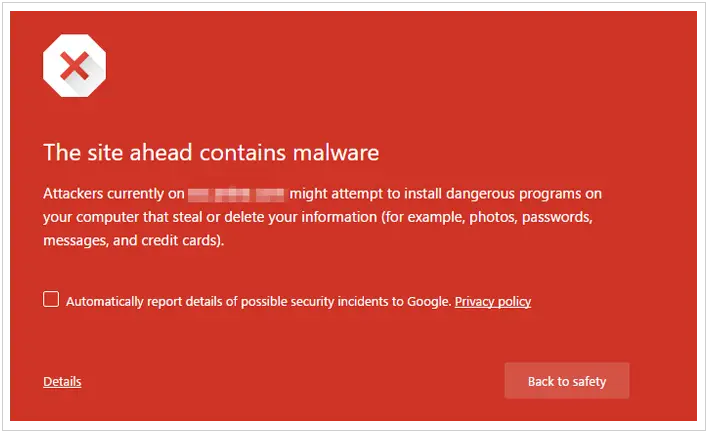
One of the most common symptoms of browser hijacking is discovering that your homepage has been reset. If your browser displays an unfamiliar website after launch, particularly one that is pornographic or advertising fake security software, this is almost definitely the work of a hijacker.
Can Chrome browser be hacked?
(NewsNation) — If you use Google Chrome as an internet browser, beware: Your information could be compromised. Google issued an alert warning billions of Chrome users that the browser has been successfully targeted by hackers.
Can my browser get hacked?
In most cases, browser hijacking is a crude – if deeply annoying – scam designed to redirect users to sites or ads where extra clicks generate revenue for the hackers. It can be dangerous, however, depending on the kind of malware involved.
Can my browser get hacked?
In most cases, browser hijacking is a crude – if deeply annoying – scam designed to redirect users to sites or ads where extra clicks generate revenue for the hackers. It can be dangerous, however, depending on the kind of malware involved.
How do you tell if Chrome has been hijacked?
The most obvious sign that your browser has been exploited is that your homepage is different from what it used to be or toolbars that you don’t recognize have appeared. You might also see new favorites or bookmarks just below the address bar or if you manually look through the bookmarks.
How safe is Google Chrome?
Google Chrome is by all accounts a secure browser, with features like Google Safe Browsing, which helps protect users by displaying an impossible-to-miss warning when they attempt to navigate to dangerous sites or download dangerous files. In fact, both Chrome and Firefox have rigorous security in place.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
Who is the No 1 hacker in world?
Kevin Mitnick is the world’s authority on hacking, social engineering, and security awareness training. In fact, the world’s most used computer-based end-user security awareness training suite bears his name. Kevin’s keynote presentations are one part magic show, one part education, and all parts entertaining.
What happens when you are hacked?
This can be really serious, hackers can use your identity details to open bank accounts, get credit cards, order products in your name, take over existing accounts and take out mobile phone contracts. Hackers could even get genuine documents such as passports and driving licenses in your name once they have stolen your …
How do I get rid of a browser hijacker?
How do I get rid of browser hijackers in Chrome? To remove browser hijackers in Chrome, remove any suspicious Google Chrome extensions. Then go to the Chrome settings and restore your browser to the default settings.
How do you tell if Chrome has been hijacked?
The most obvious sign that your browser has been exploited is that your homepage is different from what it used to be or toolbars that you don’t recognize have appeared. You might also see new favorites or bookmarks just below the address bar or if you manually look through the bookmarks.
Can my browser get hacked?
In most cases, browser hijacking is a crude – if deeply annoying – scam designed to redirect users to sites or ads where extra clicks generate revenue for the hackers. It can be dangerous, however, depending on the kind of malware involved.
How do you know if there is spyware on your computer?
The best way to check for spyware is by scanning the computer with anti malware software. The anti malware software deep scans the hard drive to detect and remove any threat lurking in the computer.
What is the most unsafe browser?
According to a study done by researchers at Trinity College, Yandex and Edge are the two worst browsers for security. The study also found that Edge sends users’ hardware ID, IP address, and location to back-end servers which over time can reveal your identity.
Which browser is more secure Safari or Chrome?
In fact, Safari beats Chrome on the Mac because it’s more energy-efficient, better at protecting your privacy, and it seamlessly works with the Apple ecosystem.
Will uninstalling Chrome remove malware?
After you uninstall and install Chrome again and log into your Google account, it will restore any settings, extensions, and potentially malware from the cloud backup. So if resetting browser settings and removing extensions didn’t help, reinstalling Chrome won’t remove malware either.
Which browser should I use?
Google Chrome: The best for Mac. Opera Mini: The best for mobile. Vivaldi: The fastest web browser. Tor: The most secure web browser.
Which browser is safe for online banking?
The Edge browser in Windows 10 is a new sandboxed app, so it’s much better for banking than Internet Explorer. Otherwise, Chrome is the most secure alternative, because it runs in Google’s own strong sandbox. Some security companies also provide add-ons, such as Kaspersky Safe Money and Bitdefender Safepay.
Should I use Chrome or Google?
Those who are looking to find out information based on keywords or phrases will want to just use the Google search bar, but those who are looking to have multiple tabs open or are looking for a particular website will want to choose Google Chrome.
Does changing password stop hackers?
Yes, changing your password will prevent hackers from accessing your account. Updating your account password at the first sign of an attack limits damage. Changing your password regularly also improves security. Stolen credentials in data breaches are often old.
Should I delete my email if it was hacked?
If you have been hacked several times and your email provider isn’t mitigating the amount of spam you are receiving, then consider starting afresh but don’t delete your email address! Many experts do warn against deleting email accounts as most email providers will recycle your old email address.