Ensure that the Remote Desktop protocol is enabled on the target server. Check if the user is a non-administrator user on the target server. If yes, then check if the RDP connection to the target server works with the credentials of a user who is administrator on the target server.If the access denied issue is caused by a corrupt account, you can resolve it by creating a new local user profile / account. To do that, follow these steps: Step 1 Click Start menu and select Settings. Click Accounts on the Windows Settings pane. Step 2 Select “Family & other people” on the left side and then click “Add someone else to this PC”.
How do I allow login through Terminal Services?
Start > Run > gpedit. msc. Expand: Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Management. Select: Allow log on through Remote Desktop Services.
Why Remote Desktop is not working?
Check firewalls, security certificates and more if a remote desktop is not working. When the remote desktop connection between a Windows desktop and its host fails, it’s time to do some remote desktop troubleshooting by checking firewalls, security certificates and more.
What is Deny logon through Terminal Services?
The “Deny logon through Terminial Services” right defines the accounts that are prevented from logging on using Terminal Services. If Terminal Services is not used by the organization, the Everyone group must be assigned this right to prevent all access.
What is Terminal Services logon?
The “Allow Logon through Terminal Services” policy is a Microsoft Group Policy Object (GPO) that defines how the Remote Desktop Protocol (RDP) behaves when connecting users remotely to a machine. System Administrators use this policy to grant users the rights necessary for RDP sessions.
How do I see who is connected to my RDP server?
The easiest way to determine who has access to a particular Windows machine is to go into computer management (compmgmt. msc) and look in Local Users and Groups. Check the Administrators group and the Remote Desktop Users group to see who belongs to these.
What is remote access for?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection. Remote access enables users to connect to the systems they need when they are physically far away.
How do I know if remote desktop is enabled?
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server and to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services. If the value of the fDenyTSConnections key is 0, then RDP is enabled. If the value of the fDenyTSConnections key is 1, then RDP is disabled.
What does Deny logon locally mean?
The “Deny log on locally” specifies the users or groups that are not allowed to log into the local computer. This policy can be found in Computer Configuration > Policies > Security Settings > Local Policies > User Rights Assignment > Deny log on locally.
How can I tell if someone is accessing my server?
A very basic check you can try is to telnet to the port, if it times out then it’s inaccessible, if you get a clear screen and flashing cursor (it may timeout with and error eventually or possibly even print some text), just type “TELNET {IP Address} {PORT}”.
How do I grant access to server?
Click Start, point to Administrative Tools, and then click Routing and Remote Access. Double-click Your_Server_Name, and then click Remote Access Policies. Right-click Connections to Microsoft Routing and Remote Access server, and then click Properties. Click Grant remote access permission, and then click OK.
How can I tell who is logged into a server?
Step 1- Open the Command Line Interface by running “cmd” in the run dialog box (Win + R). Step 2- Type query user and press Enter. It will list all users that are currently logged on your computer.
How do I know if Remote Desktop is enabled?
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server and to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services. If the value of the fDenyTSConnections key is 0, then RDP is enabled. If the value of the fDenyTSConnections key is 1, then RDP is disabled.
What ports need to be open for Remote Desktop?
Remote Desktop requires TCP port 3389 to be open. It is also possible to change the listening port for Remote Desktop on your computer. If you don’t want to use 3389 externally, open a different port externally, but point it to 3389 on the IP address of the machine you want RDC on.
Is IT safe to allow remote access?
Remote access solutions could leave you vulnerable. If you don’t have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
What is a remote access code?
Definition of Remote Access Code. What is a remote access code? It is a code or a password that a user enters to gain access to a private network or server. It is a form of authentication that either permits or blocks an access attempt from entering a corporate system.
How do I find my IP address?
Here’s how to find the IP address on the Android phone: Go to your phone’s settings. Select “About device.” Tap on “Status.” Here you can find information about your device, including the IP address.
How do I access my IP?
Click Start ->Control Panel -> Network and Internet -> Network and Sharing Center. and go to Details. The IP address will display.
How do I install remote access and routing in Windows 10?
Click Start, point to Administrative Tools, and then click Routing and Remote Access. In the console tree, expand Routing and Remote Access, expand the server name, and then click Remote Access Policies. Right-click the right pane, point to New, and then click Remote Access Policy.
Is Remote Desktop enabled by default?
The Remote Desktop or RDP feature is disabled by default, so you will need to enable it in the settings.
Can hackers remotely access your computer?
Remote desktop hacks become a common way for hackers to access valuable password and system information on networks that rely on RDP to function. Malicious actors are constantly developing more and more creative ways to access private data and secure information that they can use as leverage for ransom payments.
Can I disable remote access Connection Manager?
Double-click Remote Access Connection Manager. In the Startup type list, click Disabled. Click Stop, and then click OK.
How do I resolve the Access Denied issue?
If the access denied issue is caused by a corrupt account, you can resolve it by creating a new local user profile / account. To do that, follow these steps: Step 1 Click Start menu and select Settings.
Why am I getting folder access denied error?
When you try to delete, copy, move or change a file or folder on your computer, you might be blocked by Accedd denied error which prompts you donot have permission to do so. The error message could be: “Folder Access Denied. You need permission to perform this action. You require permission from TrustedInstaller to make changes to this folder.”
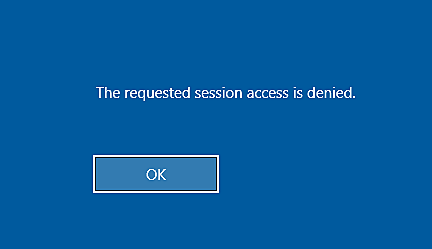
Why can’t I access the admin console?
The requested session access is denied. Attempting the connection with the same non-administrator user from a different client machine is working This is most likely because you are trying to login taking over the admin console session on the target machine.
What does Access Denied mean on Windows 10?
The “Access Denied” error appears when your browser uses different proxy settings or VPN instead of what’s really set on your Windows 10 PC. Thus, when a website detects that there is something wrong with your browser cookies or your network, it blocks you and this is why you can’t open it. Windows 10 users – we’ve all been there.