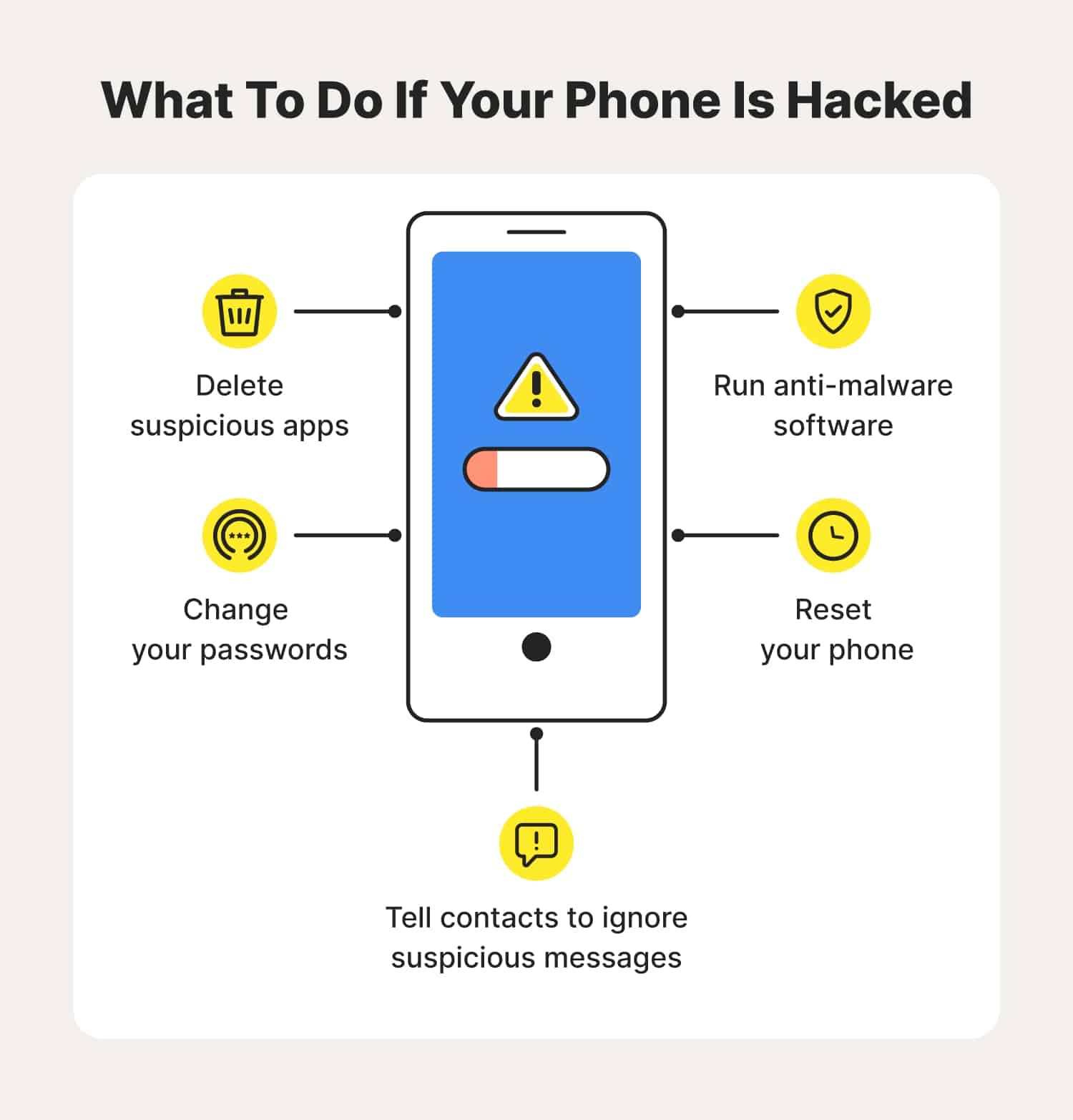
Poor performance: If your phone shows sluggish performance like crashing of apps, freezing of the screen and unexpected restarts, it is a sign of a hacked device. Unrecognised apps: If you notice any unrecognised applications downloaded on your device, it could be the work of a hacker.
What happens if my phone is hacked?
If you find apps you haven’t downloaded, or calls, texts, and emails that you didn’t send, that’s a red flag. A hacker may have hijacked your phone to send premium-rate calls or messages or to spread malware to your contacts. Similarly, if you see spikes in your data usage, that could be a sign of a hack as well.
How will I know if my Android phone is hacked?
The quickest and easiest way to find out if you’ve been hacked is to install a security or antivirus app. This will allow you to perform scan on your device and find out for sure if there is malicious software installed onto your Android system.
What happens if my phone is hacked?
If you find apps you haven’t downloaded, or calls, texts, and emails that you didn’t send, that’s a red flag. A hacker may have hijacked your phone to send premium-rate calls or messages or to spread malware to your contacts. Similarly, if you see spikes in your data usage, that could be a sign of a hack as well.
Will resetting phone remove hackers?
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device. Follow the instructions below to reset your iPhone or Android.
Can someone hack my phone with my number?
That said there are a few ways a hacker can use your phone number to help get extra access as part of a larger attack: ‘Phishing’ for personal data. It’s common for hackers to send fake text messages to their targets in order to gain username and password information (this is known as phishing).
Who is accessing my phone?
Open the Android Settings app. Tap “Mobile Network” (It’s in the “Network & Internet” section.) On the Mobile Network screen, tap “App Data Usage.” Here, you can view your current cellular app data usage.
Can hackers see you through your phone camera?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
What does *# 21 do to your Android phone?
According to tech magazine How-To Geek, dialing this code shows whether or not call forwarding is enabled on the device — not whether it’s been hacked. How-to Geek described the *#21# feature as an “interrogation code” that allow users to view their call forwarding setting from the phone app.
What happens if my phone is hacked?
If you find apps you haven’t downloaded, or calls, texts, and emails that you didn’t send, that’s a red flag. A hacker may have hijacked your phone to send premium-rate calls or messages or to spread malware to your contacts. Similarly, if you see spikes in your data usage, that could be a sign of a hack as well.
Can your phone be hacked when turned off?
Can a phone be hacked while turned off? The short answer is no, your phone cannot be hacked while it’s turned off. Phone hacking, even remotely, only works if the device being targeted is on.
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.
Can someone hack your phone text?
Android phones can get infected by merely receiving a picture via text message, according to research published Monday. This is likely the biggest smartphone flaw ever discovered.
Is there an app to stop hackers?
Norton is the leading antivirus app for Android and iOS devices and will protect your phone against all types of cyberthreats, including phishing links, identity theft, viruses, malware, and more. You can test its features risk-free with the whopping 60-day money-back guarantee.prieš 6 dienas
Is someone watching my phone?
To check your mobile data usage on Android, go to Settings > Network & Internet > Data Usage. Under Mobile, you’ll see the total amount of cellular data being used by your phone. Tap Mobile Data Usage to see how your data use has changed over time. From here, you can identify any recent spikes.
What is the use of * * 4636 * *?
Android code: *#*#4636#*#* This code will open up a menu that shows information about your phone’s data usages. Here’s how you can retrieve deleted text messages on your iPhone.
What does * 73 do on a phone?
Call forwarding is activated when someone answers at the forwarded number. To deactivate call forwarding, dial *73. Listen for two beeps, then hang up. Answer all your incoming calls, even when you’re already on the line.
Does resetting phone remove virus?
On an Android device, a factory reset will generally remove a virus. The Android operating system uses an app on its recovery partition during a hard reset to restore factory settings. Malicious apps on mobile devices are less prevalent than desktop systems where antivirus software is crucial.
Should I reset my iPhone if hacked?
If you suspect your iPhone has been hacked, you should reset your phone to its factory settings. What do you have to do to prevent another attack? Never connect to a free Wi-Fi Do not jailbreak your phone Delete any apps on your phone you do not recognize Do not download illegitimate apps, like the flashlight app.
Does resetting iPhone delete hackers?
Restoring your system to its original factory settings will wipe out any back doors hackers established into your device. However, restoring your phone to a back-up where the back doors were already installed could preserve the hacker’s way into the device.
Does resetting phone delete everything?
To remove all data from your phone, you can reset your phone to factory settings. Factory resets are also called “formatting” or “hard resets.” Important: You’re using an older Android version.
What happens if my phone is hacked?
If you find apps you haven’t downloaded, or calls, texts, and emails that you didn’t send, that’s a red flag. A hacker may have hijacked your phone to send premium-rate calls or messages or to spread malware to your contacts. Similarly, if you see spikes in your data usage, that could be a sign of a hack as well.