What is a KMS Host Key. A KMS Key is used to activate the KMS host computer with a Microsoft activation server and can activate up to six KMS hosts with 10 activations per host. Each KMS host can activate an unlimited number of computers.
How do I find my KMS key?
To get the KMS key, sign in to the Volume Licensing Service Center (VLSC) and download the KMS key for each product and version of Office that you want KMS to activate.
What is KMS client key?
To use KMS, you need to have a KMS host available on your local network. Computers that activate with a KMS host need to have a specific product key. This key is sometimes referred to as the KMS client key, but it is formally known as a Microsoft Generic Volume License Key (GVLK).
How do I activate my KMS key?
Open the command prompt, type slmgr /ipk followed by the 25-digit KMS host product key and press Enter. Then, use slmgr /ato to activate the host key.
How do I download KMS client key?
Click Install product key in the Selected Items menu in the right-side pane to display the Install Product Key dialog box. The Install Product Key dialog box displays the keys that are available to be installed. Select the Automatically select an AD or KMS client key option and then click Install Key.
Where do I get my Windows 10 product key?
Generally, if you bought a physical copy of Windows, the product key should be on a label or card inside the box that Windows came in. If Windows came preinstalled on your PC, the product key should appear on a sticker on your device. If you’ve lost or can’t find the product key, contact the manufacturer.
How long does a KMS activation last?
According to the Microsoft article: Understanding KMS, in the KMS Activation Renewal section, it states that “KMS activations are valid for 180 days—the activation validity interval. To remain activated, KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days.”.
How do I connect to KMS server?
Install and configure a KMS host Select Key Management Service (KMS) as the activation type and enter localhost to configure the local server or the hostname of the server you want to configure. Select Install your KMS host key and enter the product key for your organization, then select Commit.
Where is KMS?
Kerkhoven-Murdock-Sunburg School District is located in central Minnesota and includes the cities of Kerkhoven, Murdock and Sunburg abbreviated as KMS.
What is the KMS service name?
The Microsoft Key Management Server (KMS) is part of the Microsoft Volume Activation 2.0 solution managing Windows OS activation keys and performs activation for supported clients automatically.
Is KMS activator a virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
How does Microsoft KMS work?
What is the Key Management Service (KMS) The Key Management Service (KMS) is an activation service that allows organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation.
How can I activate Windows 10 for free?
To activate Windows, you need a digital license or a product key. If you’re ready to activate, select Open Activation in Settings. Click Change product key to enter a Windows product key. If Windows was previously activated on your device, your copy of Windows 10 or Windows 11 should be activated automatically.
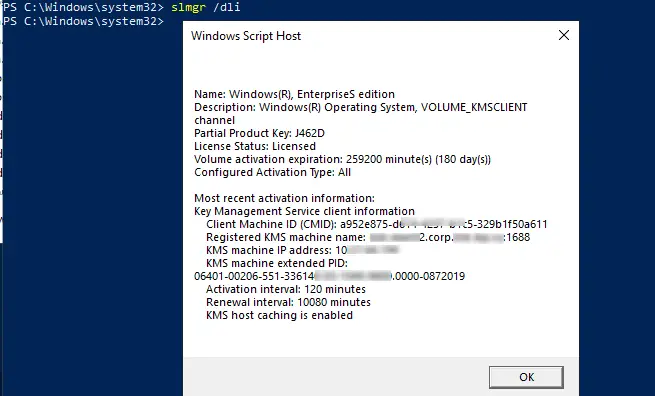
How do I find my KMS server Windows 10?
On a client computer or the KMS host, open an elevated Command Prompt window, type Slmgr. vbs /dlv, and then press ENTER. The /dlv command displays the detailed licensing information. The response should return an error that states that the KMS activation count is too low.
Is Windows product ID Same as key?
No the Product ID is not the same as your Product key. You need a 25 character “Product Key” to activate Windows. The Product ID just identifies which version of Windows you have.
Can you reuse a Windows 10 key?
Generally speaking, you do not have a limit on the number of times you can transfer a license as long as you deactivate the previous installation, so you’re not using the same product key on more than one system.
Do KMS keys expire?
Keys generated by AWS KMS do not have an expiration time and cannot be deleted immediately; there is a mandatory 7 to 30 day wait period.
What happens when KMS activation expires?
After each successful connection, the expiration is extended out to the full 180 days. What happens if Windows cannot reactivatethelicense? If a Windows computer has not been able to reestablish communication to the KMS server after 180 days, the machine will become unlicensed.
What is a KMS server?
KMS (Key Management Service) is one of the methods to activate Microsoft Windows and Microsoft Office. Activation ensures that the software is obtained from and licensed by Microsoft. KMS is used by volume license customers, usually medium to large businesses, schools, and non-profits.
What is KMS file?
A KMS file is a data file created by Correlate Client, a Windows program used to create shortcuts to files and organize them in one document. It contains a structure of one or more shortcuts to files. KMS files are commonly used to store links to business, human resource, project, and productivity-related files.
How do I find my KMS server IP address?
Answers. Look for the KeyManagementServiceName data and this should return your KMS server. Do a ping of this and it should then return you the IP address of the KMS server. Run “slmgr /dlv” and you will get the KMS host name.
How do I delete KMS server?
Procedure. Select Configuration > System Settings > Key Management Server. The Key Management Server page appears and shows all key management servers that have been configured. Select the radio button for the KMS you want to remove, and select Remove.