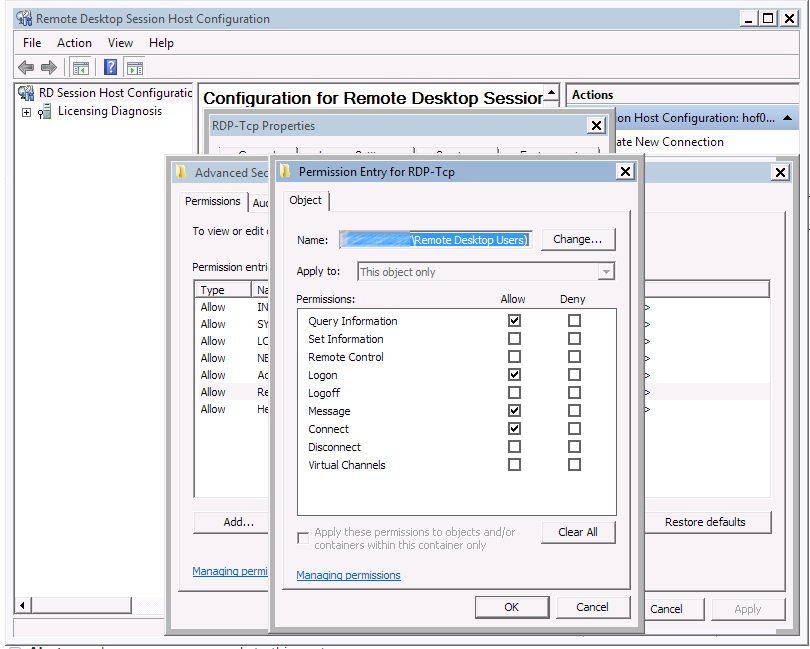
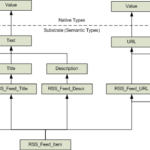
By default, the Remote Desktop Users group is assigned the following permissions: Query Information, Logon, and Connect.
What is RDP permission?
Allow Access to Use Remote Desktop Connection Before Remote Desktop can be used, permission has to be granted to the specific accounts that you would like to Allow to connect to your computer remotely. This is typically done on your Office Computer.
Does remote desktop require admin rights?
As per my knowledge, if you want your user to access the server remote session then it’s not compulsory that they should be added under administrator group. But you must add the user under “Remote Desktop User” local group.
How do I give a user permission to remote desktop?
Right-click on “Computer” and select “Properties”. Select “Remote Settings”. Select the radio button for “Allow remote connections to this computer”. The default for which users can connect to this computer (in addition to the Remote Access Server) is the computer owner or administrator.
What is RDP permission?
Allow Access to Use Remote Desktop Connection Before Remote Desktop can be used, permission has to be granted to the specific accounts that you would like to Allow to connect to your computer remotely. This is typically done on your Office Computer.
Can remote desktop be monitored?
A: YES, your employer can and has the right to monitor your Citrix, Terminal, and Remote Desktop sessions.
How can I tell who is accessing my Remote Desktop?
The easiest way to determine who has access to a particular Windows machine is to go into computer management (compmgmt. msc) and look in Local Users and Groups. Check the Administrators group and the Remote Desktop Users group to see who belongs to these.
Who needs domain admin rights?
Membership in Domain Admins is rarely a valid requirement. Those members have full administrative rights to all workstations, servers, Domain Controllers, Active Directory, Group Policy, etc., by default. This is too much power for any one account, especially in today’s modern enterprise.
Do local admins have RDP access?
Administrators have access via RDP enabled by default. However you may need to restrict remote access for a specific administrator: if you want to be sure that every task (backups for example), services or other operations that may launch using his credentials won’t stop working.
How can I tell who is accessing my Remote Desktop?
The easiest way to determine who has access to a particular Windows machine is to go into computer management (compmgmt. msc) and look in Local Users and Groups. Check the Administrators group and the Remote Desktop Users group to see who belongs to these.
What is built in Remote Desktop Users group?
The Remote Desktop Users group allows members to connect remotely to servers in the domain. Being able to remotely log on to the DC allows them to perform actions as if they were physically sitting at the server and working on it. Because of the power this group gives members, it has no default members.
What is RDP and how it works?
Remote desktop protocol (RDP) is a secure network communications protocol developed by Microsoft. It enables network administrators to remotely diagnose problems that individual users encounter and gives users remote access to their physical work desktop computers.
What is RDP permission?
Allow Access to Use Remote Desktop Connection Before Remote Desktop can be used, permission has to be granted to the specific accounts that you would like to Allow to connect to your computer remotely. This is typically done on your Office Computer.
Is Remote Desktop private?
When accessing your business computer from a remote computer using Windows Remote Desktop protocol, you can set it to public or private mode.
Can VPN stop remote access?
Virtual Private Network (VPN) Because internet traffic and user identity are protected with encryption, VPN is technically a security solution, although it does enable remote network access, whether users are working from home, a coffee shop, or an airport.
Is RDP secure without VPN?
Connecting to a network via Remote Desktop Protocol (RDP)/Terminal Services without a VPN is very dangerous. I’m amazed by how many companies allow RDP (TCP Port 3389) into their networks without first establishing a VPN to protect this (and other) traffic.
Can someone remotely access my computer without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
What is the difference between domain admin and Local admin?
You see, the limitation is that the Domain Administrator cannot do anything outside of the domain. A Local Administrator is already outside the domain and has the full power to do anything desired on the location machine, which IS PART of the domain.
How many domain admins is too many?
Should users be local admins?
Local accounts with administrator privileges are considered necessary to be able to run system updates, software upgrades, and hardware usage. They are also helpful to gain local access to machines when the network goes down and when your organization faces some technical glitches.
Can someone remotely access my computer without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
How do I manage RDS users?
In Server Manager click Remote Desktop Services > Overview, and then click a specific collection. Under Properties, click Tasks > Edit properties. Click User groups. Click Add and enter the user or group that you want to have access to the collection.
What are Remote Desktop Services permissions?
Remote Desktop Services permissions can be granted, or set, for individual users or groups. Users can also inherit permissions as a result of being a group member. The denial of a permission, however, overrides an inherited permission. For example, members of the Remote Desktop Users (RDU) group are granted the Query permission by default.
What is the Remote Desktop Access Policy?
Reference This policy setting determines which users or groups can access the logon screen of a remote device through a Remote Desktop Services connection. It is possible for a user to establish a Remote Desktop Services connection to a particular server but not be able to log on to the console of that same server.
How to control who can open a Remote Desktop Services connection?
Not Defined Best practices To control who can open a Remote Desktop Services connection and log on to the device, add users to or remove users from the Remote Desktop Users group. Location Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment Default values
What is the difference between the administrators and remote desktops users groups?
By default, members of the Administrators group have this right on domain controllers, workstations, and servers. The Remote Desktops Users group also has this right on workstations and servers.