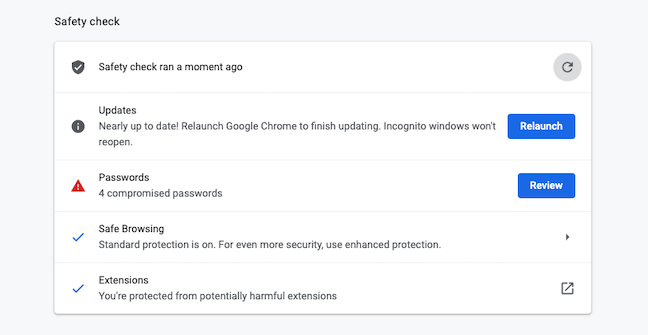
Safety check helps ensure the overall security and privacy of your browsing experience. It will notify you if any passwords saved in Chrome have been compromised, flag dangerous extensions, and make sure your security protections are up-to-date.
Why is Chrome giving me a security warning?
If you get this message, Chrome thinks that the web address may be for a different site than the one you expected. The message may also say “Is this the right site?” or “Fake site ahead.” You get this message when the site you try to visit: Appears similar to a safe site you usually visit.
What is Chrome safe and secure?
Chrome is secure by default, protecting you from dangerous and deceptive sites that might steal your passwords or infect your computer. Advanced technologies, such as site isolation, sandboxing, and predictive phishing protections, keep you and your data safe.
How long does Google safety check take?
Google Chrome will kick off the “Safety Check” test. Depending on how much browsing data you have, this can take anywhere from a few seconds to a couple of minutes. In this process, Google Chrome scans a total of four core modules to look for any malicious code and see if they are up to the mark.
What is Chrome safe and secure?
Chrome is secure by default, protecting you from dangerous and deceptive sites that might steal your passwords or infect your computer. Advanced technologies, such as site isolation, sandboxing, and predictive phishing protections, keep you and your data safe.
Is the Google Chrome Protection Alert legitimate?
“Google Chrome Warning Alert” is a fake error message displayed by a malicious website that users often visit inadvertently – they are redirected by various potentially unwanted programs (PUPs) that infiltrate systems without consent.
Is the Google virus warning real?
Google Security Alert/Warning is a fake alert issued by malicious websites. Like all social engineering, it’s designed to trick users into making an unsafe decision online. Chrome and Android devices have security alerts, but they aren’t labeled “Google Security Alert”.
Does Chrome have built in virus protection?
Does Chrome have inbuilt Antivirus? YES, Google Chrome comes with an inbuilt Malware scanner. It can search and report the malicious files and applications that are causing the trouble on your system or browser. However, this inbuilt anti-malware only comes with the Windows version of Google Chrome.
Why is Google telling me there is a data breach?
When you type your credentials into a website, Chrome will now warn you if your username and password have been compromised in a data breach on some site or app. It will suggest that you change them everywhere they were used. it does not matter on which website you see this new notification.
Why does Google keep telling me my passwords are compromised?
A Google Chrome password breach warning saying, “A data breach on a site or app exposed your password,” can strike fear in your heart. Chrome’s built-in password manager does this to alert you to a recent breach in which sensitive data such as your password may have been exposed.
Why does my Google search bar say encrypted for your safety?
That means that when you connect to Google Cloud, the data you send is encrypted using HTTPS, so that an adversary cannot snoop on your traffic. (You can find out more about HTTPS at Google in our HTTPS transparency report.)
Is Chrome good for privacy?
However, its privacy is lacking. Google Chrome is notorious for user data collection, tracking, and other privacy violations. One of its primary sources of revenue is user profiling for ad targeting. You can’t expect a very private browser from such a company.
Is Chrome safer than Safari?
Both browsers are pretty similar in security, but Chrome has a slight edge thanks to a host of customizable security extensions. The Safari password management trumps Chrome, though, and is invaluable for users of Apple devices.
Do I need to update Chrome?
Improved speed and performance. Chrome makes staying safe easy by updating automatically. This ensures you have the latest security features and fixes as soon as they’re available.
What is Chrome safe and secure?
Chrome is secure by default, protecting you from dangerous and deceptive sites that might steal your passwords or infect your computer. Advanced technologies, such as site isolation, sandboxing, and predictive phishing protections, keep you and your data safe.
How long does Google safety check take?
Google Chrome will kick off the “Safety Check” test. Depending on how much browsing data you have, this can take anywhere from a few seconds to a couple of minutes. In this process, Google Chrome scans a total of four core modules to look for any malicious code and see if they are up to the mark.
How can you tell a fake virus warning?
The Federal Trade Commission (FTC) warns that the scareware scam has many variations, but there are some telltale signs: You may get ads that promise to “delete viruses or spyware,” “protect privacy,” “improve computer function,” “remove harmful files,” or “clean your registry.”
What actually happens when you are notified by the browser that the site is not safe?
The latest version of Chrome also has a popup when you click the message that explains, “your connection to this site is not secure” and a warning about not entering any sensitive information on the site. The “Not Secure” warning means there is a lack of security for the connection to that page.
Why am I getting a virus warning from Google?
The Virus Warning Pop-Up on Android In most cases, Android users only see a fake virus warning pop-up when using the web browser to visit a malicious website. The pop-up window warns you that your Android is infected with a virus and invites you to tap a button to run a scan and remove the software from your device.
How long does it take for Chrome to check for harmful software?
Chrome generally takes two to five minutes to check for harmful software. You can speed up the process by clearing your cache first. If the CleanUp Tool detects any suspicious programs or extensions, it will prompt you to remove them.
Which is better Google or Google Chrome?
Those who are looking to find out information based on keywords or phrases will want to just use the Google search bar, but those who are looking to have multiple tabs open or are looking for a particular website will want to choose Google Chrome.
Did Google Chrome get hacked?
G oogle has announced that Google Chrome has been successfully hacked as it discovers 30 security flaws–seven of which pose a “high” threat to users. In a blog post, Google revealed that a new update will make improvements for Windows, Mac, and Linux, to fix the security issues after the hack.