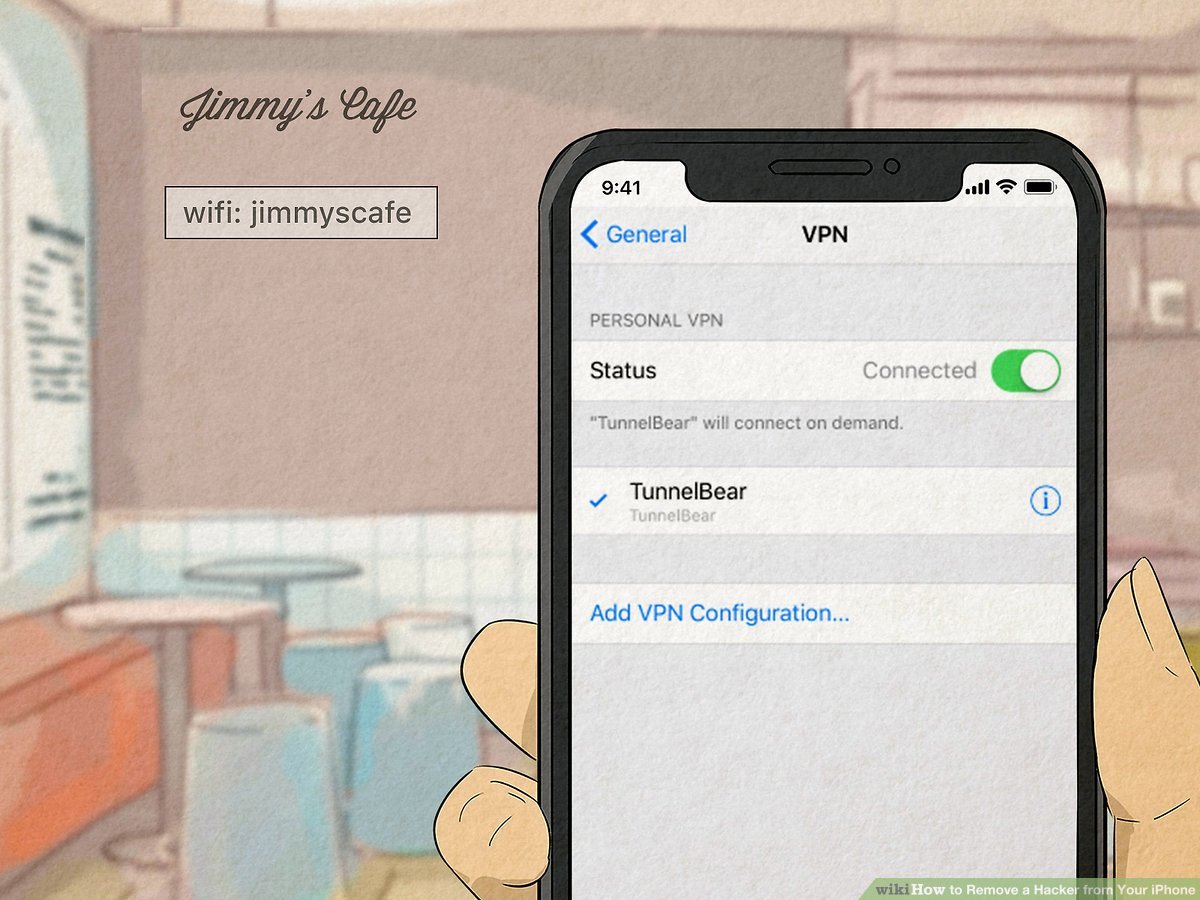
While there are many ways to protect your iPhone from hacking, one of the simplest is to be proactive about it. Ensure you have a strong password and that your phone is updated with the latest software patches. If you’re really concerned about security, consider using a VPN or other security measures.
Can hackers access your iPhone without your password?
If a hacker cracks your password on a website and it’s the same one you use for your Apple ID, they may be able to gain access to your iPhone. Use a VPN while using public Wi-Fi.