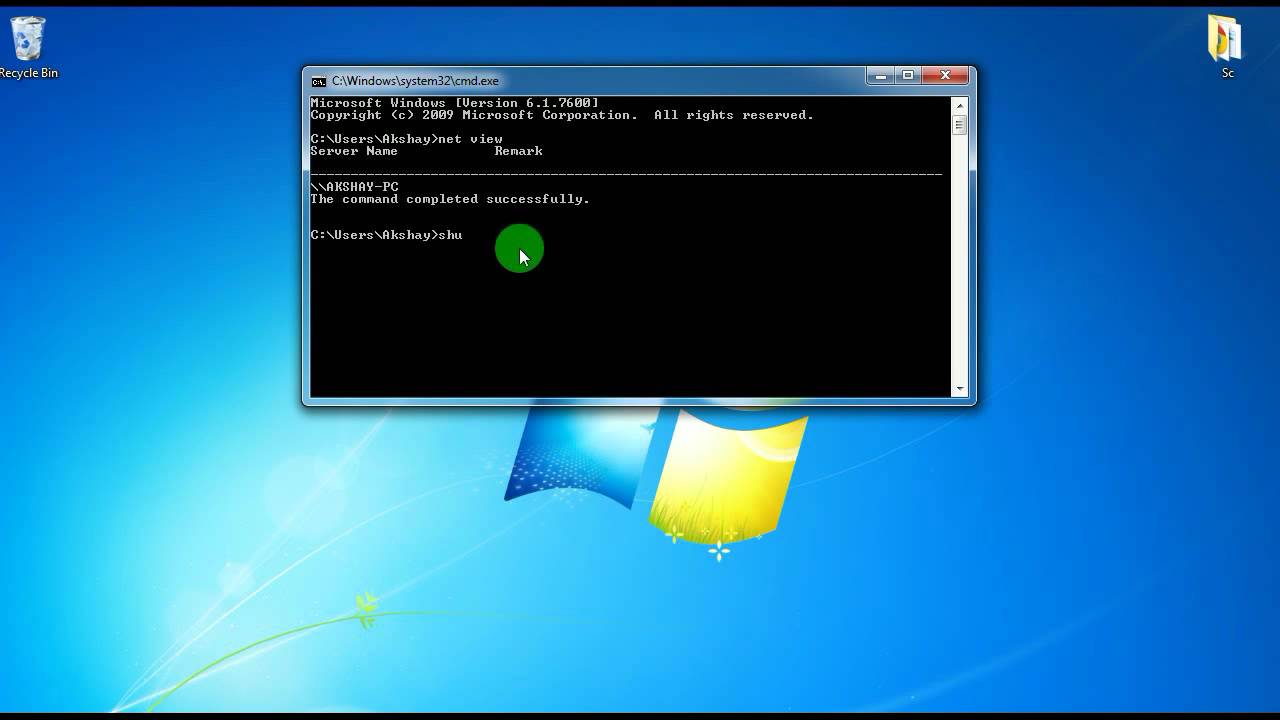
Type this one space after “shutdown” on the same line. Replace “computername” with the actual name of the target computer. Type /s or /r one space after the computer name. If you want to shut down the target computer type “/s” one space after the computer name.
How do I shutdown someone else’s computer?
Type this one space after “shutdown” on the same line. Replace “computername” with the actual name of the target computer. Type /s or /r one space after the computer name. If you want to shut down the target computer type “/s” one space after the computer name.
Can someone remotely shut down your computer?
If you have multiple computers on your network, you can shut them down remotely regardless of their operating system. If you are using Windows, you’ll need to set the remote computer to be able to shut down remotely. Once this is set up, you can perform the shut down from any computer, including Linux.
How do I shutdown an IP address?
To do this click “start”, then “run” then type command prompt. In the command prompt type “tracert website” (example tracrt Google.com) then hit enter. Various IP addresses should be returned. Then in the command prompt type “shutdown-i” and hit enter, this opens the remote shutdown dialogue.
How can I shutdown another computer using command prompt IP address denied?
From CMD you can type “runas /U:UserNameGoesHere CMD” and enter the password when prompted. Then try the command from the newly presented CMD Box. I am using this solution on a home Workgroup network. Solution works for shutdown.exe and psshutdown.exe It works for Windows 8 and should work for Windows 7.
How do I shutdown someone else’s computer?
Type this one space after “shutdown” on the same line. Replace “computername” with the actual name of the target computer. Type /s or /r one space after the computer name. If you want to shut down the target computer type “/s” one space after the computer name.
How do you shutdown all computers on a network using cmd?
Shut down machines remotely from any computer on the network by clicking the Start button in the lower-left corner of your screen, selecting “All Programs,” “Accessories” and then “Command Prompt.” Type “shutdown /i” (without the quotes) and press “Enter” to open the remote shutdown dialog box.
How can I remotely access another computer using cmd?
Type “mstsc /console /v:computername” into Command Prompt, with the specific computer name you wrote down earlier in place of “computername.” This entry takes you straight to the login screen for your remote computer. After you log on, you can use the remote machine as if it is the one you’re sitting infront of.
Can a laptop be shut down remotely?
Open up the Shutdown Start Remote server on your PC (no need to install it) and then open up the app on your Android phone. If both devices are connected to the same network, then you should see your PC name in the Shutdown Start Remote app interface. Tap on it to connect to your PC.
Can someone remotely access my computer without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
Can someone hack my computer remotely?
Yes, it’s absolutely possible for your home network to get hacked. There are a couple of ways hackers can gain access to your network. One common method is to guess the password. It sounds simple, but routers often come with a preset default password that the manufacturer uses for all devices.
How do I find out someone’s IP address?
Use an IP lookup tool Starting with the simplest way to find someone’s IP address is to use one of the many IP lookup tools available online. Resources such as WhatIsMyIPAddress.com or WhatIsMyIP.com offer tools to enter an IP address and search for its free public registry results.
What is PsShutdown?
How do I turn off computer without power button?
An oldie but goodie, pressing Alt-F4 brings up a Windows shut-down menu, with the shut-down option already selected by default. (You can click the pull-down menu for other options, like Switch User and Hibernate.) Then just press Enter and you’re done.
How do I shutdown someone else’s computer?
Type this one space after “shutdown” on the same line. Replace “computername” with the actual name of the target computer. Type /s or /r one space after the computer name. If you want to shut down the target computer type “/s” one space after the computer name.
What is the command for shutdown in CMD?
shutdown /s command will shut down the system you are working on. shutdown / i from the command prompt will open the Remote Shutdown Dialog window, this will provide options available via an easy to use interface including networked systems.
Can you shut down laptop from iPhone?
If you have the Remote Off/Off Remote apps running on both your devices, your iPhone will find your computer in the ‘Visible Computers’ section to the left. Select your computer. You should see these commands: Shut Down, Lock, Restart, Sleep, Hibernate. Choose one.
What is remote shutdown dialog?
Remote Shutdown Using Shutdown Dialog Box Step 3: The remote shutdown dialog box appears as shown in the below screenshot. Select the Add or Browse button to add the computers on the local network you want to shut down or restart remotely.
What is one way hackers can trick you into transmitting?
What is one way hackers can trick you into transmitting personal data over on a public network without your knowledge? They disguise the network as an evil twin.
Can someone spy on you through Wi-Fi?
By just listening to existing Wi-Fi signals, someone will be able to see through the wall and detect whether there’s activity or where there’s a human, even without knowing the location of the devices. They can essentially do a monitoring surveillance of many locations. That’s very dangerous.”
Can you be hacked while offline?
These attacks demonstrate that it is possible to hack an offline PC, even if you don’t have physical access. However, although technically feasible, these attacks aren’t straightforward. Most of these methods require a particular setup or optimal conditions.
Can remote desktop connection be used to spy?
Yes, it could be used in a subversive way however that is not the intent of the program. Additionally unless it already setup not to show any indication it’s running and a connection is established prior to a user sitting down at that computer I doubt it would go unnoticed.