Chrome.exe is the executable file that opens and runs the Chrome browser on your computer, but the Chrome.exe virus is a trojan that imitates Chrome.exe and can seriously damage your computer.
Can I remove Chrome exe?
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall. In the uninstall programs window, look for “Chrome.exe virus”, select this entry and click “Uninstall” or “Remove”.
Can I remove Chrome exe?
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall. In the uninstall programs window, look for “Chrome.exe virus”, select this entry and click “Uninstall” or “Remove”.
How do I know if Chrome exe is a virus?
How can I check if Chrome.exe is legitimate or a virus? The best way to figure out if your version of Chrome.exe is a legitimate file or a virus is to run a full system scan using a comprehensive antivirus scanner. However, you can also check the Chrome.exe file manually.
Why do I have so many Chrome exe?
You may have noticed that Google Chrome will often have more than one process open, even if you only have one tab open. This occurs because Google Chrome deliberately separates the browser, the rendering engine, and the plugins from each other by running them in separate processes.
Where is Chrome exe on my computer?
Otherwise, LEAPWORK may not be able to find Chrome.exe file in its default location, usually, the default location in 64-bit Windows operating system is C:\Program Files (x86)\Google\Chrome\Application\chrome.exe and in 32-bit Windows operating system it is C:\Program Files\Google\Chrome\Application\chrome.exe.
Why is Chrome running in the background?
This might be to enable functionality such as email checks or virus scans, or because an app needs to update itself or stay aware while you work on other tasks. Google Chrome for Mac runs installed extensions and Web apps in the background, if they request it.
Can Google Chrome have a virus?
The Google Chrome virus is a browser hijacker (a type of malware) which changes the browser’s settings and configuration without permission from the user. This leads to pop-up ads, redirects to suspicious websites, homepage changes, and certain browser settings being deleted.
How do I check for malware on Chrome?
To run a scan, you need to open Chrome’s settings. To do so, click on the triple-dot icon in the top-right corner, then click “Settings”. Once in the settings, you should run a quick “Safety check”, to do so, click on “Check now” in the “Safety check” subsection, which is third from the top.
How can you tell a fake virus warning?
The Federal Trade Commission (FTC) warns that the scareware scam has many variations, but there are some telltale signs: You may get ads that promise to “delete viruses or spyware,” “protect privacy,” “improve computer function,” “remove harmful files,” or “clean your registry.”
What happens if I disable Chrome?
Disabling chrome is almost the same as Uninstall since it will no longer be visible on the app drawer and no running processes. But, the app will still be available in phone storage. In the end, I will also be covering some other browsers that you might love to check out for your smartphone.
How do I remove Chromium virus from Windows 10?
#1) Click on the “Windows” button and search for “Control Panel”. #2) Click on “Programs”, and then click on “Uninstall a program”, as shown in the image below. #3) Now, locate “Chromium” from the list of programs and right-click on it, then click on “Uninstall”.
Can I remove Chrome exe?
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall. In the uninstall programs window, look for “Chrome.exe virus”, select this entry and click “Uninstall” or “Remove”.
How do I remove chromium virus from Windows 10?
#1) Click on the “Windows” button and search for “Control Panel”. #2) Click on “Programs”, and then click on “Uninstall a program”, as shown in the image below. #3) Now, locate “Chromium” from the list of programs and right-click on it, then click on “Uninstall”.
Is Safari a virus?
It may seem like the iPhone’s main browser, Safari, has no risk of giving your phone a virus. However, no matter the method of browsing the internet, there’s always a chance it could happen. Although it’s incorrect to say that the iPhone can’t get a virus, it is true that iOS devices are generally more secure.
What is a chrome memory leak?
This is the outcome when you open multiple tabs in your browser, which in turn uses more RAM. Therefore, it may freeze or hang your device for a few minutes. Anyway, without wasting any time let’s see How to Fix Chrome Memory Leak & reduce high RAM usage with the help of the below-listed tutorial.
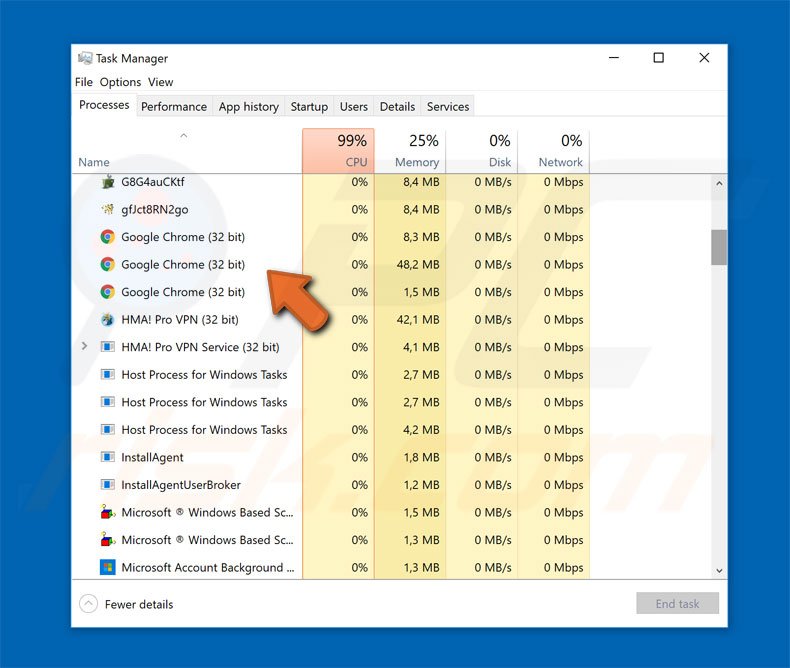
Why do I see multiple Chrome exe in Task Manager?
But if you open the Task Manager, you may be surprised to see many Google Chrome processes running. I could see 18 running even though I had opened only in one single window with 4 tabs. This is because Chrome opens a separate process for each of its tab, extension, tab and, subframe.
Why is Google Chrome taking up so much CPU?
Explaining Chrome’s CPU Usage These typically relate to your browsing behavior, including having too many tabs open at once, too many apps or browser extensions running and streaming high-quality video. Likewise, auto-playing videos, animations and excessive ads can also cause these problems.
Why Chrome opens multiple windows?
This issue can occur when the incorrect user profile has been corrupted or removed from the Google Chrome™ browser settings.
Should I uninstall Chromium?
In and of itself, Chromium is not malware and should not be removed immediately. We recommend investigating your process, as well as the Chromium folder to see any red flags that could point to a malware attack. There are certain types of malware that are capable of disguising themselves as software, incuding browsers.
How do I remove an exe virus from my computer?
Now to actually delete the virus from the system go to system32 folder and delete the regsvr.exe virus file from there (you will need to uncheck the option of “Hide Protected System Files and Folders” in Folder Options to view the virus file).
Can exe files be hacked?
One of the most common tricks used by hackers is to get unsuspecting users to click on a malicious .exe file which leads to malware being downloaded onto a computer. They’re usually sent to you as an email attachment with the email offering some form of compelling inducement to get you to open the attachment.