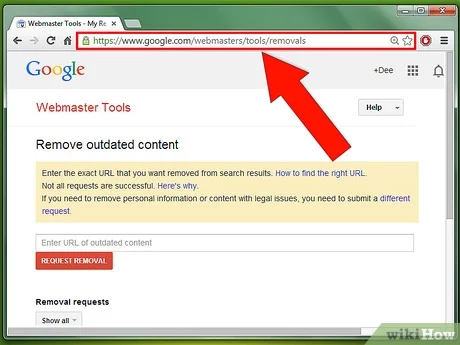
Log in to your account. Choose “Removal” from the “Index” menu. Select the “Temporary Removals” tab. Hit the “New Request” button (keep it on “Remove this URL only”) and enter the URL of the page you wish to remove entirely from search results and Google’s cache.Choose “Removal” from the “Index” menu Select the “Temporary Removals” tab Hit the “New Request” button (keep it on “Remove this URL only”) and enter the URL of the page you wish to remove entirely from search results and Google’s cache
Can a website be taken down?
A website can be taken down for for copyright violation. The OSP/ISP that is hosting the website can take a website down if the site does not remove or “take down” the infringing content identified in a DMCA Takedown notice. A DMCA Takedown notice is the preferred method for this process.
Can I request Google to delete my data?
You can manually delete all activity from My Activity or filter by date and product to delete activity items or groups of activity. You can always delete activity manually, even if automatic deletion is turned on. You can delete your Google Account or delete a Google service.
How do I remove my personal information from Google for free?
How to submit a removal request to Google. To submit a removal request for this kind of information ahead of the tool’s launch, head to Google’s search results removal form and select “Remove information you see in Google Search” under the “What do you want to do?” tab.
How does the FBI shut down a website?
The FBI can use an IP address to find out where the physical servers are located. If that is in the US then they can simply go and seize those servers as evidence, or use a subpoena.
How do I delete an article from Google?
Removing a News Article from Google Search and the Internet In essence, the only way to remove the article is to directly contact the news agency or the individual that published the article and to request that they remove it. This request is known in the industry as a request for “unpublishing.”
What happens if you click on an unsecure website?
Insecure websites are vulnerable to cyberthreats, including malware and cyberattacks. If your site falls victim to a cyberattack, it can impact the site’s functioning, prevent visitors from accessing it, or compromise your customers’ personal information.
Can the FBI see my texts?
A recently discovered FBI training document shows that US law enforcement can gain limited access to the content of encrypted messages from secure messaging services like iMessage, Line, and WhatsApp, but not to messages sent via Signal, Telegram, Threema, Viber, WeChat, or Wickr.
How does the FBI track your computer?
Additionally, the FBI has other ways to tell what a person is doing on his or her computer. It can break into the machine, either remotely or by breaking into someone’s office, and install key logger software, which enables agents to monitor what a person types on the keyboard.
What can the FBI do with an IP address?
Law enforcement can find out who this person is by subpoenaing the service provider for the IP address associated with that activity. A subpoena is a legal instrument used to compel individuals or companies to provide evidence, usually under the threat of a penalty for failing to comply.
How can I check to see if a website is safe?
Fortunately, there are two quick checks to help you be certain: Look at the uniform resource locator (URL) of the website. A secure URL should begin with “https” rather than “http.” The “s” in “https” stands for secure, which indicates that the site is using a Secure Sockets Layer (SSL) Certificate.
Can a website steal my information?
Hackers illegally access devices or websites to steal peoples’ personal information, which they use to commit the crimes like theft. Many people shop, bank, and pay bills online. People also store financial information, like credit card or bank account numbers, on their devices.
Can a website hack you?
The question “can you get hacked by visiting a website” seems to be floating around the internet a lot. The short answer to it is “yes”, in principle you can. As is often the case, however, the short answer only tells part of the story. The whole story helps to shed a lot more light on internet security.
Can the FBI tap your phone?
Federal agents cannot legally tap your phone whenever they want to. They have to follow strict guidelines and go through a specific process to obtain approval.
Does the FBI listen to your phone calls?
The main statute the FBI uses to listen in directly on phone calls is called Calea – the 1994 Communications Assistance for Law Enforcement Act. Calea was designed to make it easier for the FBI to listen in on calls as telecoms technology shifted from copper wires to digital.
How do I know if I am being investigated?
You are visited or contacted by the police – The most common way to tell if the police are investigating you is if they confront you personally. You may find police showing up at your home, place of work, or reaching out to you by phone to ask questions about a criminal case.
Can the government see my deleted search history?
Important Caveats. While the government won’t go snooping through your Internet history, emails, or text messages, it can review publicly available information about you. This can include anything you’ve ever posted to social media, an online forum, or other places on the Internet that can be traced back to you.
Can the FBI see your screen?
Meinrath explained that the rumor regarding FBI surveillance was truer than some may believe. “The easy answer is yes, [the FBI] has the capability of [monitoring through laptop cameras],” Meinrath said.
Can an IP address be traced to a cell phone?
This IP address will never be identified by your device or revealed to your device, however, so it is very unlikely anybody could track your device that way either.
Can I be identified by my IP address?
What information does my IP address reveal? IP addresses do reveal your geolocation, but not your precise location like a home address does. IP addresses will also never reveal your name, phone number, or other precise personal information.
How do you know if a website will give you a virus?
Google Safe Browsing is a good place to start. Type in this URL http://google.com/safebrowsing/diagnostic?site= followed by the site you want to check, such as google.com or an IP address. It will let you know if it has hosted malware in the past 90 days.
How can you tell if a website is malicious?
To find out if a link is safe, just copy/paste the URL into the search box and hit Enter. Google Safe Browsing’s URL checker will test the link and report back on the site’s legitimacy and reputation in just seconds. It’s that easy to use Google’s URL scanner.
What types of content does Google remove from search results?
Mostly, the list includes highly-sensitive private information and personal information. Here are a few examples of the types of content Google will remove from your search results: If your issue falls into one of these categories, you can use a simple tool to remove personal information from Google.
How to remove online content from search engines?
Seven ways to remove online content from search: 1 Ask people to delete their content 2 Remove content at the publisher level 3 Ask people to change their content 4 Make a page invisible to Google 5 Google removal 6 Suppress visibility More …
How do I remove content from other Google properties?
To remove content from other Google properties, search the help documentation for your product to learn how to remove it. For example: Google Shopping and some other properties: Opt out of search results for specific Google properties here .
How do I remove a page or file from Google search?
To permanently remove your page or file from Google Search: Block access to it, as described in Get information off the web. Add a noindex tag or header to your page. Important: When using this method, be sure that your page is not blocked by a robots.txt file.