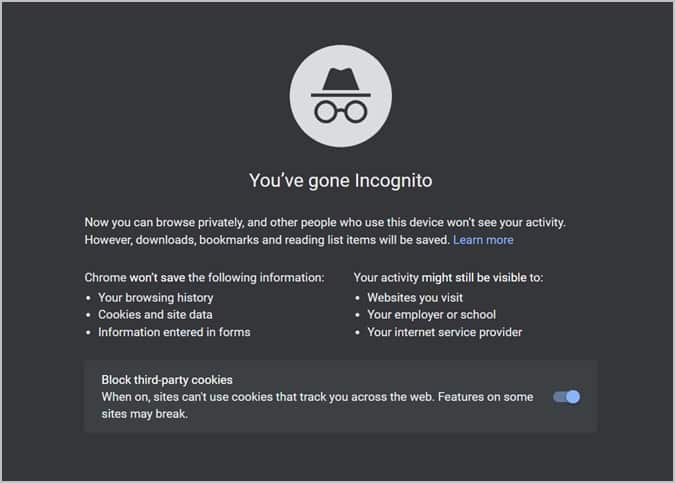
In Incognito, none of your browsing history, cookies and site data, or information entered in forms are saved on your device. This means your activity doesn’t show up in your Chrome browser history, so people who also use your device won’t see your activity.
What does used Chrome mean in my activity?
Can you track Chrome Incognito history?
Incognito mode doesn’t prevent web tracking Your incognito history can still be seen by your ISP, and the websites you visit can still track you. Incognito mode does not mean you’re browsing anonymously.
What does used Google Chrome fast and secure mean?
It keeps your phone safe by showing warnings to you when you attempt to navigate to dangerous sites or download dangerous files. Fast downloads and view web pages and videos offline Chrome has a dedicated download button, so you can easily download videos, pictures, and entire webpages with just one tap.
How can I see deleted Google activity?
Scan the android phone to locate the browsing history that was lost. You can also filter the results using the correct file types. Now preview and recover the browsing history on the android phone. Turn on ‘Displayed deleted items’ options to list out only the deleted file.
How can I tell if someone is using incognito mode?
The easiest way to track general usage of private browsing mode without a browsing history is to first clear your current browsing history. If a user navigates to a website in a browser in private browsing mode, the activity won’t appear in the browser’s history list.
What does the incognito icon look like?
The new Incognito window can be recognized by the dark background and the stylized “spy” icon just to the left of the three-dots menu. Chrome also reminds users of just what Incognito does and doesn’t do each time a new window is opened.
Where is incognito history stored?
Chrome won’t store the files you download while browsing in private. But, they’re still saved to your Downloads folder, even after you exit Incognito. You and anyone who uses your device can see and open the files.
Can you see incognito history on WIFI?
Nope. When you use incognito mode, your device and browser don’t keep a log of the sites you’re visiting. Yet, the Wi-Fi router can still log that information and the network admin can always retrieve that information later.
What does Chrome mean on my phone?
Google Chrome is a pre-installed browser on Android Phones. It’s one of the best browsers for Android and also the most used browser across the world. It is loaded with multiple features that make internet browsing super easy and seamless when switching between devices.
What’s the difference between Chrome and Google Chrome?
Google Chrome is a product of Google that has physical products that are made with the web browser in mind. Over their decades in business, Google has managed to create a massive line of products for Google and Google Chrome. Google Chrome is simply a branch of all of Google’s products and services.
What does used phone mean in Google activity?
It means you used the phone.
Is Google device activity accurate?
“Other Google activity” And it’s just about 100% accurate. If you’re feeling creeped out right now, don’t worry — there are a few steps you can take to hide your movement from Google. Turn off the Google Location Services on your Android device: This is the simplest solution to being tracked by Google.
Does deleting my activity delete everything?
Your activity might be stored in your browser, even if you delete it from My Activity. Learn how to delete browsing history and other browsing data from Chrome. If you use another browser, check its instructions for how to delete this info.
What is Google activity history?
Data helps make Google services more useful for you. Sign in to review and manage your activity, including things you’ve searched for, websites you’ve visited, and videos you’ve watched.
Can browsing history be recovered once it is deleted?
Even though the folder is gone from the direct view of unwanted people, but the documents still exist and can easily be found with a bit of extra effort. In technical terms, your deleted browsing history can be recovered by unauthorized parties, even after you cleared them.
How can I track my husbands internet activity?
mSpy app is a monitoring toole for all devices. The app can also lets you easily track your husband’s suspicious activities. With the app, you can simply get details about his location, receive and read all his text, Snapchat, WhatApp, Facebook, and Skype messages.
What is secret mode on Android?
Incognito mode on Android devices is just that; it’s a way to hide as you travel the web. As realized in Google Chrome on Android, Incognito mode hides your browsing history so others can’t see the websites you’ve visited. In effect, it masks your footprints across the web.
What is disadvantage of incognito mode?
Cons of incognito mode While browsing incognito, unless you take additional steps to encrypt your data and internet connection, your IP address remains visible and other people on your network can see your online activity.
Can someone see my browsing history from another computer?
The answer is yes. As long as you’re connected to a network that’s under your boss’s control, he or she can see nearly everything you do, the same as any other network administrator could.
Why is Incognito mode showing up?
Your online privacy is not impacted in any way. Basically, incognito mode just means that the browser doesn’t save cookies, temporary internet files or your browsing history when you are in incognito mode. The main thing it does is hide your browsing history from other people who use the same computer.
Does incognito hide your IP address?
Basically, Incognito mode hides your browsing activity from other users on your device. But Incognito mode doesn’t hide your info from websites, advertisers, your internet service provider (ISP), or Big Tech companies. Even in incognito, Google and others can still track you. Incognito does not hide your IP address.
What is incognito mode on Google Chrome?
Incognito Mode or “private browsing” is a privacy feature on Google Chrome that actually disables the browsing history of the browser. This privacy mode allows people to browse the Web without storing local data that could potentially be retrieved at a later date.
Who can see my browsing history in incognito mode?
When you browse privately, no one else who uses your computer can see your activity. Bookmarks and downloads are saved, however. While you are in Incognito Mode, Chrome does not save: Browsing incognito does not make you anonymous on the internet. It merely means your browsing session is sanitized on your own computer.
How do I open an incognito window on my computer?
When the drop-down menu appears, choose New Incognito Window . To launch incognito mode using a keyboard shortcut, press Ctrl+Shift+N on Chrome OS, Linux, and Windows, or press Cmd+Shift+N on Mac OS X or macOS. You can also open a new incognito window with the File menu on a Macintosh.
What happens if you shop in incognito mode without an account?
For example, you may use Incognito mode to shop online for a birthday gift for a family member who shares your device. If you don’t sign in to your Google account, your shopping activity will not appear in your Chrome browsing activity and won’t be saved to your Google Account.