End-to-end encryption protects your iMessage and FaceTime conversations across all your devices. With watchOS, iOS, and iPadOS, your messages are encrypted on your device so they can’t be accessed without your passcode.
Is iMessage actually secure?
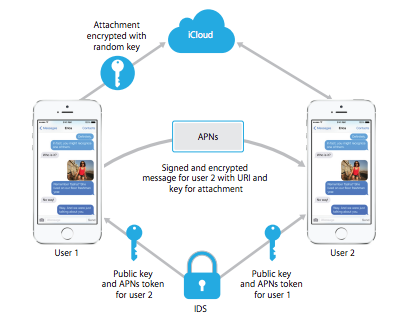
Apple’s iMessage for iPhone, iPad, and Mac always uses end-to-end encryption. Only the sender and receiver of the messages can see their contents. Photos, videos, and other file attachments are also encrypted. What’s more, Apple’s FaceTime service also uses end-to-end encryption for voice and video calls, too.
Are Apple iMessages private?
iMessage is secured by end-to-end encryption, the idea being that the keys to decrypt messages between you and those you message are only shared between you. That stops anyone intercepting your content.
Can iMessage be hacked?
Apple iMessage uses end-to-end encryption, and it is one of the safest messaging apps available right now. In addition, it uses a security system known as BlastDoor to protect it against malware attacks. It is a safe app because all the photos, videos, and other attachments have encryptions.
Can iMessage be tracked?
“IMessages between two Apple devices are considered encrypted communication and cannot be intercepted, regardless of the cell phone service provider,” the agency’s intelligence note.
Is iMessage actually secure?
Apple’s iMessage for iPhone, iPad, and Mac always uses end-to-end encryption. Only the sender and receiver of the messages can see their contents. Photos, videos, and other file attachments are also encrypted. What’s more, Apple’s FaceTime service also uses end-to-end encryption for voice and video calls, too.
Are Apple iMessages private?
iMessage is secured by end-to-end encryption, the idea being that the keys to decrypt messages between you and those you message are only shared between you. That stops anyone intercepting your content.
Who can see my iMessages?
1 Answer. Show activity on this post. They can only view this information if they are logged into your account on their iDevice. For example, an iPhone, iPad and MacBook all on the same account will receive all messages sent or received from the other machines (barring a lack of network connectivity).
Can police read iMessages?
Law enforcement can retrieve messages via Google / iCloud backups. The chart shows that subpoenas will not grant access to message content for six of the nine secure messaging apps. The three that do give up “limited” content are iMessage, Line and WhatsApp.
Can police retrieve deleted iMessages?
Keeping Your Data Secure So, can police recover deleted pictures, texts, and files from a phone? The answer is yes—by using special tools, they can find data that hasn’t been overwritten yet. However, by using encryption methods, you can ensure your data is kept private, even after deletion.
Is iMessage more secure than SMS?
All Android devices use SMS messages, but this security issue affects iPhone and Android users alike, experts say. Although Apple’s iMessage system is more secure than SMS, iPhone owners must still deliver SMS messages to those who do not have Apple devices.
Is iMessage safer than WhatsApp?
Because it uses end-to-end encryption, WhatsApp is inherently the safer option than other messaging apps. Yes, that includes Facebook Messenger, Instagram Messages, Snapchat, and even regular old iMessage. But it’s not 100 percent foolproof either…
How do you make your iMessages private?
Turn Off Message Preview to Make Message Private on iPhone Open Settings app on your iPhone. Navigate to Notifications > Messages. In the Messages section, you will see two options; you can either use the Message Preview feature to turn on for the Lock Screen or disable the feature completely.
Can iMessages have viruses?
iPhone Viruses from iMessages Hackers may also try to send viruses and other malware through iMessage. Often the message will appear to be urgent or important, and the text will encourage you to click a strange link to claim a prize or resolve some concern.
Can someone hack my iPhone through a text message?
Can iMessage be spied?
Can you spy on iMessages? Yes, you can spy on iMessages. There are various monitoring programs, particularly iPhone spy apps, that allow you to know what information is sent and received via iMessages.
Can someone intercept your iMessages?
Hi, It is absolutely possible to “intercept” iMessages, read, and also reply to them without the intended recipient ever knowing that anything untoward has ever happened.
Is iMessage encrypted over WIFI?
According to Whatsapp, all message traffic between the server and your phone are encrypted. The same applies for iMessage. The initial contact for iMessage is initiated via normal SMS, and does not travel through the wifi network.
Is iMessage more secure than SMS?
All Android devices use SMS messages, but this security issue affects iPhone and Android users alike, experts say. Although Apple’s iMessage system is more secure than SMS, iPhone owners must still deliver SMS messages to those who do not have Apple devices.
Is iMessage safer than WhatsApp?
Because it uses end-to-end encryption, WhatsApp is inherently the safer option than other messaging apps. Yes, that includes Facebook Messenger, Instagram Messages, Snapchat, and even regular old iMessage. But it’s not 100 percent foolproof either…
Can your ISP see your iMessages?
No. Your iMessages are secure, unless someone has your Apple ID and password, they won’t be able to read them. This means your ISP nor Apple can read your iMessages.
Is iMessage actually secure?
Apple’s iMessage for iPhone, iPad, and Mac always uses end-to-end encryption. Only the sender and receiver of the messages can see their contents. Photos, videos, and other file attachments are also encrypted. What’s more, Apple’s FaceTime service also uses end-to-end encryption for voice and video calls, too.