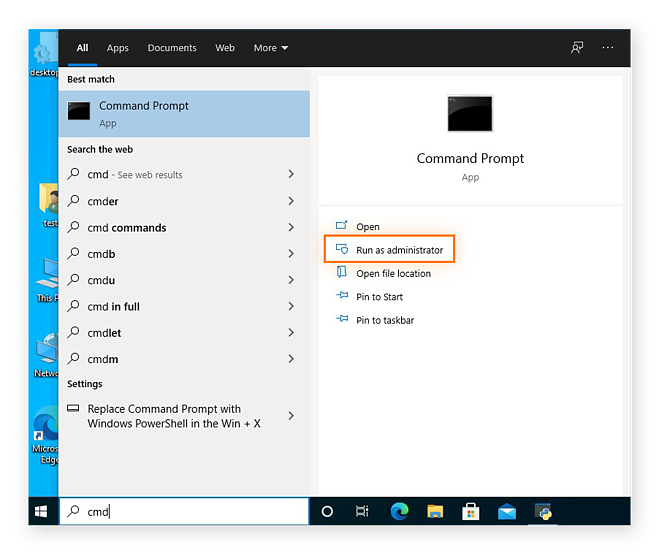
To view your incognito browsing history, you can use tools like the DNS cache or third-party software to recover your private browsing data. While there’s no straightforward way to see the sites you visited incognito — like viewing your history in your browser — the DNS cache is a good place to start.
Can I see my incognito history?
To view your incognito browsing history, you can use tools like the DNS cache or third-party software to recover your private browsing data. While there’s no straightforward way to see the sites you visited incognito — like viewing your history in your browser — the DNS cache is a good place to start.
Where are incognito files stored?
Chrome won’t store the files you download while browsing in private. But, they’re still saved to your Downloads folder, even after you exit Incognito. You and anyone who uses your device can see and open the files.
Does incognito delete history?
Many people think that using incognito mode, they’re hiding their activity from would-be trackers. But incognito mode only deletes information from your device when you close the app. It doesn’t stop websites, employers, and others from tracking your activity.
Can my parents see my incognito history on Wi-Fi?
Nope. When you use incognito mode, your device and browser don’t keep a log of the sites you’re visiting. Yet, the Wi-Fi router can still log that information and the network admin can always retrieve that information later.
Does incognito hide history from Wi-Fi?
Incognito mode can hide your browsing history from a particular device, but it’s not perfect. The wireless router still logs it, and the information can remain on your computer.
What is disadvantage of incognito mode?
Cons of incognito mode While browsing incognito, unless you take additional steps to encrypt your data and internet connection, your IP address remains visible and other people on your network can see your online activity.
Can my parents see my incognito history on WIFI?
Nope. When you use incognito mode, your device and browser don’t keep a log of the sites you’re visiting. Yet, the Wi-Fi router can still log that information and the network admin can always retrieve that information later.
What is disadvantage of incognito mode?
Cons of incognito mode While browsing incognito, unless you take additional steps to encrypt your data and internet connection, your IP address remains visible and other people on your network can see your online activity.
Who can see my mobile data history?
Who can see my mobile data history? Your mobile data history is accessible to your mobile service provider. They can see when and how much data you use, as well as your general location (based on which cell tower you’re connected to).
How can I see my child’s Incognito history?
The only easy way to view private browsing history on a phone is to use third-party software like mSpy. Such apps will offer an incognito history tracker feature and let you track private browsing.
What is better than incognito?
A VPN is better than incognito mode because it encrypts all of your web activity data and device IP address from everyone except the VPN provider itself, including your internet service provider (ISP).
How can you tell if someone is Incognito mode?
The easiest way to track general usage of private browsing mode without a browsing history is to first clear your current browsing history. If a user navigates to a website in a browser in private browsing mode, the activity won’t appear in the browser’s history list.
What is Incognito mode good for?
Private browsing (aka incognito mode) is a great way to prevent your web browser from saving what you do. But to call it privacy-focused is a stretch, and while your browser or device doesn’t log your movements in its history and cookies, that doesn’t mean the sites you visit don’t clock your behavior.
How can I see my child’s Incognito history?
The only easy way to view private browsing history on a phone is to use third-party software like mSpy. Such apps will offer an incognito history tracker feature and let you track private browsing.
What is better than incognito?
A VPN is better than incognito mode because it encrypts all of your web activity data and device IP address from everyone except the VPN provider itself, including your internet service provider (ISP).
Is incognito really private?
Incognito or private mode will keep your local browsing private, but it won’t stop your ISP, school, or employer from seeing where you’ve been online. In fact, your ISP has access to all your browsing activity pretty much no matter what you do. You can, however, use a Virtual Private Network (VPN) service.
How can you tell if someone is Incognito mode?
The easiest way to track general usage of private browsing mode without a browsing history is to first clear your current browsing history. If a user navigates to a website in a browser in private browsing mode, the activity won’t appear in the browser’s history list.
Can you see what someone googles on your Wi-Fi?
Well, the short answer to the question is yes. Almost every Wi-Fi router keeps logs of the websites the connected devices are visiting. Only the Wi-Fi owner has the permission to check out the logs of the Wi-Fi router to understand which connected user visited which websites.
Can you tell if your phone is being monitored?
If someone is spying on your phone, you may see your device’s data usage increase, your phone may unexpectedly reboot or show signs of slowing down. You may also notice activity, such as your device’s screen lighting up when it is in standby mode. You may also notice your device’s battery life suddenly decreasing.
Who can see my incognito searches?
Your online privacy is not impacted in any way. Basically, incognito mode just means that the browser doesn’t save cookies, temporary internet files or your browsing history when you are in incognito mode. The main thing it does is hide your browsing history from other people who use the same computer.
Which browser has no history?
With the DuckDuckGo browser, your browsing history never leaves your device. Deleting your entire browsing history is as easy as tapping a single button. It automatically blocks ads, stops third-party trackers, and ensures HTTPS encryption on all sites where that’s possible.