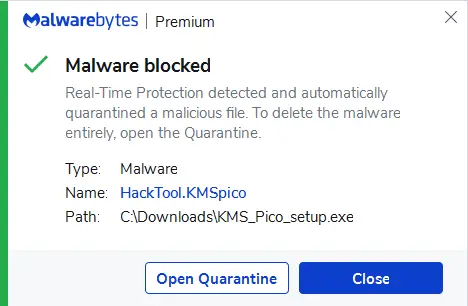
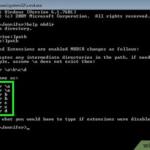
The KMSPico virus is described as a hacking tool that may be used to activate unlicensed versions of Microsoft Windows and Office applications. It is sold under a variety of names, with different “editions” and version numbers.
Is KMSpico trusted?
KMSpico is trustworthy software, but only if you download KMSpico from a legit source. It can help you activate windows and Microsoft Office products for free. KMSpico is regularly updated and maintained which makes it trustworthy and safe.
Is KMSpico a hack?
KMSpico is Malwarebytes’ detection name for a Hacktool that allows the user to use Microsoft software illegally.
How do I get rid of KMSpico virus?
We recommend that the safest way to remove and get rid of KMSpico and its OS-related problems is through a professional anti-malware/antivirus. You’ll need to run a full system scan to eliminate the application from your system and other potentially dangerous components.
Are kms activator safe?
Angelo B37. Microsoft’s Defender will find the KMS activater as a threat and other antivirus software will also do it. We have no information if this kind of tools have malware, we simply advise not to use it. If you do want to use illegal software please use it at your own risk.
Is KMS activator a virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
Who made KMSPico?
Developed by TeamDaz, KMSPICO is an activator used to activate and validate Microsoft Products, such as Windows and Office. It is also known as Windows 10 Activator and has similar versions like KMSAuto and Windows 7 Loader.
Is KMSPico a mine?
The actual KMSPico which was on a thread on MyDigitalLife contains no such miner. Download from another source, besides a copy on the Web Archive of the thread from MyDigitalLife, and you may find something else.
What is the password of KMSPico?
KM Spico Password: 12345.
What is KMS activator?
The Key Management Service (KMS) is an activation service that allows organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation.
Should I uninstall kms after activation?
Yes you can remove KMSpico but dont do it. You may have activated windows or ms office with kmspico now you think that it is useless, no its not like this, to keep your windows activated do not remove kmspico. If you remove it then your windows will go again in trail mode.
What is KMSpico used for?
KMSPico is a tool used to activate a copy of the Windows OSsoftware that is acquired illegally. Doing so is unlawful under almost all circumstances and could have legal repercussions. Cracktools are often downloaded from sites of a shady nature.
What is the original KMSpico site?
You can get an authentic version of KMS Pico from it’s origin, forums. mydigitallife.
Is KMS CMD safe?
Its safe. win 10 allows piracy and you’ll also get updates. However, your product’ll have no official support. KMS activates computers on a local network, eliminating the need for individual computers to connect to Microsoft.
Is KMS activation permanent?
KMS activations are valid for 180 days (the activation validity interval). KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days. By default, KMS client computers attempt to renew their activation every 7 days.
Is KMS client key legal?
No, they are not legal. Be aware of those KMS, some of them might include virus/malware that might damage your PC.
Is it safe to activate Windows 10 using KMSPico?
KMSPico is 100% safe to use. It has been in the wild for about 2 years, which shows how many people are using it safely. We have not seen any reports of anyone succumbing to harm while running this tool on their system.
What is KMSPico used for?
KMSPico is a tool used to activate a copy of the Windows OSsoftware that is acquired illegally. Doing so is unlawful under almost all circumstances and could have legal repercussions. Cracktools are often downloaded from sites of a shady nature.
How does KMSPico work?
What is KMSPICO? It’s a cracking program that can bypass Windows activation. It is an activation prevention tool, which means it will help you in activating your installed Windows very easily. You simply need to download KMSPICO in order to activate it.
What is KMSPico activator?
KMSPico is the activator that is used to activate Microsoft Products, such as Windows and Office. It is a total virus and malware-free tool and trusted by many people.
Can I remove AutoKMS after activation?
AutoKMS is not really a virus, but a hack tool downloaded intentionally by most users who try to activate unregistered Microsoft products. In order to get rid of it, you can try to uninstall it as you do with any other application.
What is KMSPico activator?
KMSPico is the activator that is used to activate Microsoft Products, such as Windows and Office. It is a total virus and malware-free tool and trusted by many people.