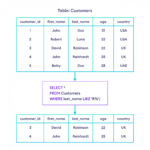
Those who are looking to find out information based on keywords or phrases will want to just use the Google search bar, but those who are looking to have multiple tabs open or are looking for a particular website will want to choose Google Chrome.
Is Google Chrome The safest?
With its comprehensive security features, Google Chrome is the safest browser today. It’s not only safe to download and install but also safe to use. So, it’s a good idea to give this browser a try if you want to ensure that your privacy is well protected while browsing the internet.
Why should I switch from Google to Google Chrome?
Security/Privacy Chrome keeps you safe and sound with its built-in malware and phishing protection. It has safe browsing technology and will show you a warning message before you visit a site that is suspicious. Chrome also automatically updates, so you always have the latest and most up-to-date version.
Do I need both Google and Chrome?
Do I Need Both Google And Google Chrome? Yes, you’re going to need both Google and Google Chrome on your device, even if you only use one or the other. When scrolling through all the applications on your device, you may notice that you have a bunch of useless applications that you never open.
Which browser should I use?
Google Chrome: The best for Mac. Opera Mini: The best for mobile. Vivaldi: The fastest web browser. Tor: The most secure web browser.
Is Google getting rid of Chrome?
Has Google Chrome been hacked?
G oogle has announced that Google Chrome has been successfully hacked as it discovers 30 security flaws–seven of which pose a “high” threat to users. In a blog post, Google revealed that a new update will make improvements for Windows, Mac, and Linux, to fix the security issues after the hack.
Is Google Chrome safe for online banking?
The answer is an easy one: yes. It’s just as safe as doing online banking on your Windows 10 PC or a MacBook. Chrome OS is, more or less, just Google Chrome, and chances are you’re using that on a Mac or PC anyway.
Is Chrome safer than Safari?
Both browsers are pretty similar in security, but Chrome has a slight edge thanks to a host of customizable security extensions. The Safari password management trumps Chrome, though, and is invaluable for users of Apple devices.
What’s the difference between Chrome and Google app?
The distinction therefore between Chrome Apps and Google Apps is that Chrome is a browser, while Google Apps is not; it is a web hosted service that does not distinguish functionality through browsers, so it can be utilized using virtually any browser.
What happens if I disable Chrome?
Disabling chrome is almost the same as Uninstall since it will no longer be visible on the app drawer and no running processes. But, the app will still be available in phone storage. In the end, I will also be covering some other browsers that you might love to check out for your smartphone.
Is Microsoft edge or Google Chrome better?
In terms of features and privacy, Microsoft has made major upgrades. It has unique features like Reading aloud, immersive reading, built-in adblockers, and stringent privacy measure makes the Microsoft Edge better than Google Chrome. But, when it comes to personalization, Google Chrome has a sweet spot.
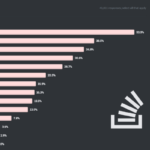
Why is Google Chrome the most popular browser?
Chrome surpassed all the other browsers at the time thanks to its lean design and low hardware footprint, which was a breath of fresh air at the time. However, that has changed over the past few years, with alternatives like Microsoft Edge and Firefox consuming far less RAM and CPU resources than Chrome.
Why do people delete Google Chrome?
Protection: Chrome delete can also be used as a means of protecting the factory chrome, rather than eliminating it. This prevents the chrome from fingerprints and potential damage. Heat reduction: Chrome delete can be used to keep door handles and other parts of the exterior cooler during the hot summer months.
Has Google Chrome been hacked?
G oogle has announced that Google Chrome has been successfully hacked as it discovers 30 security flaws–seven of which pose a “high” threat to users. In a blog post, Google revealed that a new update will make improvements for Windows, Mac, and Linux, to fix the security issues after the hack.
What happens if I delete Google?
You’ll lose all the data and content in that account, like emails, files, calendars, and photos. You won’t be able to use Google services where you sign in with that account, like Gmail, Drive, Calendar, or Play.
What is the number 1 browser?
How I know my phone is hacked or not?
Poor performance: If your phone shows sluggish performance like crashing of apps, freezing of the screen and unexpected restarts, it is a sign of a hacked device. Unrecognised apps: If you notice any unrecognised applications downloaded on your device, it could be the work of a hacker.
Do I need to update Chrome?
Improved speed and performance. Chrome makes staying safe easy by updating automatically. This ensures you have the latest security features and fixes as soon as they’re available.
Which browser can be hacked?
Security exploits can also take advantage of vulnerabilities (security holes) that are commonly exploited in all browsers (including Mozilla Firefox, Google Chrome, Opera, Microsoft Internet Explorer, and Safari).
Do you need antivirus for Google Chrome?
Yes, Google Chromebooks need antivirus protection. While they come with some in-built antivirus features, the protection provided isn’t foolproof. You can download a malicious app from the Google Play Store or fall victim to an online scam or phishing site.