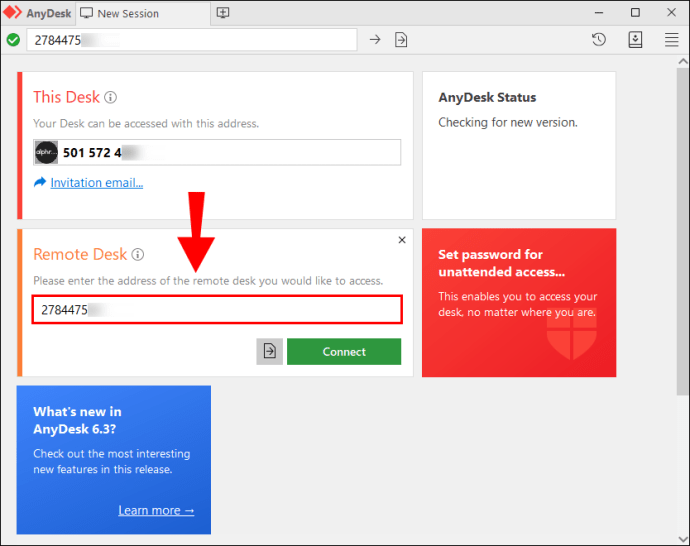
With regards to Anydesk specifically, uninstalling the application, is enough to prevent remote access to your system.
Does deleting AnyDesk stop access?
With regards to Anydesk specifically, uninstalling the application, is enough to prevent remote access to your system.
How do I close AnyDesk on Windows 10?
Click Start and select “All Programs.” Scroll down and click on the “Startup” folder. If there is a shortcut to Anydesk there, delete it.
How do I stop remote access to my computer?
Open System and Security. Choose System in the right panel. Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab. Click Don’t Allow Connections to This Computer and then click OK.
Does AnyDesk use IP address?
AnyDesk clients use the TCP-Ports 80, 443, and 6568 to establish connections. It is however sufficient if just one of these is opened. AnyDesk’s “Discovery” feature uses a free port in the range of 50001–50003 and the IP 239.255. 102.18 as default values for communication.
How do I stop AnyDesk access on my Mac?
Task Manager => Startup tab => right click on AnyDesk and change it to disable. Control Panel => Administrative Tools => Services => AnyDesk Service => Right click and select properties => Startup type from [Automatic] to [Manual] => also you can press on stop button.
How do I completely remove AnyDesk from my Iphone?
Helpful answers. You can hold down Option key and the apps will start to jiggle, then press the cross button and press delete. The app is deleted. You can hold down Option key and the apps will start to jiggle, then press the cross button and press delete.
Can AnyDesk be tracked?
AnyDesk outputs trace files while running that can be utilized to diagnose problems. Some errors occur without causing an immediate crash and may cause other unintended behavior.
How do I uninstall AnyDesk silently?
Removing AnyDesk This can be done using either the –remove or –uninstall command as mentioned in Installation Commands. –uninstall will start the uninstallation process for the AnyDesk client. Using this command, a GUI prompt will appear which will guide the user through the uninstallation process.
Can someone remotely access my computer when it’s off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
Can a website detect AnyDesk?
No, they cannot.
Is AnyDesk legal?
Warranty rights of the Customer remain unaffected by this provision. 4.3 The customer may request from ANYDESK the necessary interface information for the creation of an interoperable, independently created program. However, ANYDESK is under no legal obligation to provide the customer with interface information.prieš 6 dienas
How do you tell if your Mac has been remotely accessed?
Open System Preferences>Sharing and go to the Screen Sharing tab, check whether it is on, if so whether it is set to allow access for all users or only specified ones. Do the same for the Remote Login tab, Remote Management tab, and Remote Apple Events tab.
Does deleting an app uninstall it?
Yes, on Android devices “uninstall” is the same thing as “delete”. When you remove an app you purchased, you can still reinstall it without having to pay again.
Is AnyDesk a security risk?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
Can someone connect to my computer without me knowing?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
How do I see who is connected to my computer?
right click on my computer -> manage ->shared folders -> sessions/open files. that will tell you what windows shares they are looking at.
Can a hacker take control of my computer?
Your computer can be used to attack other computers. Sometimes hackers will take over a computer, sometimes thousands of them, to launch an attack on a website they’ve targeted.
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Is AnyDesk a security risk?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
Does AnyDesk use camera?
He simply uses AnyDesk: Almost every laptop has a built-in webcam, and with AnyDesk, you can turn it on from anywhere and have a clear view of your room. That’s where you’ll find your kitties sleeping soundly. Be sure to use a strong password and disconnect the session afterwards.
How do I disable remote access on Mac?
Disabling Remote Access for macOS Click the Apple icon > System Preferences, then click the Sharing icon. 2. Uncheck the boxes next to Remote Login and Remote Management.
How do I remove AnyDesk from my browser?
Delete AnyDesk (malicious add-ons) from Microsoft Edge Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
How to fix AnyDesk not working on Windows 10?
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”. After you uninstall all the potentially unwanted program causing AnyDesk issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection.
How do I uninstall the anydeskapp?
Click Finder, in the opened screen select Applications. Drag the app from the Applications folder to the Trash (located in your Dock), then right click the Trash icon and select Empty Trash. In the uninstall programs window, look for ” AnyDeskApp ” and other potentially unwanted programs, select these entries and click ” Uninstall ” or ” Remove “.
How to resolve AnyDesk not working in Mozilla Firefox?
If you face problems in AnyDesk removal then you have the option to rese the settings of Mozilla Firefox. Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”. In the newly opened pop-up window, click “Refresh Firefox” button