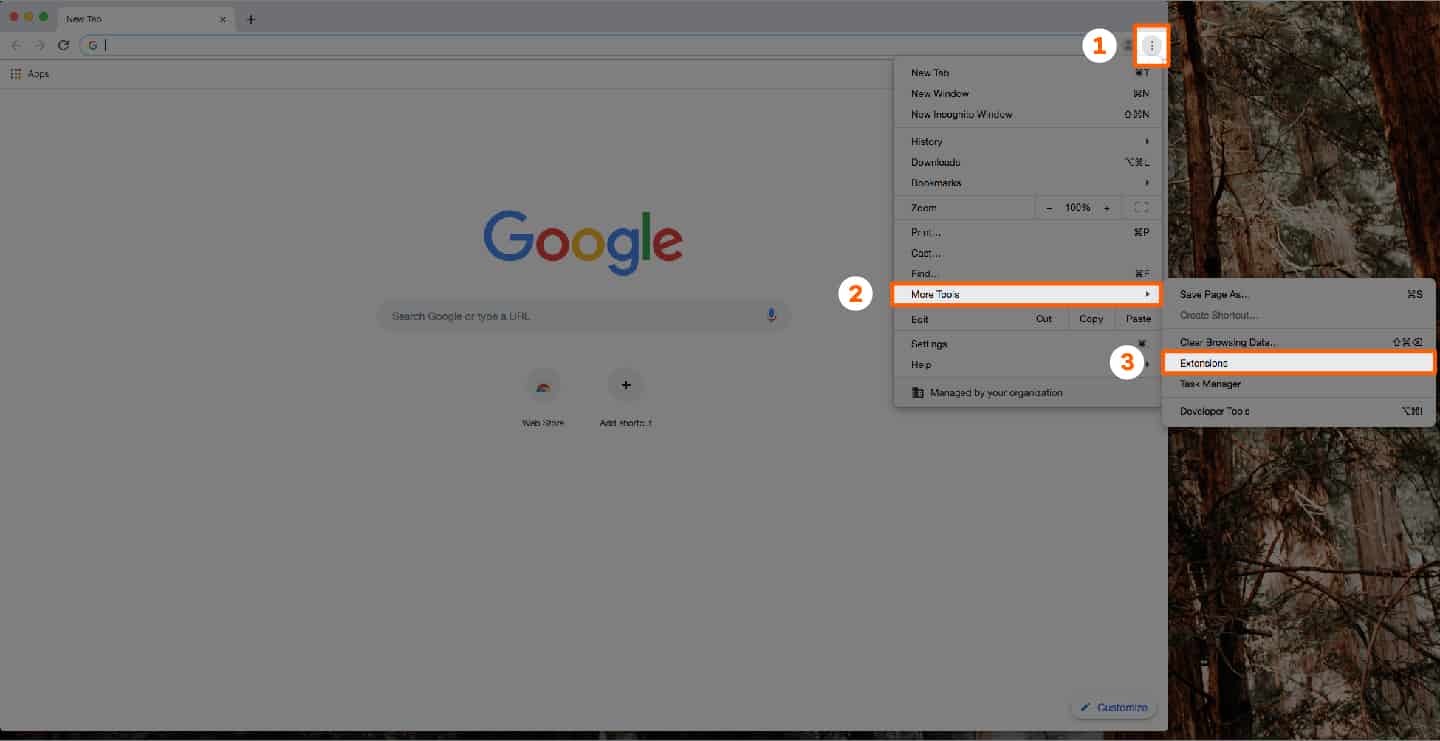
How can I check if Chrome.exe is legitimate or a virus? The best way to figure out if your version of Chrome.exe is a legitimate file or a virus is to run a full system scan using a comprehensive antivirus scanner. However, you can also check the Chrome.exe file manually.Chromium virus removal Open your Task Manager and look for processes named “ Chromium.” Right-click on it and select “ Open File Location.” Keep the Chromium folder open and follow the next step. Step 2: Download And Run Rkill.exe The second step is to close all the running processes of the target Adware to allow its removal.
How do I know if Chrome exe is a virus?
How can I check if Chrome.exe is legitimate or a virus? The best way to figure out if your version of Chrome.exe is a legitimate file or a virus is to run a full system scan using a comprehensive antivirus scanner. However, you can also check the Chrome.exe file manually.
What is Chrome virus?
What Is the Chromium Virus? The Chromium virus is a malicious web browser that is created using the Chromium code. It is able to overwrite the Chrome browser and replace the original shortcuts with fake ones.
Does uninstalling Chrome remove malware?
When you uninstall and reinstall Chrome, the moment you login to your Google account again, Google will faithfully restore your cloud backup which ends up reinstalling the malware. To fix this, you need to wipe your Chrome sync data. That will delete all the cloud backups, including hopefully the malware.
Why does Chrome keep telling me I have a virus?
The Google Chrome pop-up virus is a common and frustrating malware on Android phones. The most common cause for this virus is downloading apps from third-party or unknown sources which contain the malware. The most important thing is to NOT tap anywhere on the pop-up!
Where is Google Chrome exe file located?
The chrome.exe file is located in a subfolder of “C:\Program Files (x86)” (e.g. C:\Program Files (x86)\Google\Chrome\Application\).
Why do I have so many Chrome exe?
You may have noticed that Google Chrome will often have more than one process open, even if you only have one tab open. This occurs because Google Chrome deliberately separates the browser, the rendering engine, and the plugins from each other by running them in separate processes.
Can Google Chrome get viruses?
Google Chrome includes a feature to synchronize your browser data between computers, including web browser extensions. This is a convenient feature, but when malware infects your Google Chrome browser, it can hitch a ride on the sync data and become difficult to remove with anti-virus programs.
How do I check for malware on Chrome?
To run a scan, you need to open Chrome’s settings. To do so, click on the triple-dot icon in the top-right corner, then click “Settings”. Once in the settings, you should run a quick “Safety check”, to do so, click on “Check now” in the “Safety check” subsection, which is third from the top.
Can Google Chrome have a virus?
Does Chrome have inbuilt Antivirus? YES, Google Chrome comes with an inbuilt Malware scanner. It can search and report the malicious files and applications that are causing the trouble on your system or browser. However, this inbuilt anti-malware only comes with the Windows version of Google Chrome.
What causes browser hijacking?
Browser hijacking occurs when unwanted software alters the activity of the internet browser to spy on users, steal their information, or to display persistent advertising.
Is my browser hacked?
One of the most common symptoms of browser hijacking is discovering that your homepage has been reset. If your browser displays an unfamiliar website after launch, particularly one that is pornographic or advertising fake security software, this is almost definitely the work of a hijacker.
Is a browser hijacker a virus?
Short bio. Browser hijackers, or simply hijackers, are a type of malware created for the purpose of modifying Internet browser settings without the user’s knowledge or consent.
What is hijacking in computer?
Cyber hijacking, or computer hijacking, is a type of network security attack in which the attacker takes control of computer systems, software programs and/or network communications.
How can I find a hidden Virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
Is there a free Virus removal?
Don’t worry about viruses. Avast One scans and cleans the viruses currently on your device, and stops future viruses and threats from infecting your system.
Why is Google Chrome taking up so much CPU?
Explaining Chrome’s CPU Usage These typically relate to your browsing behavior, including having too many tabs open at once, too many apps or browser extensions running and streaming high-quality video. Likewise, auto-playing videos, animations and excessive ads can also cause these problems.
Why do I see multiple Chrome exe in Task Manager?
But if you open the Task Manager, you may be surprised to see many Google Chrome processes running. I could see 18 running even though I had opened only in one single window with 4 tabs. This is because Chrome opens a separate process for each of its tab, extension, tab and, subframe.
Does factory reset remove virus?
On an Android device, a factory reset will generally remove a virus. The Android operating system uses an app on its recovery partition during a hard reset to restore factory settings. Malicious apps on mobile devices are less prevalent than desktop systems where antivirus software is crucial.
Will resetting PC remove virus?
Running a factory reset, also referred to as a Windows Reset or reformat and reinstall, will destroy all data stored on the computer’s hard drive and all but the most complex viruses with it. Viruses can’t damage the computer itself and factory resets clear out where viruses hide.
Why does Chrome keep telling me I have a virus?
The Google Chrome pop-up virus is a common and frustrating malware on Android phones. The most common cause for this virus is downloading apps from third-party or unknown sources which contain the malware. The most important thing is to NOT tap anywhere on the pop-up!
What happens when you reset Chrome settings?
Resetting Chrome will restore your home page and search engine to their default settings. It will also disable all browser extensions and clear out your cookie cache. But your bookmarks and saved passwords will remain, at least in theory. You may want to save your bookmarks before performing a browser rest.
How to remove Google Chrome virus and adware effectively?
Here are the steps you need to take to remove the Google Chrome virus and adware from your browser: Step 1. Reset browser settings Open Chrome and click on the three dots in the upper right corner Step 2. Change default ads permissions Click on pop-ups and redirects and select “ don’t allow sites to send pop-ups and redirects ” Step 3.
What is the Google Chrome virus?
The Google Chrome virus is a browser hijacker (a type of malware) which changes the browser’s settings and configuration without permission from the user. This leads to pop-up ads, redirects to suspicious websites, homepage changes, and certain browser settings being deleted.
How to remove a Chromebook virus?
Therefore, if you notice any strange redirects or a high CPU usage on your device, it might be a case of a Chromebook virus. For Chromebook virus removal, as well as malware avoidance on the Chrome OS, you should install a reputable anti-malware extension that would be able to block phishing and scam sites.
How do I remove a virus from my computer?
Move at the bottom of the Settings page and click on Advanced. Again scroll down and under “Reset and clean up,” click on Clean up computer. Click Find and uncheck the “Send details to Google….” below, if you don’t want to share the details with Google. Chrome will scan your computer and ask for removing the malicious application and files.