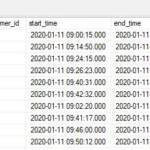
These are keys, which can be used to activate a product with py-kms (note this keys are provided officially by Microsoft).
What is GVLK product key?
Computers that activate with a KMS host need to have a specific product key. This key is sometimes referred to as the KMS client key, but it is formally known as a Microsoft Generic Volume License Key (GVLK).
What is my KMS host key?
What is a KMS Host Key. A KMS Key is used to activate the KMS host computer with a Microsoft activation server and can activate up to six KMS hosts with 10 activations per host. Each KMS host can activate an unlimited number of computers.
How do I get a KMS key?
To get the KMS key, sign in to the Volume Licensing Service Center (VLSC) and download the KMS key for each product and version of Office that you want KMS to activate.
What is Csvlk key type?
KMS host keys A KMS host needs a key that activates, or authenticates, the KMS host with Microsoft. This key is usually referred to as the KMS host key, but it is formally known as a Microsoft Customer Specific Volume License Key (CSVLK).
What is GVLK product key?
Computers that activate with a KMS host need to have a specific product key. This key is sometimes referred to as the KMS client key, but it is formally known as a Microsoft Generic Volume License Key (GVLK).
Is KMS client key safe?
No, it isn’t safe to use either kms activation or any other activation software, specially if they use (as you said) unknown host server beacause this will provide them a kind of backdore to your system by which they might track your files or sensitive information.
How do I download KMS client key?
Click Install product key in the Selected Items menu in the right-side pane to display the Install Product Key dialog box. The Install Product Key dialog box displays the keys that are available to be installed. Select the Automatically select an AD or KMS client key option and then click Install Key.
Where are KMS keys stored?
AWS managed KMS keys that are created on your behalf by other AWS services to encrypt your data are always generated and stored in the AWS KMS default key store.
How do I connect to KMS server?
Install and configure a KMS host Select Key Management Service (KMS) as the activation type and enter localhost to configure the local server or the hostname of the server you want to configure. Select Install your KMS host key and enter the product key for your organization, then select Commit.
What is the default KMS key?
A KMS default master key is used by an AWS service such as RDS, EBS, Lambda, Elastic Transcoder, Redshift, SES, SQS, CloudWatch, EFS, S3 or Workspaces when no other key is defined to encrypt a resource for that service. The default key cannot be modified to ensure its availability, durability and security.
What is the full form of KMS?
KMS, an abbreviation of Knowledge Management System, was a commercial second generation hypermedia system, originally created as a successor for the early hypermedia system ZOG.
How long does a Key Management Service KMS activation last?
KMS activations are valid for 180 days, a period known as the activation validity interval. KMS clients must renew their activation by connecting to the KMS host at least once every 180 days to stay activated. By default, KMS client computers attempt to renew their activation every seven days.
What is a KMS activator?
What is difference between MAK and KMS license?
Key Management Service (KMS) allows organizations to activate systems within their own network. Multiple Activation Key (MAK) activates systems on a one-time basis, using Microsoft’s hosted activation services.
What is Volume Activation Management Tool?
The Volume Activation Management Tool (VAMT) enables network administrators and other IT professionals to automate and centrally manage the Windows®, Microsoft® Office, and select other Microsoft products volume and retail-activation process.
What is GVLK product key?
Computers that activate with a KMS host need to have a specific product key. This key is sometimes referred to as the KMS client key, but it is formally known as a Microsoft Generic Volume License Key (GVLK).
Is KMS activator a virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
Is KMS activation legal?
Activation servers (KMS) through an organization or educational institution is legal, and should be used for those intents and purposes.
Is KMS genuine?
Yes, KMS activation is illegal for Windows. If you activate through the KMS method then your copy of Windows would not be considered genuine by Windows.
How do I activate Windows 10 without a product key?
One of the first screens you’ll see will ask you to enter your product key so you can “Activate Windows.” However, you can just click the “I don’t have a product key” link at the bottom of the window and Windows will allow you to continue the installation process.
What are the 3 types of KMS keys?
Choosing a KMS key type. AWS KMS supports several types of KMS keys: symmetric encryption keys, symmetric HMAC keys, asymmetric encryption keys, and asymmetric signing keys. KMS keys differ because they contain different cryptographic key material.