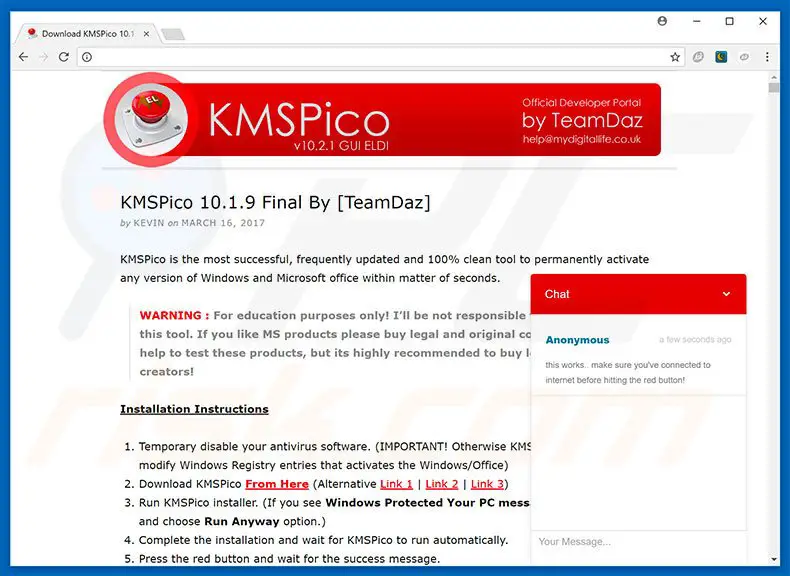
KMSPico is a tool used to activate a copy of the Windows OSsoftware that is acquired illegally. Doing so is unlawful under almost all circumstances and could have legal repercussions. Cracktools are often downloaded from sites of a shady nature.
Is KMSPico a malware?
KMSPico Malware is a hacking program that claims to be a Microsoft Windows and Office activator. It is extensively disseminated under a variety of names and variants on phoney download sites and file-sharing networks like BitTorrent.
Why is KMSPico on my computer?
What is KMSPico Virus? KMSPico is an illegal, unsafe tool that cybercriminals have developed to activate unregistered Microsoft products for free. It does this by bypassing Microsoft’s KMS (key management system) protocols and replacing the key with a newly generated key that postpones the activation.
How do I get rid of KMSPico virus?
The safest way to remove the intruder from your computer and get rid of OS-related problems is to run a full system scan with professional anti-malware software, such as SpyHunter 5 or Malwarebytes.
What if I uninstall KMSPico?
Yes you can remove KMSpico but dont do it. You may have activated windows or ms office with kmspico now you think that it is useless, no its not like this, to keep your windows activated do not remove kmspico. If you remove it then your windows will go again in trail mode.
Is KMSPico a malware?
KMSPico Malware is a hacking program that claims to be a Microsoft Windows and Office activator. It is extensively disseminated under a variety of names and variants on phoney download sites and file-sharing networks like BitTorrent.
Is KMSpico a hack tool?
KMSpico is Malwarebytes’ detection name for a Hacktool that allows the user to use Microsoft software illegally.
Is KMSpico trusted?
KMSpico is trustworthy software, but only if you download KMSpico from a legit source. It can help you activate windows and Microsoft Office products for free. KMSpico is regularly updated and maintained which makes it trustworthy and safe.
Is kms activator a virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
Is KMSPico a mine?
The actual KMSPico which was on a thread on MyDigitalLife contains no such miner. Download from another source, besides a copy on the Web Archive of the thread from MyDigitalLife, and you may find something else.
Can I delete AutoKMS after activation?
AutoKMS is not really a virus, but a hack tool downloaded intentionally by most users who try to activate unregistered Microsoft products. In order to get rid of it, you can try to uninstall it as you do with any other application.
Is kms activator legal?
No, they are not legal. Be aware of those KMS, some of them might include virus/malware that might damage your PC.
What is the password of KMSPico?
KM Spico Password: 12345.
How do I stop windows Defender from detecting KMSPico?
Go to Start > Settings > Update & Security > Windows Security > Virus & threat protection. Under Virus & threat protection settings, select Manage settings, and then under Exclusions, select Add or remove exclusions. Select Add an exclusion, and then select from files, folders, file types, or process.
Can Malwarebytes remove kms?
Malwarebytes can detect and remove RiskWare. KMS without further user interaction.
Is it safe to use KMS activator?
Angelo B37. Microsoft’s Defender will find the KMS activater as a threat and other antivirus software will also do it. We have no information if this kind of tools have malware, we simply advise not to use it. If you do want to use illegal software please use it at your own risk.
Is kms activator legal?
No, they are not legal. Be aware of those KMS, some of them might include virus/malware that might damage your PC.
Is KMSPico a mine?
The actual KMSPico which was on a thread on MyDigitalLife contains no such miner. Download from another source, besides a copy on the Web Archive of the thread from MyDigitalLife, and you may find something else.
Which is the official KMSPico site?
You can get an authentic version of KMS Pico from it’s origin, forums. mydigitallife.
Is KMSPico a malware?
KMSPico Malware is a hacking program that claims to be a Microsoft Windows and Office activator. It is extensively disseminated under a variety of names and variants on phoney download sites and file-sharing networks like BitTorrent.
Is AutoKMS a virus Reddit?
Win32/AutoKMS is not malware. It is a component of a system for activating Volume License copies of Microsoft Office.
How do I install KMS?
Install and configure a KMS host Select Key Management Service (KMS) as the activation type and enter localhost to configure the local server or the hostname of the server you want to configure. Select Install your KMS host key and enter the product key for your organization, then select Commit.