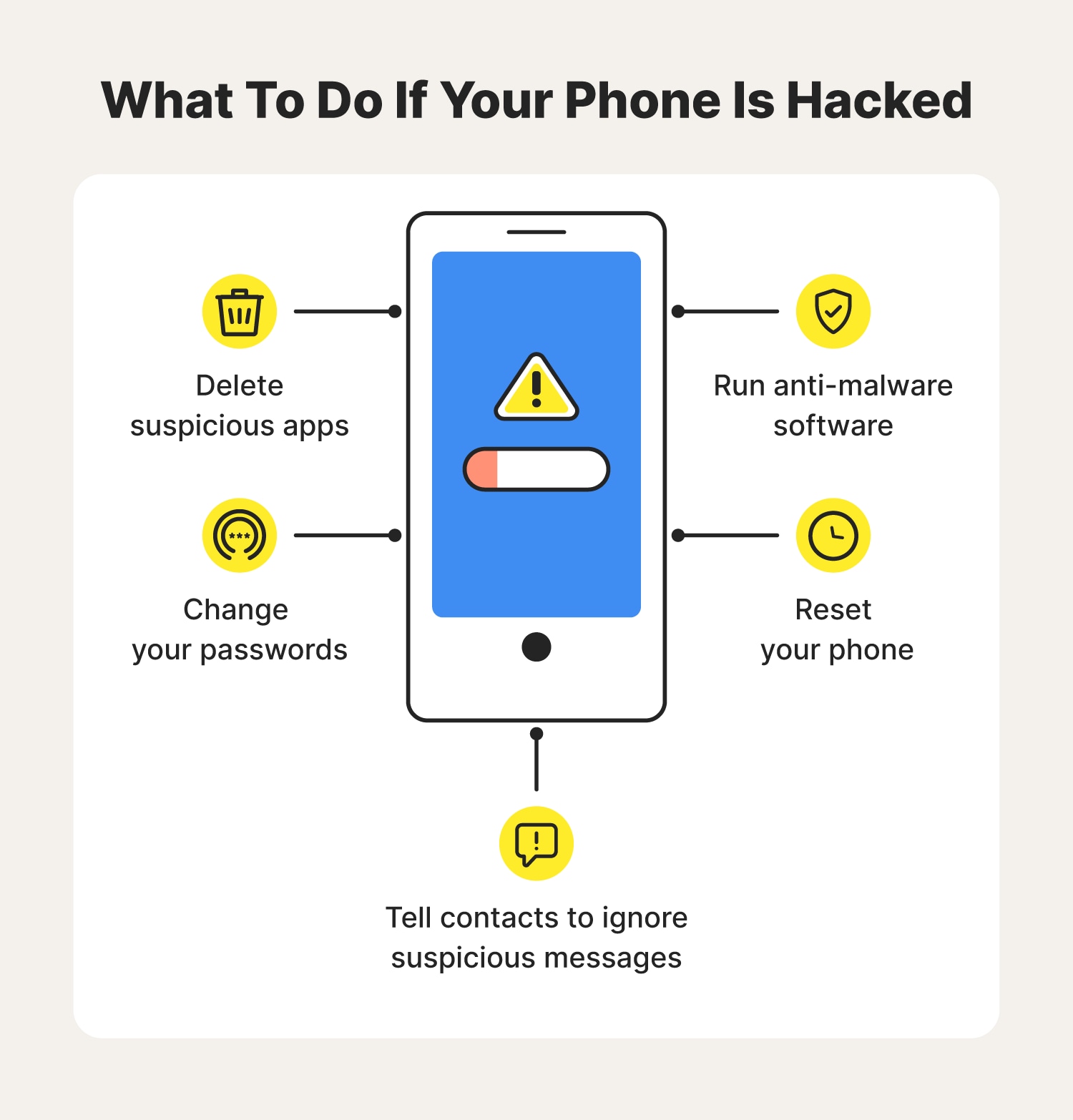
If you suspect your iPhone has been hacked, you should reset your phone to its factory settings. What do you have to do to prevent another attack? Never connect to a free Wi-Fi Do not jailbreak your phone Delete any apps on your phone you do not recognize Do not download illegitimate apps, like the flashlight app.
Does resetting iPhone get rid of hackers?
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device. Follow the instructions below to reset your iPhone or Android.
Will restarting my phone get rid of a hacker?
With such a powerful tool at their disposal, Marczak said rebooting your phone won’t do much to stop determined hackers. Once you reboot, they could simply send another zero-click. “It’s sort of just a different model, it’s persistence through reinfection,” he said.
Can Apple tell if iPhone is hacked?
If Apple detects evidence of a state-sponsored attack, the targeted user will get a Threat Notification on the top of the page when signed into appleid.apple.com. Apple will also send an email and iMessage notification to the account associated with the user’s Apple ID. Don’t expect this to work perfectly.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.
Can an iPhone be hacked by visiting a website?
Just like on your computer, your iPhone can be hacked by clicking on a suspicious website or link. If a website looks or feels “off” check the logos, the spelling, or the URL.
Can your iPhone get hacked by clicking on a link?
Dangerous email. Enticing you to click on a link in a text messages or an email is a common avenue hackers use to steal your information or to install malware on your smartphone. This is called a phishing attack. The hacker’s goal is to infect your iPhone with malware and likely breach your data.
What happen when I reset all settings on iPhone?
Reset All Settings: All settings—including network settings, the keyboard dictionary, location settings, privacy settings, and Apple Pay cards—are removed or reset to their defaults. No data or media are deleted.
What does iPhone reset network do?
Resetting network settings on your Apple® iPhone® resets Wi-Fi networks and passwords, cellular settings, and VPN settings.
What can hackers do to my phone?
When a hacker gets into your phone, they will try to steal access to your valuable accounts. Check your social media and email for password reset prompts, unusual login locations or new account signup verifications. You notice unfamiliar calls or texts in your logs. Hackers may be tapping your phone with an SMS trojan.
What does *# 21 do to your phone?
We rate the claim that dialing *#21# on an iPhone or Android device reveals if a phone has been tapped FALSE because it is not supported by our research.
What is the code to check if your iPhone is hacked?
Dial *#21# and find out if your phone has been hacked this way. If you see that it was, just dial ##21# to erase these settings. No need to memorize all these codes and phone tap numbers when you’re using Clario.
Can you tell if your phone is being monitored?
Yes, there are signs that will tell you when your phone is being monitored. These signs include overheating of your device, the battery draining fast, receiving odd text messages, hearing weird sounds during calls, and random reboots of your phone.vor 4 Tagen
What if I accidentally clicked on a suspicious link on my phone?
Review where a phishing link redirected your Android phone, noting the site address or any files downloaded. Do not interact with the suspect webpage. Delete any downloaded files. Scan the device for malware using a trusted app.
Is iCloud safe from hackers?
iCloud is Extremely Secure “Data stored in the iCloud is encrypted so a hacker needs a key to access it. Meaning to say: this storage system is extremely secured.” With that said, this doesn’t mean iCloud is 100 percent secure all of the time. Problems can arise because of the behavior of iPhone users.
How can I see who tried to log into my Apple ID?
Sign in to the Apple ID website (https://appleid.apple.com) and review all the personal and security information in your account to see if there is any information that someone else has added. If you have two-factor authentication turned on, review trusted devices for any devices that you don’t recognize.
When should I reset my iPhone?
There are several reasons you may want to reset your iPhone. Most commonly, people reset their iPhone because they are experiencing major software errors, like issues connecting to networks or apps crashing. Resetting the phone to its factory settings should resolve these errors and restore normal functioning.
Does reset all settings remove Apple ID?
No, once you “Erase all content and settings” your iPhone is basically back to factory settings and the new owner will not be able to sync with or sign in to your iCloud account.
Does resetting settings delete passwords?
A network settings reset will not delete any files, folders, or other media stored on your device. Nor will it delete any web browser data, such as your browsing history or saved bookmarks. Here’s what a network settings reset deletes: Wi-Fi network names and passwords.
Can your iPhone get hacked by clicking on a link?
2. Avoid clicking suspicious links. Just like on your computer, your iPhone can be hacked by clicking on a suspicious website or link. If a website looks or feels “off” check the logos, the spelling, or the URL.
What if I accidentally clicked on a suspicious link on my iPhone?
Disconnect from the internet immediately. This is to isolate your machine from infecting other devices and to cut off access to your machine from the hacker. This may help contain the malware infection. If you are on a wired connection, unplug. If you are on a Wi-Fi connection, disconnect from the Wi-fi in settings.
How to fix an iPhone that has been hacked?
1 How can an iPhone be hacked? 2 Has your iPhone been hacked? Here’s how to check 3 4 Ways to fix a hacked iPhone Turn off the internet Delete any unrecognized apps Reset iPhone All Settings Erase everything from the hacked iPhone 4 How to keep your iPhone and its data safe
Is it safe to restore a hacked phone?
If you believe it’s been hacked, do NOT restore it. Take it to the police, talk to the prosecutor, and have their forensics team look at it. If you ONLY want to be safe, you can try and restore it. That should take care of any spyware installed, but it may brick the phone as it may not be possible to return a hacked phone to a pristine state.
Can your phone get hacked if you jailbreak it?
You will face a higher risk of getting hacked if your device is jailbroken, however. After removing any suspicious apps, use your security suite to scan your entire device for any remaining malicious software. There’s another method that you can try: a full-on factory reset.
What happens if my Apple ID is hacked?
If your Apple ID has been hacked, it means someone has gained access to all your personal information. They could potentially delete all your data, make purchases in your name, or even access sensitive information like your financial records. To secure your Apple ID, go to the Apple ID Account Page .