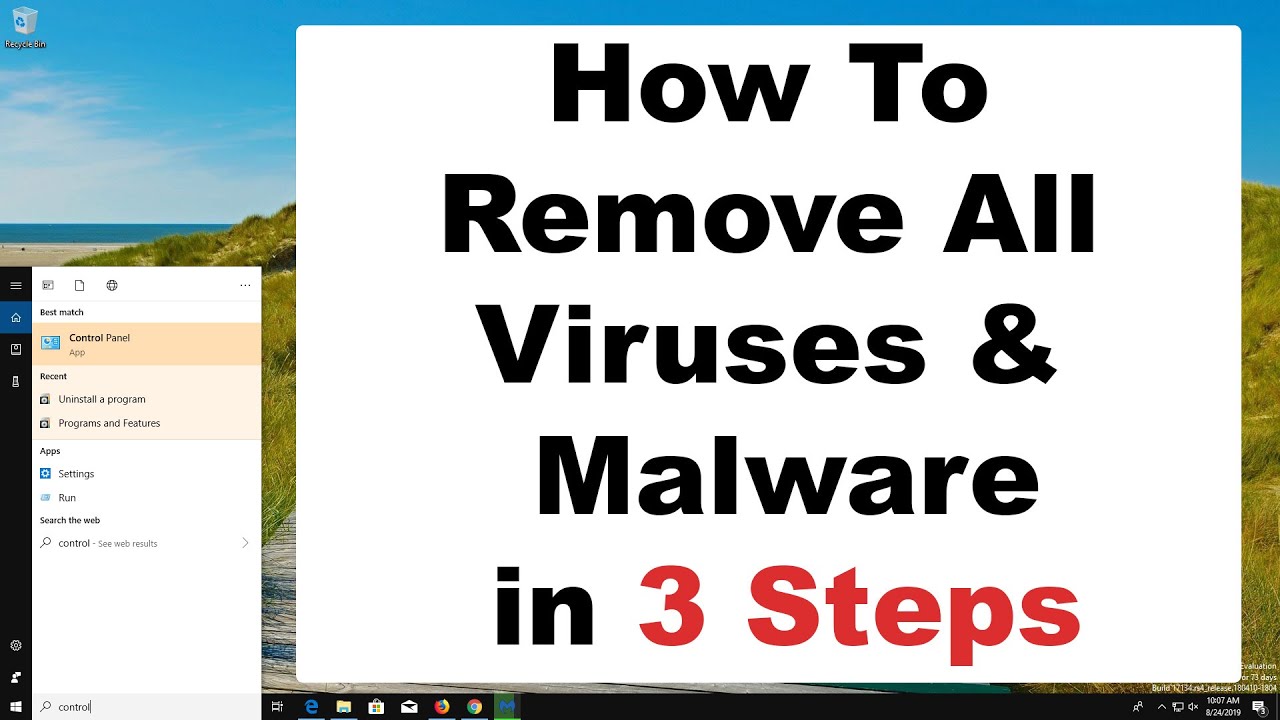
Windows Security is a powerful scanning tool that finds and removes malware from your PC. Here’s how to use it in Windows 10 to scan your PC. Important: Before you use Windows Defender Offline, make sure to save any open files and close apps and programs.
Can malware be removed from a computer?
Windows Security is a powerful scanning tool that finds and removes malware from your PC. Here’s how to use it in Windows 10 to scan your PC. Important: Before you use Windows Defender Offline, make sure to save any open files and close apps and programs.
Does McAfee remove malware?
How does McAfee Virus Removal Service work? McAfee Virus Removal Service detects and eliminates viruses, Trojans, spyware and other malware easily and quickly from your PC. It also applies security updates to your operating system and your security software when necessary.
Does Norton remove malware?
Yes, Norton 360 provides anti malware protection. It protects against computer viruses, spam, social dangers, phishing, identity theft, and other online born threats.
How do I manually find malware on my computer?
Open your Windows Security settings. Select Virus & threat protection > Scan options. Select Windows Defender Offline scan, and then select Scan now.
What happens if a virus gets in my computer?
A computer virus infiltrates a computer and its programs similar to the way the flu infects your body’s immune system and multiplies. Viruses can be installed on your computer without your knowledge or consent, and can insert new, malicious code that can monitor and manipulate your online activity.
Does resetting a PC remove virus?
Running a factory reset, also referred to as a Windows Reset or reformat and reinstall, will destroy all data stored on the computer’s hard drive and all but the most complex viruses with it. Viruses can’t damage the computer itself and factory resets clear out where viruses hide.
Does a factory reset remove viruses?
On an Android device, a factory reset will generally remove a virus. The Android operating system uses an app on its recovery partition during a hard reset to restore factory settings. Malicious apps on mobile devices are less prevalent than desktop systems where antivirus software is crucial.
What is the difference between a virus and malware?
Often used interchangeably, the terms malware and virus have two distinct meanings. Malware, or malicious software, is an overarching term used to describe any program or code that is created with the intent to do harm to a computer, network or server. A virus, on the other hand, is a type of malware.
Is it worth paying for McAfee?
Overall, McAfee’s antivirus scanner is among the very best on the market. If you’re looking for reliable protection against both known and zero-day threats, McAfee is a really good choice, with perfect malware detection rates, fast scans, and simple scan scheduling.
What happens if malware is detected?
In short, malware can wreak havoc on a computer and its network. Hackers use it to steal passwords, delete files and render computers inoperable. A malware infection can cause many problems that affect daily operation and the long-term security of your company.
What’s the difference between malware and a virus?
Often used interchangeably, the terms malware and virus have two distinct meanings. Malware, or malicious software, is an overarching term used to describe any program or code that is created with the intent to do harm to a computer, network or server. A virus, on the other hand, is a type of malware.
What happens when Norton detects a virus?
When your Norton product detects a security risk, it automatically removes it, unless it requires your input to understand how you want to resolve the risk.
How good is Norton at detecting malware?
How long does it take Norton to clean?
The actual removal process, handled by the Norton Removal Tool may take as long as 10 minutes. During this time, the computer will be restarted, possibly more than once.
What are the most common ways to be infected by a computer Virus?
Methods of Malware and Virus Infection and Spread Downloading infected files as email attachments, from websites or through filesharing activities. Clicking on links to malicious websites in emails, messaging apps or social network posts.
What are the most common ways to be infected by a computer virus?
Methods of Malware and Virus Infection and Spread Downloading infected files as email attachments, from websites or through filesharing activities. Clicking on links to malicious websites in emails, messaging apps or social network posts.
Can you delete a virus file?
Deleting an infected file removes both the virus and the infected file from your computer. Unless the virus has already infected other files on your computer, deleting an infected file is the most effective way of removing the virus and ensuring that it does not spread to other files.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Can you tell if someone is remotely accessing your computer?
You can use the Windows Task Manager on your computer to assess whether any programs have been opened on your computer without your knowledge. If you see programs in use that you did not execute, this is a strong indication that remote access has occurred.
How much is it to get a virus off your computer?
The average cost of a virus removal at a technology retailer like Best Buy or Staples ranges from $99 to $149, so it’s easy to see how the cost of dealing with a virus can quickly grow.
How do hackers take control of your computer?
Another common way that hackers use to gain control of your computers is by sending out Trojan Viruses disguised as email attachments. Hackers typically send out these messages to 1000s of users with enticing headings and an attachment which they are hoping you will open.