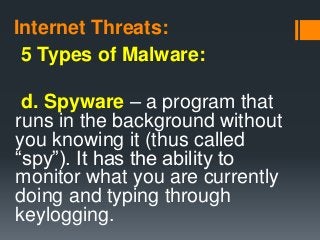
a program that runs in the background without you knowing it (thus called “spy”). It has the ability to monitor what you are currently doing and typing through keylogging. used to record the keystroke done by the users.
What is a program that runs in the background without you knowing it it has the ability to monitor what you are currently doing?
Spyware is a type of program that is installed with or without your permission on your personal computers to collect information about users, their computer or browsing habits tracks each and everything that you do without your knowledge and send it to remote user.
What type of program that runs in the background without knowing it?
A daemon is a type of background process designed to run continually in the background, waiting for event(s) to occur or condition(s) to be met. These processes typically use minimal system resources and perform tasks which require little to no input from the user.
What do you mean by spyware?
Spyware is malicious software that enters a user’s computer, gathers data from the device and user, and sends it to third parties without their consent. A commonly accepted spyware definition is a strand of malware designed to access and damage a device without the user’s consent.
Which Internet threats that disguised as a useful program and allows hackers to get your information?
Trojan. A Trojan disguises itself as desirable code or software. Once downloaded by unsuspecting users, the Trojan can take control of victims’ systems for malicious purposes.
What type of program that runs in the background without knowing it?
A daemon is a type of background process designed to run continually in the background, waiting for event(s) to occur or condition(s) to be met. These processes typically use minimal system resources and perform tasks which require little to no input from the user.
What is spyware and adware?
Spyware are programs designed to track all of your computer activities, from which applications you use to which websites you visit. Adware are programs that pop-up various advertisements and offers, often based on the websites you visit.
What is running in the background on my computer?
You can access the Task Manager by pressing the Ctrl + Alt + Del shortcut keys on your keyboard, then select Task Manager. You can also right-click with your mouse on the Windows Taskbar and select Task Manager.
What does it mean to run in the background?
When you have an app running, but it’s not the focus on the screen it is considered to be running in the background.
What is a background in programming?
When referring to multitasking operating systems, the background is the place an active program is running, but not visible to the user. For example, you could have a program playing music, minimize the program and continue to listen to the music while browsing the Internet. Note.
Can VPN stop spyware?
Use a VPN – While a VPN can’t prevent spyware from being downloaded onto your device, it can mask your location and prevent your online behavior from being tracked and monitored. The best VPNs also feature anti-malware and ad-blocking software, like CyberGhost.
How do I know if I have spyware?
Look out for the following clues: Increasing sluggishness and slow response. Unexpected advertising messages or pop-ups (spyware is often packaged with adware). New toolbars, search engines and internet home pages that you don’t remember installing.
Is a program that runs in the background without you knowing it it has the ability to monitor what you are currently doing and typing through keylogging?
A keylogger, sometimes called a keystroke logger or keyboard capture, is a type of surveillance technology used to monitor and record each keystroke on a specific computer.
Which malware is used to steal information from your computer without your knowledge?
Spyware collects your personal information and passes it on to interested third parties without your knowledge or consent. Spyware is also known for installing Trojan viruses. Adware displays pop-up advertisements when you are online.
What type of malware can spread without human interaction?
A worm is a type of virus that can spread without human interaction. Worms often spread from computer to computer and take up valuable memory and network bandwidth, which can cause a computer to stop responding. Worms can also allow attackers to gain access to your computer remotely.
What name is given to a malicious program that comes in disguise of a useful program *?
Trojan Horses Trojan horse programs are malware that is disguised as legitimate software. A Trojan horse program will hide on your computer until it’s called upon.
How does spyware infect a computer?
Some common ways your device might become infected with spyware include: Accepting a prompt or pop-up without reading it first. Downloading software from an unreliable source. Opening email attachments from unknown senders.
What type of program that runs in the background without knowing it?
A daemon is a type of background process designed to run continually in the background, waiting for event(s) to occur or condition(s) to be met. These processes typically use minimal system resources and perform tasks which require little to no input from the user.
What is a Trojan spyware?
A Trojan, or Trojan horse, is a type of malware that conceals its true content to fool a user into thinking it’s a harmless file.
What is phishing and spyware?
A phishing email is sent to trick the user. The email is either seeded with a Trojan or has a link for downloading the Trojan or spyware. The Trojan/spyware monitors and reports the user activity and sends login or other confidential data to the malicious user as soon as it detects user access to the target page.
What is the most common type of spyware?
Adware: This is the most common type. It causes pop-up advertising to appear constantly. Not only is it annoying, but any information you provide may be stored and sent without your permission when accessing any of these sites.
What is a virus for computers?
A computer virus is a type of malicious software, or malware, that spreads between computers and causes damage to data and software.
What is a background a program?
A program that runs in the background without you knowing it. It has the ability to monitor what you are currently doing and typing through key logging. A. Worms B. Spyware C. Virus D. Fair Use 15. A malicious program designed to transfer from one computer to another in any means possible. A.
What are the programs that run in the background of computer?
There are programs and utilities that run in the background of every computer. Some of these programs are necessary for your system to function. Others may be malware, adware, or malicious programs designed to hijack your computer or personal information.
What are hidden background programs?
Others may be malware, adware, or malicious programs designed to hijack your computer or personal information. Let’s discuss some ways to access these hidden background programs: Most people have at least heard of “Ctrl+Alt+Delete”.
How can I see what processes are running in the background?
There are sites that will provide an explanation of most any process found running in the background of your computer. Computer management is another feature of the Windows operating system that will allow you to see services and applications that are running in the background of your computer.