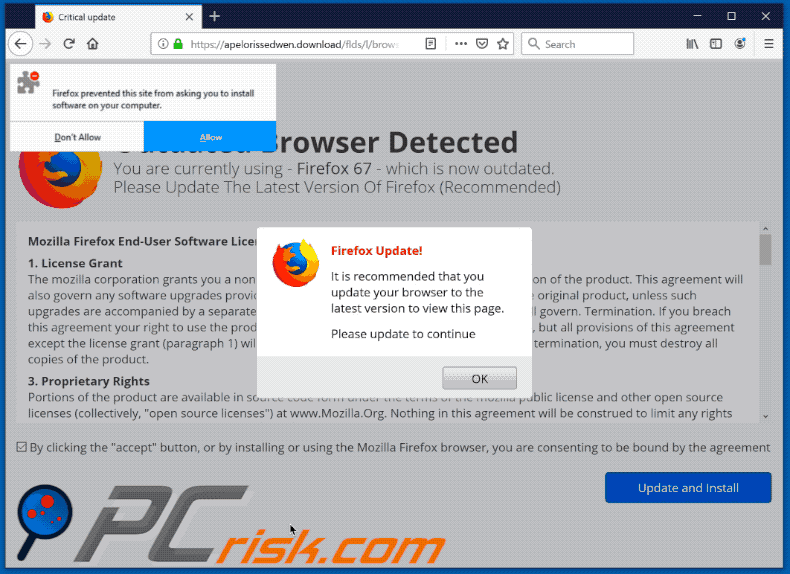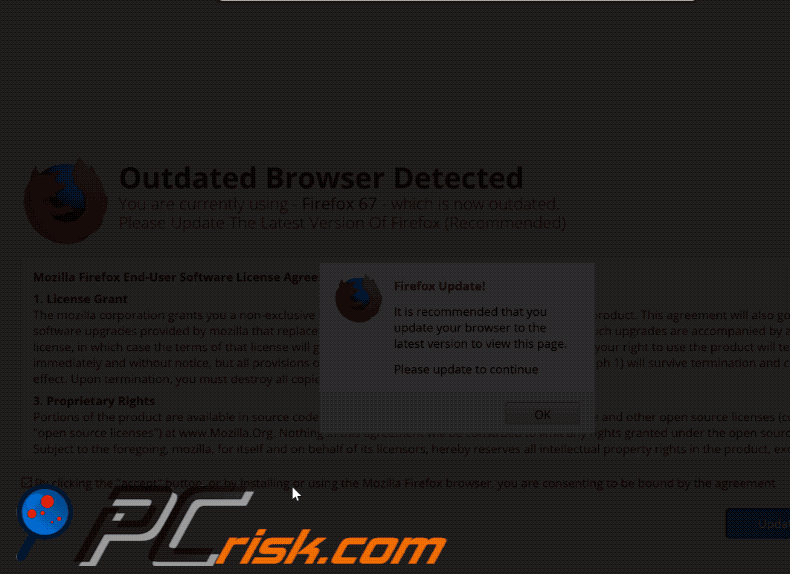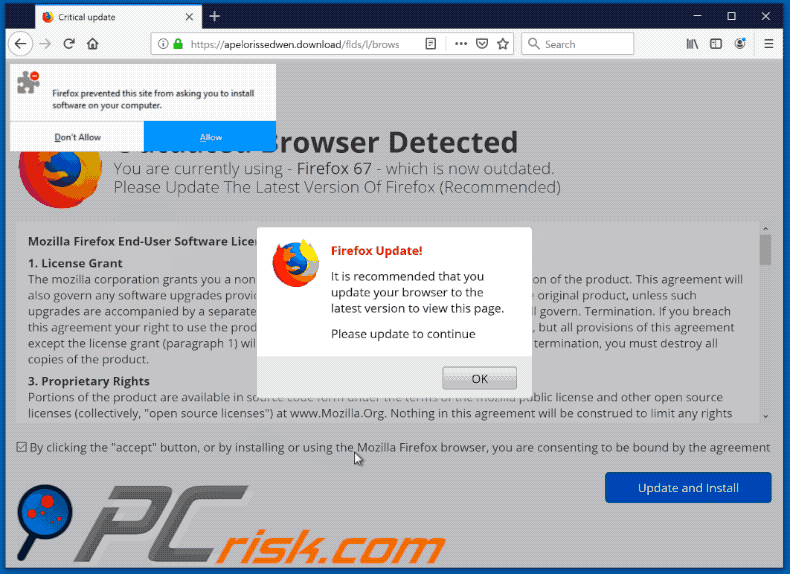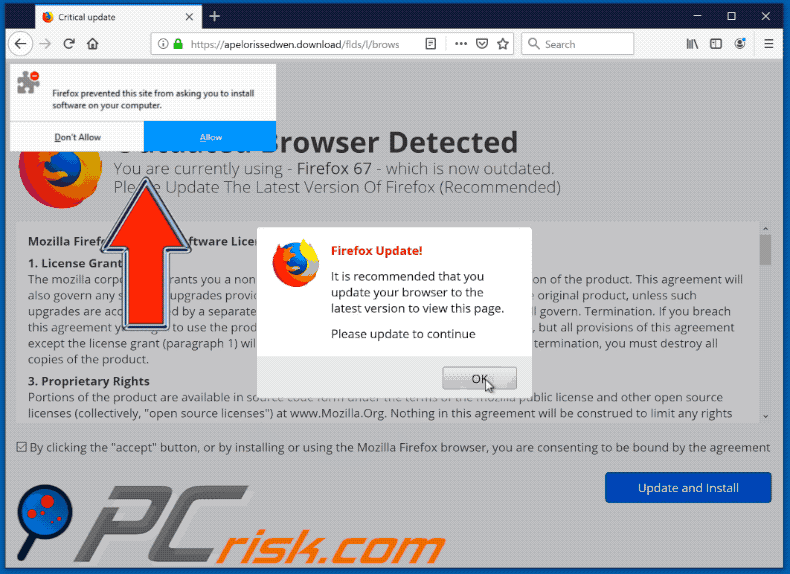
What should you do if you are worried about using a potentially outdated Internet browser? Contact the help desk or your security team if you have questions about the use or status of your system’s software.
Why should you not attempt to fix a hacked computer device or work account by yourself?
If the computer or device was provided to you by your employer or is used for work, do not try to fix the problem yourself. Not only can you cause more harm than good, but you could also destroy valuable evidence that can be used for an investigation.
Why do cyber attackers commonly use social engineering attacks?
Social engineering is a popular tactic among attackers because it is often easier to exploit people than it is to find a network or software vulnerability. Hackers will often use social engineering tactics as a first step in a larger campaign to infiltrate a system or network and steal sensitive data or disperse …
Why is it important to use a strong unique passphrase for each of your social networking accounts?
If the password is reused, they can gain access to further accounts. This is why unique passwords are so important. Additionally, when hackers can’t easily find or a guess the password, they may use a technique called brute forcing.
What should you do if you discover you are using an outdated browser quizlet?
What should you do if you are worried about using a potentially outdated Internet browser? Contact the help desk or your security team if you have questions about the use or status of your system’s software.
Who is the No 1 hacker in world?
Kevin Mitnick is the world’s authority on hacking, social engineering, and security awareness training. In fact, the world’s most used computer-based end-user security awareness training suite bears his name. Kevin’s keynote presentations are one part magic show, one part education, and all parts entertaining.
Which of the following is the most effective strategy for protecting against an insider threat?
1: Monitor User Behavior The most effective counter to the Insider Threat is to monitor user behavior in real-time to predict and detect abnormal user behavior associated with potential sabotage, data theft or misuse.
What technology can prevent a hacker from using your computer when you don’t have it with you?
Firewalls. A firewall is a software program or piece of hardware that blocks hackers from entering and using your computer. Hackers search the internet the way some telemarketers automatically dial random phone numbers.
Why is IT important to follow your security policies for making sure any browser plugin?
The more plugins (or add-ons) a browser has installed, the greater the attack surface, the more likely a threat can find a vulnerability. In fact, most browser based attacks now adays do not target the browser itself but plugins. In addition, we want to ensure that whatever plugins we have installed our always current.
What is best control to handle social engineering attacks ensuring that anti virus is updated ensuring firewall is deployed awareness?
In a case like social engineering where victims are subject to spear phishing attacks, phishing attacks, malicious emails, and compromised sites, it is good to have a spam firewall and web filter in place to mitigate those threats before they even reach the network.
What technology can prevent a hacker from using computer when you don’t have it with you?
Firewalls. A firewall is a software program or piece of hardware that blocks hackers from entering and using your computer. Hackers search the internet the way some telemarketers automatically dial random phone numbers.
What can someone do with your Microsoft account?
If someone gets access to your Microsoft account, they may be able to use your email to reset the passwords for your other accounts, like banking and online shopping. You can change your password on the Security basics page at any time. Do make the new password significantly different from previous passwords.
Does Microsoft protect my computer?
When you start Windows for the first time, Microsoft Defender Antivirus is on and actively helping to protect your PC by scanning for malware (malicious software), viruses, and other threats. Microsoft Defender uses real-time protection to scan everything you download or run on your PC.
Why is it important to update your mobile device to have the latest versions of its operating system and applications quizlet?
Why is it important to update your mobile device to have the latest versions of its operating system and applications? It provides access to new security features and fixes for known vulnerabilities.
Which of the following provides the most protection against malware encryption keyloggers updates?
Bitdefender is a very fast and accurate antivirus that provides excellent protection against a wide range of malware, including really well-hidden keyloggers.
Which country has most powerful hackers?
China. By quite a significant margin, China houses the largest number of hackers on Earth.
Who is Earth’s most wanted hacker?
Who hacked NASA?
A British man facing charges of hacking into top secret Pentagon and NASA computers in the U.S. has lost a long legal battle against his extradition from the U.K. to the U.S. American prosecutors say the man, Gary McKinnon, is a major military computer hacker.
Which of the following countermeasures can you implement to help reduce technology insider threats?
1 Answer. Inventory your technology holdings; use strong passwords, prevent unauthorized access, and watch for behavioral indicators are countermeasures that can help reduce technology-associated insider threats.
What technology should be used to secure your data to mitigate the damage?
Use data encryption on laptops and notebook computers Using a whole-disk encryption program is the best safeguard against unauthorized access of data on your laptop or notebook computer. Such applications use strong encryption methods that protect your device’s hard drive while allowing you easy access to your data.
What technology would prevent an unauthorized person from accessing your data?
You can use a VPN layer between the users and the system or implement an SSL/TLS to encrypt network traffic. Inside the system, communications can be secured using IPsec, SSL/TLS, or some other VPN technology.
What technology can prevent a hacker from using your computer when you don’t have it with you?
Firewalls. A firewall is a software program or piece of hardware that blocks hackers from entering and using your computer. Hackers search the internet the way some telemarketers automatically dial random phone numbers.