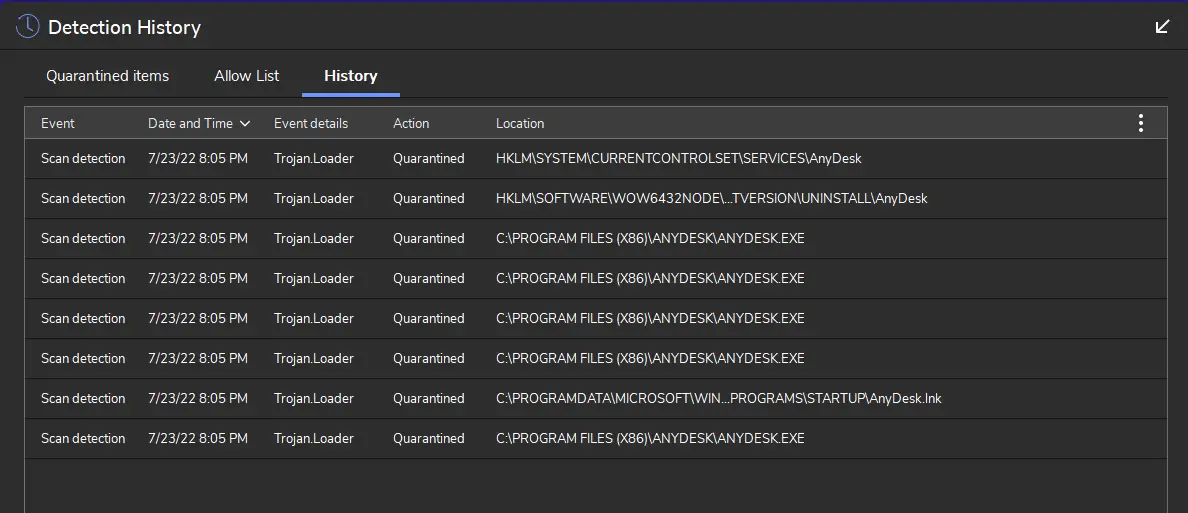
It is known that cybercriminals use deceptive methods to trick users into unknowingly installing AnyDesk. This app is not malicious, but it can be misused for malicious purposes (e.g., to steal sensitive information or infect a computer with malware).
Is AnyDesk a spyware?
AnyDesk is used legitimately by millions of IT professionals worldwide, to remotely connect to their clients’ devices to help with technical issues. However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money.
Is AnyDesk a security risk?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
Can AnyDesk hack my computer?
Sophos discovered that the AvosLocker attackers installed AnyDesk so it works in Safe Mode, tried to disable the components of security solutions that run in Safe Mode, and then ran the ransomware in Safe Mode.
Should I delete AnyDesk?
With regards to Anydesk specifically, uninstalling the application, is enough to prevent remote access to your system. This of course assumes your colleague didn’t upload anything to your computer without your knowledge.
Can AnyDesk be tracked?
AnyDesk outputs trace files while running that can be utilized to diagnose problems. Some errors occur without causing an immediate crash and may cause other unintended behavior.
What happens if I uninstall AnyDesk app?
What happens if I uninstall AnyDesk? After uninstalling the potentially unwanted program that causes AnyDesk redirects, scan your computer for any remaining unwanted components or possible malware infections.
What are the disadvantages of AnyDesk?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
Is TeamViewer better than AnyDesk?
For teams that want the choice of whether to run their remote access solution on-premises or in the cloud, AnyDesk is perhaps the best option. And for teams that want to ensure compatibility with all devices, TeamViewer might be the better choice, simply for its range of compatible manufacturers.
Is AnyDesk any good?
AnyDesk is a brilliant software for connecting to remote desktops. It is one of the popular platforms for accessing systems remotely and is very easy to use. The interface provided can be easily understood by the non techies also.
How do I make AnyDesk secure?
You can do that in the security settings: Simply click “Enable unattended access” and choose a secure password. Don’t forget: A strong password is the first line of defense! Unattended access is where the security layers really start to show: If you want, you can set up two-factor authentication.
Do hackers use TeamViewer?
If you are using TeamViewer, then beware and make sure you’re running the latest version of the popular remote desktop connection software for Windows.
How do I uninstall AnyDesk silently?
Removing AnyDesk This can be done using either the –remove or –uninstall command as mentioned in Installation Commands. –uninstall will start the uninstallation process for the AnyDesk client. Using this command, a GUI prompt will appear which will guide the user through the uninstallation process.
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
How do I uninstall AnyDesk from Windows?
Method 2: Uninstall AnyDesk via Apps and Features/Programs and Features. Look for AnyDesk in the list and click on it. The next step is to click on uninstall, so you can initiate the uninstallation.
Does AnyDesk use camera?
He simply uses AnyDesk: Almost every laptop has a built-in webcam, and with AnyDesk, you can turn it on from anywhere and have a clear view of your room. That’s where you’ll find your kitties sleeping soundly. Be sure to use a strong password and disconnect the session afterwards.
What happens if I uninstall AnyDesk app?
What happens if I uninstall AnyDesk? After uninstalling the potentially unwanted program that causes AnyDesk redirects, scan your computer for any remaining unwanted components or possible malware infections.
What are the disadvantages of AnyDesk?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
What AnyDesk used for?
AnyDesk is a remote desktop software that allows us to connect to a computer remotely. It is a cross-platform software that provides platform independent remote access to different devices such as PC and other host devices. It provides remote access, file transfer, VPN features.
Is AnyDesk a spyware?
AnyDesk is used legitimately by millions of IT professionals worldwide, to remotely connect to their clients’ devices to help with technical issues. However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money.
How do I close AnyDesk on Windows 10?
Click Start and select “All Programs.” Scroll down and click on the “Startup” folder. If there is a shortcut to Anydesk there, delete it.
What is the app AnyDesk used for?
AnyDesk is a remote desktop application distributed by AnyDesk Software GmbH. The proprietary software program provides platform independent remote access to personal computers and other devices running the host application. It offers remote control, file transfer, and VPN functionality.
Is AnyDesk a scam?
However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money. #1. Rule Number One Never give anyone you don’t know access to your devices. #2. Rule Number Two Never share online banking login details or any passwords with anyone.
What is AnyDesk remote access program?
Remote access program, requires authentication and goes through their servers. Fine, so long as you or your technician is using AnyDesk for remote support. Remote acess program. I am a technition, so I use it to provide remote support to my clients and friends, just like I do with TeamViewer.
How do I know if AnyDesk is a threat?
Therefore, you should check the AnyDesk.exe process on your PC to see if it is a threat. We recommend Security Task Manager for verifying your computer’s security. This was one of the Top Download Picks of The Washington Post and PC World . Remote access program, requires authentication and goes through their servers.
How to get rid of AnyDesk malware?
Instant automatic removal of AnyDesk malware: Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. Spyhunter is a professional automatic malware removal tool that is recommended to get rid of AnyDesk malware.