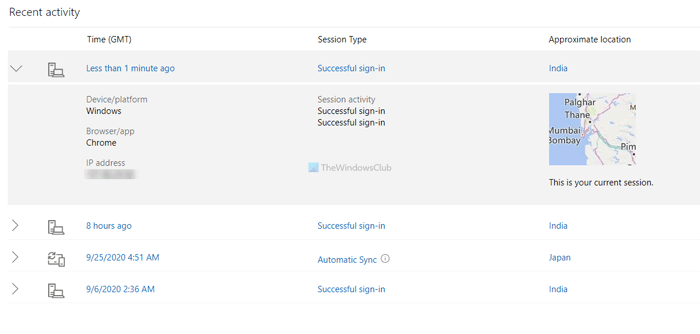
If you get an email about unusual activity on your Microsoft account, or if you’re worried that someone else might have used your account, go to the Recent activity page. You’ll see when your Microsoft account was signed in during the last 30 days, along with any device or app-specific info.
Can someone read my emails without me knowing?
Can someone read my emails without me knowing? Anyone with access to your device with your mailing account logged in can read your emails without you knowing. An intruder may open and read your email and mark them unread. They can also delete your emails after reading them.
Is my Outlook being monitored?
Checking email snooping To check in Outlook, the most commonly used email client, go to Tools, Email Accounts, and click Change or Properties. You’ll then see whether the POP and SMTP server is a local or proxy server. It it’s a proxy server, the email is being monitored.
Can someone hack my Outlook account?
Signs of Hacking One sign that your Outlook has been hacked is if your contacts are receiving spam emails from your account. If you’re alerted to the fact that your account is sending out emails you didn’t send, immediately take steps to secure your account.
Is my Outlook being monitored?
Checking email snooping To check in Outlook, the most commonly used email client, go to Tools, Email Accounts, and click Change or Properties. You’ll then see whether the POP and SMTP server is a local or proxy server. It it’s a proxy server, the email is being monitored.
Can other people see my emails?
When you send email, you might think the contents are private — the only people that will see them are you and the recipients of the message. Unfortunately, that’s just not the case — email is one of the least secure forms of communication there is.
Can someone access my email remotely?
Whether it’s a personal email or a business account, getting your email hacked is a scary possibility. Hackers can quickly gain access to anything you’ve sent – like passwords, account numbers, or bank information – plus, they could use your account to send viruses to other computers, and then hack them.
Open task manager by right-clicking on the taskbar and choosing Task Manager. If there’s a suspicious process, that’s the monitoring app. Question: Can my company see what I do on my computer? Answer: Your company can see your device activities and track them if they provide you with that computer.
Can someone hack your email without a password?
If a hacker wanted to try breaking into one of your online accounts, knowing your email address is a solid first step. Obviously, they can’t log in without your password, but by knowing your email address, they could target you with phishing emails – malicious attachments that install malware on your machine.
Should I delete my email if it was hacked?
If you have been hacked several times and your email provider isn’t mitigating the amount of spam you are receiving, then consider starting afresh but don’t delete your email address! Many experts do warn against deleting email accounts as most email providers will recycle your old email address.
Can you tell if someone opened your Gmail?
If you use a gmail.com account, read receipts won’t work. To find out when an email you sent was opened, you can request a read receipt. A read receipt is sent to you as an email with the time and date of when your message was opened. Want to get more out of Google apps at work or school?
Is my Outlook being monitored?
Checking email snooping To check in Outlook, the most commonly used email client, go to Tools, Email Accounts, and click Change or Properties. You’ll then see whether the POP and SMTP server is a local or proxy server. It it’s a proxy server, the email is being monitored.
Can I see who has logged into my Office 365 account?
Login history can be searched through Office 365 Security & Compliance Center. In the left pane, click Search, and then click Audit log search. Please notice that for User activity in Exchange Online (Exchange mailbox audit logging) you need to have mailbox audit logging turned on for each user.
How do I remove my Microsoft account from other devices?
If you don’t use a device but it still appears in your devices, here’s how to remove it: Go to account.microsoft.com/devices, sign in, and find the device you want to remove. Select the device to see all your options, select Remove device, then follow the instructions.
How can you tell if someone has read your email in Outlook without them knowing?
Select File> mail option or click “Mail’ from the left side bar. Under “Tracking” section, look for “For all messages sent, request”. Now, select checkbox for “read receipts”. By doing this, you can confirm that the recipient views the sent message or not.
Go to Options. Select Mail from the left-pane. Lookup for the Tracking. See under For all messages sent, request you will see two checkboxes saying Delivery receipt confirming the message was delivered to the recipient’s email server & Read receipt confirming the recipient viewed the message.
Has my email been opened?
Fortunately, there are actually two ways to tell whether an email has been opened and read: Request a return receipt. Use an email tracking tool.
How do I keep my email private?
Encrypt your email. The best way to keep your private email away from prying eyes and hackers is to use encryption. Encryption protects your private email by jumbling up your messages, making them impossible to decipher unless you explicitly authorize someone to read them.
How does someone hack your email?
Phishing The most common way email gets hacked are through phishing schemes. Phishing is the most widely used technique because it’s simple, affordable, and attacks the weakest link in any security system – people.
Can you tell if your computer is being monitored?
Look for Suspicious Processes You can find suspicious processes by opening the Windows Task Manager. After booting up your computer and loading Windows, press Ctrl+Alt+Del and select “Task Manager.” From the “Processes” tab, scroll through the list of active running while looking for any that are out of the ordinary.
Can my employer monitor my work computer at home?
Conclusion: Your Boss Can Legally Monitor Any Activity on a Work Computer or A Work Network. As you now know, your boss can monitor almost anything you do during the day – whether you’re working remotely or have returned to the office.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.