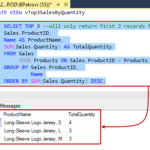
It won’t protect you from viruses or malware. It won’t keep your internet service provider (ISP) from seeing where you’ve been online. It won’t stop websites from seeing your physical location. And any bookmarks you save while in private browsing or incognito mode won’t disappear when you switch it off.
Can you be tracked in secret mode?
Incognito mode doesn’t prevent web tracking Your favorite websites, your ISP, your employer — not to mention data brokers and hackers coveting your personal data — can all still track you.
Is Secret mode really secret?
The word incognito means to hide one’s true identity. Incognito mode on Android devices is just that; it’s a way to hide as you travel the web. As realized in Google Chrome on Android, Incognito mode hides your browsing history so others can’t see the websites you’ve visited.
Is Secret mode encrypted?
No, the Google Chrome browser’s incognito mode is not a VPN. It doesn’t encrypt your web activity or IP address as a VPN does; it simply hides your browsing history from other users on your device.
What is safer than incognito?
The incognito mode protects your privacy from other people who use your device, while a VPN keeps you anonymous and safe from everybody on the internet.
Is incognito mode actually private?
Incognito or private mode will keep your local browsing private, but it won’t stop your ISP, school, or employer from seeing where you’ve been online. In fact, your ISP has access to all your browsing activity pretty much no matter what you do. You can, however, use a Virtual Private Network (VPN) service.
Can police track incognito?
Sure. It is safe and it keeps you anonymous. However, if it is a matter of court and police, the VPN company gives your data. Nobody knows, but your VPN knows where you visited and what you did using their service.
Can WIFI owner see what sites I visited incognito?
Nope. When you use incognito mode, your device and browser don’t keep a log of the sites you’re visiting. Yet, the Wi-Fi router can still log that information and the network admin can always retrieve that information later.
What is disadvantage of incognito mode?
Cons of incognito mode While browsing incognito, unless you take additional steps to encrypt your data and internet connection, your IP address remains visible and other people on your network can see your online activity.
Who can see your incognito activity?
When you browse privately, other people who use the device won’t see your history. Chrome doesn’t save your browsing history or information entered in forms. Cookies and site data are remembered while you’re browsing, but deleted when you exit Incognito mode.
How do you know if he’s using secret conversations?
It’s worth noting that if you send someone a message through Secret Conversations, they will know it’s a secret chat because the message bubble, which is usually blue, will be black. Next to their image it will read ‘Encrypted from one device to the other’ to let both parties know they’re engaged in a “Secret” chat.
Can Facebook secret conversations be recovered?
Secret Conversations have device keys to verify encryption, and can be set to disappear after a certain time, but Facebook can still access and decrypt them if they are reported.
Can I see secret conversations on another device?
You can only access a secret conversation on the device the you created it on. You can send secret conversations from another device, but you won’t be able to see any previous messages.
Does Google still track you in incognito mode?
‘ If you’re using “incognito” mode on the Google browser, you might think, or even be led to believe, you’re browsing history and internet visits are private and not being tracked. That is not true. No matter where you go online, if you’re using the Chrome browser, you are being followed.
Can hotel Wi-Fi see what you are doing on incognito mode?
Can’t I Just Use Incognito/Private Mode on Hotel WiFi? No, that’s not enough. The fact that incognito or private mode can hide your traffic is actually a common misconception we hear very often.
What is disadvantage of incognito mode?
Cons of incognito mode While browsing incognito, unless you take additional steps to encrypt your data and internet connection, your IP address remains visible and other people on your network can see your online activity.
Can iphones track private browsing?
Yes, private browsing on iPhone can be traced. There are plenty of options for private browsing on your iphone like the Safari private browsing mode, Chrome incognito mode, and Safari’s Hide IP Address option.
Can my internet provider see what I browse?
ISPs cannot see which specific pages within that website you visit (everything after the ‘/’). ISPs cannot see what you search for or what you type into forms.
Can police see deleted history?
So, can police recover deleted pictures, texts, and files from a phone? The answer is yes—by using special tools, they can find data that hasn’t been overwritten yet. However, by using encryption methods, you can ensure your data is kept private, even after deletion.
What is illegal to search on the internet?
States may differ in how they define “illegal” online content, but federal law is quite clear on what not to search on Google. This includes: Images or video of child sexual abuse or exploitation. Content that promotes terrorism or advocates terrorist acts. Content that promotes, incites or instructs crime or violence.
Can the government see my deleted search history?
Important Caveats. While the government won’t go snooping through your Internet history, emails, or text messages, it can review publicly available information about you. This can include anything you’ve ever posted to social media, an online forum, or other places on the Internet that can be traced back to you.
How do I stop Wi-Fi owner from viewing my history?
You can hide your WiFi history by using Tor or a VPN. VPN is a better choice than Tor if you want to be confident in your online privacy and security.