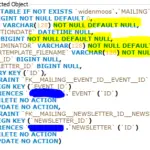
The true dasHost.exe file is a safe Microsoft Windows system process, called “Device Association Framework Provider Host”. However, writers of malware programs, such as viruses, worms, and Trojans deliberately give their processes the same file name to escape detection.
Should I allow dasHost exe?
Yes, you should allow the dasHost.exe process as it is a necessary file to connect the mouse, keyboard, and other wired or wireless devices to your computer.
Can I delete dasHost?
The dasHost.exe (Device Association Framework Provider Host) file is a file provided by Microsoft and used in Windows operating systems. Under normal circumstances, the file should not be moved or deleted because it’s necessary for certain operations.
Is Svchost exe a virus?
The svchost.exe (Service Host) file is a critical system process provided by Microsoft in Windows operating systems. Under normal circumstances, this file isn’t a virus but a crucial component in many Windows services. The purpose for svchost.exe is to, as the name would imply, host services.
What is device association framework provider?
Device Association Framework Provider Host is an official Microsoft core process that runs under the LOCAL SERVICE account. The process serves as a framework for connecting and pairing both wired and wireless devices with Windows.
Can I delete dasHost?
The dasHost.exe (Device Association Framework Provider Host) file is a file provided by Microsoft and used in Windows operating systems. Under normal circumstances, the file should not be moved or deleted because it’s necessary for certain operations.
How do I remove Dllhost exe virus?
Dllhost.exe malware removal: In the uninstall programs window, look for any deceptive/questionable applications, select these entries and click “Uninstall” or “Remove”. After uninstalling the potentially unwanted applications, scan your computer for any remaining unwanted components or possible malware infections.
What is device association service?
Device Association Framework Provide Host (dashHost.exe) is a Microsoft core process that is responsible for pairing both wired and wireless devices in Windows. The process is part of the official suite of Windows components that run under the Local Service account.
What does Csrss EXE do?
Csrss.exe is a safe Microsoft process to help manage the majority of the graphical instruction sets on Windows operating system. Before Windows NT 4.0, csrss.exe was in charge of the whole graphical subsystem, including windows management, drawing options, and many other functions.
How can I tell if an exe is a virus?
Scan the EXE With VirusTotal Another way to find out if the EXE is legit is to scan it with VirusTotal. You simply upload the suspicious file on the VirusTotal website, and this online scanner will check it for all types of malware.
Is svchost.exe a spyware?
No, it isn’t. But a virus can masquerade as an svchost.exe process. If you see a suspicious process, we recommend shutting it down and running an antivirus test immediately to locate the possible virus and remove it.
Can I disable Microsoft Device Association root enumerator?
If you’re not running any old and outdated devices, disabling Microsoft RRAS Root Enumerator does absolutely nothing for your PC. It is safe to disable this driver. However, disabling or enabling the driver is pretty much the same thing if you don’t run legacy devices.
Do I need desktop window manager?
Desktop Window Manager is an essential system process that you can trust to do its job in the background. Its name may be obscure, but DWM is important to the way Windows looks and works, which is why you can’t disable or remove it.
What is run time broker?
Runtime Broker is a Windows process in Task Manager that helps manage permissions on your PC for apps from Microsoft Store. It should only use a few megabytes of memory, but in some cases, a faulty app might cause Runtime Broker to use up to a gigabyte of RAM or more.
What does FileCoAuth exe do?
What does Sdxhelper exe do?
sdxhelper.exe is Microsoft’s secure download manager that is used to download Microsoft Office or Microsoft Office Updates. It may also help if you have two versions of Microsoft Office installed so they can peacefully co-exist on your system without conflicting with each other.
Should I allow dasHost exe?
Yes, you should allow the dasHost.exe process as it is a necessary file to connect the mouse, keyboard, and other wired or wireless devices to your computer.
Can I delete dasHost?
The dasHost.exe (Device Association Framework Provider Host) file is a file provided by Microsoft and used in Windows operating systems. Under normal circumstances, the file should not be moved or deleted because it’s necessary for certain operations.
Why is LockApp exe using my GPU?
If LockApp.exe is taking a large amount of GPU and/or CPU and running for a long time, it may mean that your PC has been locked and awake for a while. In this case, if you sign into your PC, the lock app should automatically suspend itself.
What is LockApp exe and why is it suspended?
The lock app doesn’t use a lot of system resources. If a system tool tells you that it’s been running for a long time, that means your PC was locked and awake for a long time. The PC was sitting at the lock screen, so LockApp.exe was running. And, after you sign into your PC, the lock app automatically suspends itself.
Does locking Windows 10 stop processes?
No, if the screen is simply locked (ctrl-alt-del), any running process will continue (downloads, macros, etc), unless, you have a process that checks if the user is still there (but that isn’t in your problem description so it shouldn’t be the case).
Is COM Surrogate always a virus?
COM Surrogate is a normal Windows process, but hackers use fake versions of it to infect a PC while avoiding detection. The COM Surrogate virus is one of the most common malware infections on Windows computers — it’s pretty dangerous, but getting it off of your PC actually isn’t very hard.