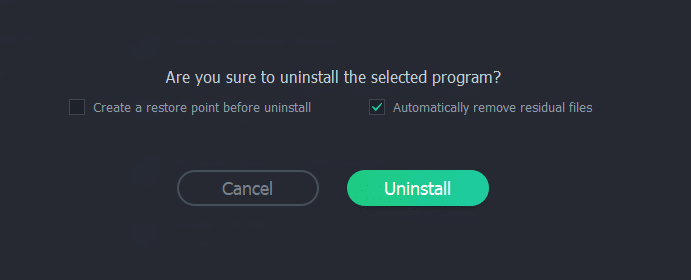
AutoKMS is not really a virus, but a hack tool downloaded intentionally by most users who try to activate unregistered Microsoft products. In order to get rid of it, you can try to uninstall it as you do with any other application.
Can I delete AutoKMS after activation?
AutoKMS is not really a virus, but a hack tool downloaded intentionally by most users who try to activate unregistered Microsoft products. In order to get rid of it, you can try to uninstall it as you do with any other application.
Should I delete KMSPico after activation?
Yes you can remove KMSpico but dont do it. You may have activated windows or ms office with kmspico now you think that it is useless, no its not like this, to keep your windows activated do not remove kmspico. If you remove it then your windows will go again in trail mode.
What happens when KMS activation expires?
After each successful connection, the expiration is extended out to the full 180 days. What happens if Windows cannot reactivatethelicense? If a Windows computer has not been able to reestablish communication to the KMS server after 180 days, the machine will become unlicensed.
What happens if you delete AutoKMS?
It can grant access to hackers or download malicious software and much more. Some Microsoft technicians claim that AutoKMS is a variation of the Troyan virus, but not all go that far. Simply because you can uninstall it anytime, and that’s just not the case with Trojan viruses.
Is kms activator a Virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
Is KMSPico a malware?
KMSPico Malware is a hacking program that claims to be a Microsoft Windows and Office activator. It is extensively disseminated under a variety of names and variants on phoney download sites and file-sharing networks like BitTorrent.
Can Malwarebytes remove kms?
Malwarebytes can detect and remove RiskWare. KMS without further user interaction.
How do I disable KMS key?
Enabling and disabling KMS keys (console) In the navigation pane, choose Customer managed keys. Select the check box for the KMS keys that you want to enable or disable. To enable a KMS key, choose Key actions, Enable. To disable a KMS key, choose Key actions, Disable.
How do I delete old KMS server?
Procedure. Select Configuration > System Settings > Key Management Server. The Key Management Server page appears and shows all key management servers that have been configured. Select the radio button for the KMS you want to remove, and select Remove.
Is KMS activation permanent?
KMS activations are valid for 180 days (the activation validity interval). KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days. By default, KMS client computers attempt to renew their activation every 7 days.
How long is KMS activation?
Any Windows client that configured to use ‘KMS Client Channel’ will be activated against the new KMS host automatically within 2 hours (as this is the ‘KMS Activation Interval’ default value).
What is KMS activation?
The Key Management Service (KMS) is an activation service that allows organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation.
How do I delete KMS server?
Procedure. Select Configuration > System Settings > Key Management Server. The Key Management Server page appears and shows all key management servers that have been configured. Select the radio button for the KMS you want to remove, and select Remove.
Is KMSAuto net malware?
Is kms a hack tool?
KMS is Malwarebytes’ detection name for a Hacktool that allows the user to use Microsoft software illegally.
Is AutoKMS a malware?
AutoKMS is Malwarebytes’ generic detection name for hacktools that are intended to enable the illegal use of Microsoft products like Windows and Office.
Is it safe to use KMS activator?
Angelo B37. Microsoft’s Defender will find the KMS activater as a threat and other antivirus software will also do it. We have no information if this kind of tools have malware, we simply advise not to use it. If you do want to use illegal software please use it at your own risk.
Which KMSpico site is real?
KMSpico is trustworthy software, but only if you download KMSpico from a legit source. It can help you activate windows and Microsoft Office products for free. KMSpico is regularly updated and maintained which makes it trustworthy and safe.
Does KMS activator work on Windows 10?
Is KMSPico a mine?
The actual KMSPico which was on a thread on MyDigitalLife contains no such miner. Download from another source, besides a copy on the Web Archive of the thread from MyDigitalLife, and you may find something else.
Is KMS server safe?
No, it isn’t safe to use either kms activation or any other activation software, specially if they use (as you said) unknown host server beacause this will provide them a kind of backdore to your system by which they might track your files or sensitive information.