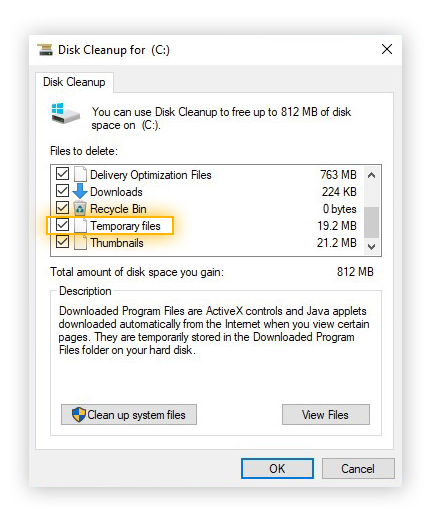
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
How can I find a hidden virus on my laptop?
Open your Windows Security settings. Select Virus & threat protection > Scan options. Select Windows Defender Offline scan, and then select Scan now.
Can computer viruses be invisible?
Removing a computer virus from a PC Computer viruses are almost always invisible. Without anti-virus protection, you may not know you have one. This is why it is vital to install anti-virus protection on all your devices.
How can I find hidden malware?
1. Download and install anti-virus software. You can use free solutions like Avast or Avira, or try a paid tool such as Kaspersky or ESET. Conduct a system scan with your anti-virus to spot infections.
Can computer viruses be invisible?
Removing a computer virus from a PC Computer viruses are almost always invisible. Without anti-virus protection, you may not know you have one. This is why it is vital to install anti-virus protection on all your devices.
What is hidden virus?
Hidden Viruses: Other viruses do not immediately become active. Instead, they “hide” for a while. After a hidden virus enters a host cell, its genetic material becomes part of the cell’s genetic material. The virus does not appear to affect the cell’s functions and may stay in this inactive state for years.
Does resetting a PC remove virus?
Running a factory reset, also referred to as a Windows Reset or reformat and reinstall, will destroy all data stored on the computer’s hard drive and all but the most complex viruses with it. Viruses can’t damage the computer itself and factory resets clear out where viruses hide.
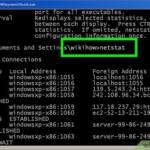
How do you check if u have a virus?
Open the Play Store app, tap your icon or avatar on the top right, and activate Play Protect in the menu. Install anti-malware software. An antivirus app is the best way to automatically detect and remove malware from your Android phone while preventing future infections.
How do you fight a virus naturally?
Load up on water, soups, and warm broths. Adding ginger, pepper, and garlic to your soups will help your body fight the viruses. The allicin present in garlic has antibacterial, antifungal, and antiviral properties. Studies have shown that eating raw garlic every day can boost immunity against the virus.
How do viruses hide?
Until recently scientists believed that viruses acted independently. Now we know that up to 40 of them can form into vesicles, which are essentially membrane-bound packets or spheres. These membrane sacs act as a Trojan horse to pass through the body’s defenses.
How is malware installed?
Malware can get onto your device when you open or download attachments or files, or visit a scammy website. Your device might get infected with malware through: downloading free stuff like illegal downloads of popular movies, TV shows, or games. downloading content available on file-sharing sites.
Can Windows Defender remove Trojan?
Windows Defender comes packed with the Windows 10 update and offers top-notch antimalware protection to keep your device and data safe. Although, Windows Defender is not capable of handling all kinds of viruses, malware, trojan, and other security threats.
Does deleting an infected file remove the virus?
Deleting an infected file removes both the virus and the infected file from your computer. Unless the virus has already infected other files on your computer, deleting an infected file is the most effective way of removing the virus and ensuring that it does not spread to other files.
How do I unhide files and folders hidden by virus?
Navigate to my documents, organize, folder and search options and click the view tab. Under the Hidden files and folders, select the show hidden files, folders and drives. Uncheck the “hide extensions for known files” and “hide protected operating system files”.
How can I remove virus for free?
If your device is showing symptoms of a virus, Malwarebytes’ free virus scanner will scan your computer for viruses and remove them. It will perform a fast, free online scan for viruses and let you know if you’ve been infected. If you give your ok, it will then delete viruses and malware.
Can computer viruses be invisible?
Removing a computer virus from a PC Computer viruses are almost always invisible. Without anti-virus protection, you may not know you have one. This is why it is vital to install anti-virus protection on all your devices.
How can I find hidden malware?
1. Download and install anti-virus software. You can use free solutions like Avast or Avira, or try a paid tool such as Kaspersky or ESET. Conduct a system scan with your anti-virus to spot infections.
Can virus hide from antivirus?
Some sophisticated viruses hide when you turn on your computer (also known as booting up your computer), and even antivirus software like Avast, with its boot-time scan feature, can be prevented from seeing it.
Can malware be hidden in files?
Malware can hide in a looooong list of files. The file extensions below are potentially dangerous because they can contain code or execute arbitrary commands. No matter where these files come from, be wary of them and try to avoid clicking on them, unless you’re absolutely sure they’re safe.
Can someone hack your computer if its off?
In general, the answer is no, you cannot hack into a computer that’s been turned off. Unless two conditions are met, the PC cannot be restarted and hacked from outside, even if you leave it connected to the internet and to power.
How much is it to get a virus off your computer?
The average cost of a virus removal at a technology retailer like Best Buy or Staples ranges from $99 to $149, so it’s easy to see how the cost of dealing with a virus can quickly grow.
How do hackers take control of your computer?
Another common way that hackers use to gain control of your computers is by sending out Trojan Viruses disguised as email attachments. Hackers typically send out these messages to 1000s of users with enticing headings and an attachment which they are hoping you will open.