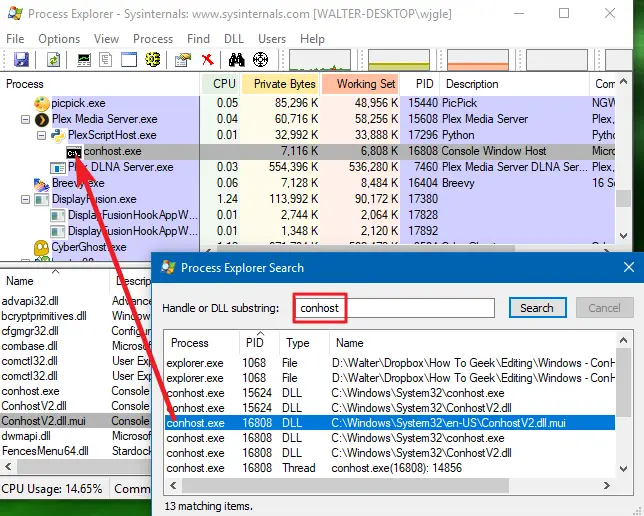
The conhost.exe (Console Windows Host) file is provided by Microsoft and is usually legitimate and completely safe. It can be seen running on Windows 11, Windows 10, Windows 8, and Windows 7. Conhost.exe is required to run in order for Command Prompt to interface with File Explorer.
Can I delete Conhost exe?
If you find that the conhost.exe file is a malicious one, you need to delete it. You can delete it manually or automatically through third-party software.
What is Conhost virus?
The Conhost Miner is a Trojan that utilizes a victim’s CPU, or processor, to mine the Monero (XMR) digital currency that utilize the CryptoNight hashing algorithm.
Where is Conhost exe stored?
Description: The original conhost.exe from Microsoft is an important part of Windows, but often causes problems. Conhost.exe is located in the C:\Windows\System32 folder.
Can I delete Conhost exe?
If you find that the conhost.exe file is a malicious one, you need to delete it. You can delete it manually or automatically through third-party software.
Why do I have so many Conhost exe running?
It’s even normal for this process to be running several times simultaneously (you’ll often see multiple instances of conhost.exe in Task Manager). However, there are situations where a virus could be masquerading as the conhost EXE file. One sign that it’s malicious or fake is if it’s using up lots of memory.
Is rundll32 exe a virus?
The rundll32.exe process is not a virus. However, it isn’t necessary that the process we observe in the Task Manager is the original process. At times virus or malware could be named rundll32.exe to conceal it.
Is Csrss a virus?
Is CSRSS.exe a virus? CSRSS.exe isn’t a virus. It’s a critical process used by Windows to control various elements of your operating system. Sometimes hackers may disguise malware as CSRSS.exe, but you can quickly check if your version is genuine.
How do I fix Conhost exe?
The built-in Windows option – Troubleshooter can also help to fix conhost.exe file errors. Go to Start> Settings> Update & Security> Troubleshoot and select the category you want to check. It’s recommended to run in Windows Safe Mode (Win+R>msconfig> Boot>Safe Boot field) and reboot the system.
What does csrss.exe do?
The csrss.exe process is an important part of the Windows operating system. Before Windows NT 4.0, which was released in 1996, csrss.exe was responsible for the entire graphical subsystem, including managing windows, drawing things on the screen, and other related operating system functions.
Is Csrss exe a virus?
Is CSRSS.exe a virus? CSRSS.exe isn’t a virus. It’s a critical process used by Windows to control various elements of your operating system. Sometimes hackers may disguise malware as CSRSS.exe, but you can quickly check if your version is genuine.
Is Service host a virus?
The svchost.exe (Service Host) file is a critical system process provided by Microsoft in Windows operating systems. Under normal circumstances, this file isn’t a virus but a crucial component in many Windows services. The purpose for svchost.exe is to, as the name would imply, host services.
Can I delete Conhost exe?
If you find that the conhost.exe file is a malicious one, you need to delete it. You can delete it manually or automatically through third-party software.
Where is Conhost exe stored?
Description: The original conhost.exe from Microsoft is an important part of Windows, but often causes problems. Conhost.exe is located in the C:\Windows\System32 folder.
Is Rundll32.exe malicious?
Rundll32.exe is a program used to run program code in DLL files which is part of Windows components. There are viruses that uses this name also that’s why it’s commonly mistaken as a real virus. There are also times that the file gets replaced with a malware infected one.
Why are there 2 csrss.exe running?
Distinguished. Having multiple instances of csrss.exe in the task manager is normal. There should be one instance of csrss.exe for system processes and another instance for interactive logons. If you have multiple users logged in, you can have even more instances of crss.exe in the Task Manager.
How do I remove csrss.exe Trojan?
Look for the csrss.exe file in the list of processes. Right-click on the file and select “Delete” from the context menu. If Windows prompts you with a message box, it means the file is not infected, so do not delete it.
Is Hkcmd exe a virus?
Hkcmd is a legitimate file, and it’s associated with Intel graphics. The file can usually be found on systems that are using Intel 810 and 815 chipsets. The actual Hkcmd file is located in the System32 subfolder in the Windows directory.
What is Wmiprvse exe?
The wmiprvse.exe process is the WMI Provider host. It’s a part of what’s known as the Windows Management Instrumentation (WMI) component within Microsoft Windows.
What is lsass.exe used for?
Local Security Authority Subsystem Service (Lsass.exe) is the process on an Active Directory domain controller. It’s responsible for providing Active Directory database lookups, authentication, and replication.
Why are there 2 csrss.exe running?
Distinguished. Having multiple instances of csrss.exe in the task manager is normal. There should be one instance of csrss.exe for system processes and another instance for interactive logons. If you have multiple users logged in, you can have even more instances of crss.exe in the Task Manager.
Is svchost.exe a Trojan?
If you see a process called svchost.exe *32 listed in Task Manager and it is utilizing a lot of the CPU, then you are most likely infected with a Miner Trojan. It has become a common tactic for Trojans to create Windows services that utilize svchost.exe to load a Miner Trojan DLL.