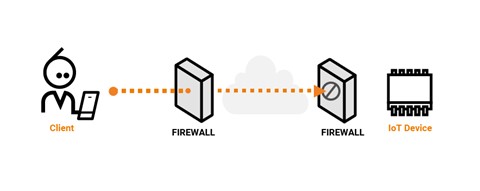
TCP tunnel is a technology that aggregates and transfers packets sent between end hosts as a single TCP connection. By using a TCP tunnel, the fairness among aggregated flows can be improved and several protocols can be transparently transmitted through a firewall.TCP tunnel is a technology that aggregates and transfers packets sent between end hosts as a single TCP connection. By using a TCP tunnel, the fairness among aggregated flows can be improved and several protocols can be transparently transmitted through a firewall.
What is meant by TCP tunneling?
TCP-tunneling using AnyDesk is geared towards forwarding any TCP-based protocol between the local and remote clients so that the local client can access the services/devices accessible by the remote client. For this feature to work, it requires an active AnyDesk connection between the local and remote clients.
How do I create a TCP tunnel?
Go to Configuration > Services > Proxy Services and create a New Service. Configure the Proxy Settings to be TCP Tunnel and add relevant listening ports for destination. Once configured, save this service and ensure it is intercepted.
What is tunneling in IOT?
Tunneling is a technique that enables remote access users to connect to a variety of network resources (Corporate Home Gateways or an Internet Service Provider) through a public data network.
What is meant by TCP tunneling?
TCP-tunneling using AnyDesk is geared towards forwarding any TCP-based protocol between the local and remote clients so that the local client can access the services/devices accessible by the remote client. For this feature to work, it requires an active AnyDesk connection between the local and remote clients.
What is difference between tunneling and port forwarding?
Tunneling, also known as “port forwarding,” is the transmission of data intended for use only within a private, usually corporate network through a public network in such a way that the routing nodes in the public network are unaware that the transmission is part of a private network.
Why do we use tunneling?
Tunneling is often used in virtual private networks (VPNs). It can also set up efficient and secure connections between networks, enable the usage of unsupported network protocols, and in some cases allow users to bypass firewalls.
What TCP means?
Transmission Control Protocol (TCP)
What is tunneling proxy server?
HTTP tunneling is used to create a network link between two computers in conditions of restricted network connectivity including firewalls, NATs and ACLs, among other restrictions. The tunnel is created by an intermediary called a proxy server which is usually located in a DMZ.
What is TCP forwarding in SSH?
SSH port forwarding, or TCP/IP connection tunneling, is a process whereby a TCP/IP connection that would otherwise be insecure is tunneled through a secure SSH link, thus protecting the tunneled connection from network attacks. Port forwarding can be used to establish a form of a virtual private network (VPN).
Is SSH UDP or TCP?
Is SSH over TCP or UDP? SSH usually runs over TCP. That being said, RFC 4251 specifies that SSH transmission layer protocol “might also be used on top of any other reliable data stream”. SSH protocol’s default settings are to listen on TCP port 22 for connections.
What is UDP tunnel?
This networking mode enables you to interconnect virtual machines running on different hosts. Technically this is done by encapsulating Ethernet frames sent or received by the guest network card into UDP/IP datagrams, and sending them over any network available to the host.
Which tools are tunneling protocols?
Tunneling protocols, such a GRE and L2TP, are common tools for interconnecting two similar networks over a different network.
How long does it take for a tunneling wound to heal?
The wound usually heals within four weeks, and many people don’t require any further treatment.
What is tunneling process explain in detail with example?
What Does Tunneling Mean? Tunneling is a protocol that allows for the secure movement of data from one network to another. Tunneling involves allowing private network communications to be sent across a public network, such as the Internet, through a process called encapsulation.
What TCP means?
Transmission Control Protocol (TCP)
Which tools are tunneling protocols?
Tunneling protocols, such a GRE and L2TP, are common tools for interconnecting two similar networks over a different network.
What is meant by TCP tunneling?
TCP-tunneling using AnyDesk is geared towards forwarding any TCP-based protocol between the local and remote clients so that the local client can access the services/devices accessible by the remote client. For this feature to work, it requires an active AnyDesk connection between the local and remote clients.
Is IP tunneling port forwarding?
It involves receiving traffic at one port and forwarding it to another port and can be done both locally or remotely. Tunneling is a Port Redirection technique that uses encrypted tunnels within the SSH protocol. Tunneling is a type of communication between two network devices using an SSH connection.
Is SSH a tunnel?
SSH tunneling, or SSH port forwarding, is a method of transporting arbitrary data over an encrypted SSH connection. SSH tunnels allow connections made to a local port (that is, to a port on your own desktop) to be forwarded to a remote machine via a secure channel.
How does the TCP work?
How exactly do TCP connections work? TCP allows for transmission of information in both directions. This means that computer systems that communicate over TCP can send and receive data at the same time, similar to a telephone conversation. The protocol uses segments (packets) as the basic units of data transmission.
Why TCP is used with IP?
TCP is used in conjunction with IP in order to maintain a connection between the sender and the target and to ensure packet order. For example, when an email is sent over TCP, a connection is established and a 3-way handshake is made.
What is a tunneling protocol?
In computer networks, a tunneling protocol is a communications protocol that allows for the movement of data from one network to another.
What is TCP tunneling and what are some examples?
For example, in video devices, TCP tunneling is often used to send and receive imagery between an existing video player client and a TCP video streaming service such as an RTSP server on an IP camera. Meanwhile, secure remote access to existing HTTP services is popular in providing remote access to admin applications.
What is contributor tunneling and how does it work?
TechTarget Contributor Tunneling, also known as “port forwarding,” is the transmission of data intended for use only within a private, usually corporate network through a public network in such a way that the routing nodes in the public network are unaware that the transmission is part of a private network.
What is a tunnel and how does it work?
Tunneling works by encapsulating packets: wrapping packets inside of other packets. (Packets are small pieces of data that can be re-assembled at their destination into a larger file.) Tunneling is often used in virtual private networks (VPNs).