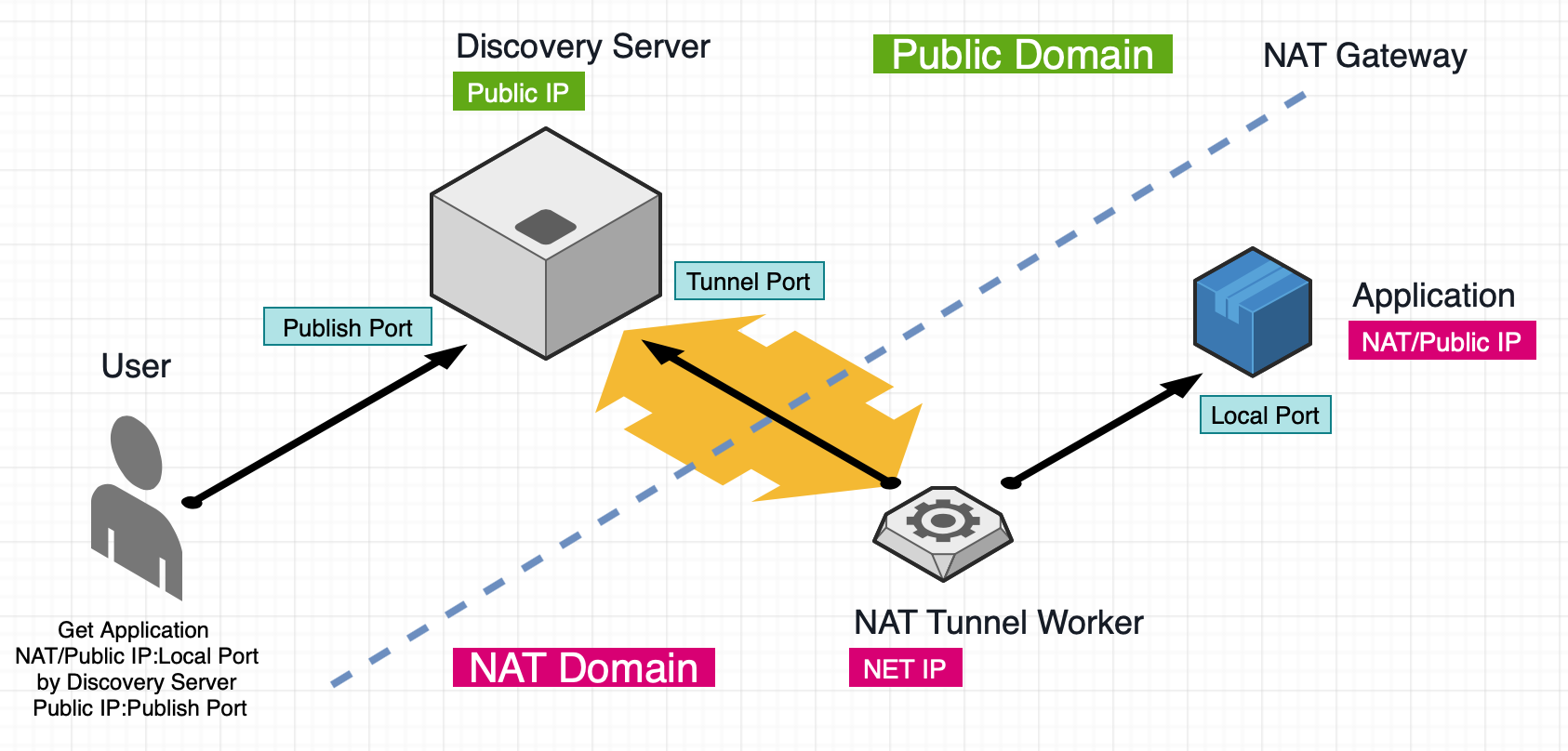
TCP tunnel is a technology that aggregates and transfers packets sent between end hosts as a single TCP connection. By using a TCP tunnel, the fairness among aggregated flows can be improved and several protocols can be transparently transmitted through a firewall.
How does TCP tunneling work?
TCP-tunneling using AnyDesk is geared towards forwarding any TCP-based protocol between the local and remote clients so that the local client can access the services/devices accessible by the remote client. For this feature to work, it requires an active AnyDesk connection between the local and remote clients.
What is tunnel in firewall?
Tunneling, also known as “port forwarding,” is the transmission of data intended for use only within a private, usually corporate network through a public network in such a way that the routing nodes in the public network are unaware that the transmission is part of a private network.
What is TCP over TCP?
This article explains why TCP-over-TCP could be a performance disaster. My understanding about the issue is that the ‘outer’ TCP connection deals with packet loss and congestion of the network and acts accordingly by increasing timeouts (and thus reducing throughputs).
What is UDP tunnel?
This networking mode enables you to interconnect virtual machines running on different hosts. Technically this is done by encapsulating Ethernet frames sent or received by the guest network card into UDP/IP datagrams, and sending them over any network available to the host.
How does TCP tunneling work?
TCP-tunneling using AnyDesk is geared towards forwarding any TCP-based protocol between the local and remote clients so that the local client can access the services/devices accessible by the remote client. For this feature to work, it requires an active AnyDesk connection between the local and remote clients.
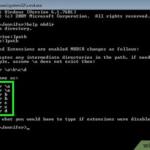
How do I create a TCP tunnel?
Go to Configuration > Services > Proxy Services and create a New Service. Configure the Proxy Settings to be TCP Tunnel and add relevant listening ports for destination. Once configured, save this service and ensure it is intercepted.
Why is tunneling used?
Tunneling is often used in virtual private networks (VPNs). It can also set up efficient and secure connections between networks, enable the usage of unsupported network protocols, and in some cases allow users to bypass firewalls.
Is SSH a tunnel?
SSH tunneling, or SSH port forwarding, is a method of transporting arbitrary data over an encrypted SSH connection. SSH tunnels allow connections made to a local port (that is, to a port on your own desktop) to be forwarded to a remote machine via a secure channel.
What is tunnel IP address?
An IP Tunnel is a communication channel, that can be created by using encapsulation technologies, between two networks that do not have a routing path. Every IP packet that is shared between the two networks is encapsulated within another packet and then sent via the tunnel.
What is TCP used for?
TCP stands for Transmission Control Protocol a communications standard that enables application programs and computing devices to exchange messages over a network. It is designed to send packets across the internet and ensure the successful delivery of data and messages over networks.
How does TCP work?
How does TCP work? TCP provides communication between an application program and the Internet Protocol (they are frequently written as TCP/IP.) An application does not need to required packet fragmentation on the transmission medium or other mechanisms for sending data in order to be sent via TCP.
What does TCP stand for?
Transmission Control Protocol (TCP)
Which tools are tunneling protocols?
Tunneling protocols, such a GRE and L2TP, are common tools for interconnecting two similar networks over a different network.
How UDP is different from TCP?
TCP is a connection-oriented protocol, whereas UDP is a connectionless protocol. A key difference between TCP and UDP is speed, as TCP is comparatively slower than UDP. Overall, UDP is a much faster, simpler, and efficient protocol, however, retransmission of lost data packets is only possible with TCP.
What is the advantage of UDP over TCP?
UDP is faster, simpler, and more efficient than TCP. Retransmission of lost packets is possible in TCP, but not in UDP. There is no retransmission of lost packets in the User Datagram Protocol (UDP).
How long does it take for a tunneling wound to heal?
The wound usually heals within four weeks, and many people don’t require any further treatment.
What is tunneling process explain in detail with example?
What Does Tunneling Mean? Tunneling is a protocol that allows for the secure movement of data from one network to another. Tunneling involves allowing private network communications to be sent across a public network, such as the Internet, through a process called encapsulation.
How does SSH tunneling work?
SSH tunneling, or SSH port forwarding, is a method of transporting arbitrary data over an encrypted SSH connection. SSH tunnels allow connections made to a local port (that is, to a port on your own desktop) to be forwarded to a remote machine via a secure channel.
How does IPv6 tunneling work?
IPv6 Tunneling allows hosts in one private IP network to communicate with hosts in another private IP network by providing a tunnel between two routers across the Internet. The IPv6 tunnel connection endpoints are terminated via a Virtual Tunnel Interface (VTI) configured in each device.
How does TCP tunneling work?
TCP-tunneling using AnyDesk is geared towards forwarding any TCP-based protocol between the local and remote clients so that the local client can access the services/devices accessible by the remote client. For this feature to work, it requires an active AnyDesk connection between the local and remote clients.
What is TCP meltdown?
TCP Meltdown occurs when you stack one transmission protocol on top of another, like what happens when an OpenVPN TCP tunnel is transporting TCP traffic inside it.
What is the TCP/NC tunnel?
The TCP/NC tunnel can mitigate the end-to-end TCP performance degradation in lossy networks without any change on end-host TCP. We implemented and validated our proposal in Network Simulator 3, based on a reinforced version of TCP/NC that we previously proposed.
What is a tunneling protocol?
In computer networks, a tunneling protocol is a communications protocol that allows for the movement of data from one network to another.
What is an IP tunnel used for?
IP tunnel. An IP tunnel is an Internet Protocol (IP) network communications channel between two networks. It is used to transport another network protocol by encapsulation of its packets.
How does HTTP tunneling work with TCP?
HTTP CONNECT method The most common form of HTTP tunneling is the standardized HTTP CONNECT method. In this mechanism, the client asks an HTTP proxy server to forward the TCP connection to the desired destination. The server then proceeds to make the connection on behalf of the client.