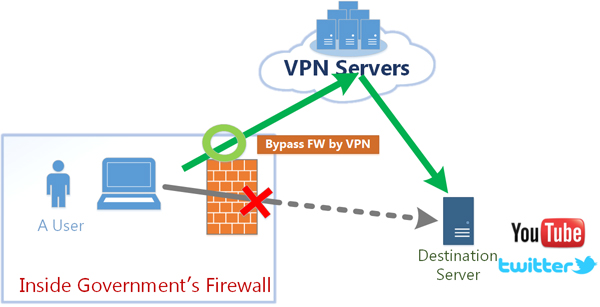
OpenVPN is the most reliable, safe, and flexible protocol and will stop any firewall from standing in your way. Aside from choosing a service with OpenVPN, make sure it has 256-bit AES encryption as well as DNS and IPv6 leak protection.
Which VPN can bypass firewall?
OpenVPN is the most reliable, safe, and flexible protocol and will stop any firewall from standing in your way. Aside from choosing a service with OpenVPN, make sure it has 256-bit AES encryption as well as DNS and IPv6 leak protection.
Can VPN break firewall?
The most commonly used technology to bypass egress firewalls is Virtual Private Network (VPN). In particular, this technology is widely used by smartphone users that are affected by egress filtering; there are many VPN apps (for Android, iOS, and other platforms) that can help users bypass egress firewalls.
Can VPN break firewall?
The most commonly used technology to bypass egress firewalls is Virtual Private Network (VPN). In particular, this technology is widely used by smartphone users that are affected by egress filtering; there are many VPN apps (for Android, iOS, and other platforms) that can help users bypass egress firewalls.
Should VPN be behind firewall?
The most common approach is to place the VPN server behind the firewall, either on the corporate LAN or as part of the network’s “demilitarized zone” (DMZ) of servers connected to the Internet. Geography is extremely important when configuring and troubleshooting VPN connections that pass through firewalls.
Is it possible to hack a firewall?
A hacker can penetrate your firewall/router and connect to a particular port, although the firewall should have never forwarded that port. Visiting a simple web page without requiring any authentication, XSS, or user input, can easily circumvent your security.
Who destroys firewall?
To destroy a firewall, from the Networking section of the control panel, click the Firewalls tab. Open the More menu of the firewall you want to destroy and click Destroy. In the Destroy Firewall window that opens, click Confirm to destroy the firewall.
Is it possible to bypass firewalls?
Use a VPN to Encrypt Your Traffic VPNs, on the other hand, allow you to bypass school firewalls by encrypting your traffic. Proxies get around the restrictions by giving you the banned website via a whitelisted one, but a VPN protects you by not allowing the firewall to see your browsing in the first place.
Can Windows Firewall be hacked?
A firewall may be secure, but if it’s protecting an application or operating system with vulnerabilities, a hacker can easily bypass it. There are countless examples of software vulnerabilities that hackers can exploit to bypass the firewall.
Can VPN break firewall?
The most commonly used technology to bypass egress firewalls is Virtual Private Network (VPN). In particular, this technology is widely used by smartphone users that are affected by egress filtering; there are many VPN apps (for Android, iOS, and other platforms) that can help users bypass egress firewalls.
Can a firewall block a virus?
A firewall will not protect you from viruses and other malware. A firewall limits outside network access to a computer or local network by blocking or restricting ports. Firewalls help prevent your computer from communicating with other computers on the network and Internet.
Can a network engineer hack?
Can a software engineer prevent against hacking? While software engineers can do everything they can to make a system more secure, it is not possible for them to prevent hacking.
How can I test my firewall?
You can do this either by clicking Action Centre in the Control Panel or by clicking the small white flag that appears in the System Tray in the bottom right hand corner of the computer Desktop. Click Security and, next to Network Firewall, it should say On. If not, there will be a link to click to switch it on.
Can antivirus stop hackers?
In Summary. Antivirus software can help stop hackers, but only to a certain extent. No antivirus offers 100 percent protection, so while antivirus is not the only way to stop hackers, it’s still a critical component of your digital security.
How do viruses get past firewalls?
Encrypted Injection Attacks Put simply, a firewall with DPI will inspect all of the data packets entering and leaving your network to check for malicious code, malware, and other network security threats. Encrypted injection attacks are usually delivered via phishing emails.
What type of firewall is Fortinet?
Fortinet’s FortiGate next-generation firewalls (NGFW) provide organizations supreme protection against web-based network threats, including known and unknown threats and intrusion strategies.
Does DMZ bypass firewall?
A DMZ helps electronic signals bypass strict firewall and router security and open all ports for faster delivery of data packets.
Can Windows Defender stop hackers?
Microsoft’s Defender is pretty good at detecting malware files, blocking exploits and network-based attacks, and flagging phishing sites. It even includes simple PC performance and health reports as well as parental controls with content filtering, usage limitations, and location tracking.
How do firewalls stop hackers?
A firewall can help protect your computer and data by managing your network traffic. It does this by blocking unsolicited and unwanted incoming network traffic. A firewall validates access by assessing this incoming traffic for anything malicious like hackers and malware that could infect your computer.
How many firewalls are enough?
If your network is entirely client-protecting, or is client-protecting with just a few incoming services, such as email, then one firewall (or a pair of firewalls configured as a high-availability pair) is probably all you need.
Which apps allow firewall?
The apps you want are your browsers like Edge, Chrome, Firefox, Internet Explorer and ports 80 and 443 to be open. That’s what you want to allow. As for private and public the way that works is based on your connection. When you are at home with your machine you want to be set to private network.
What is my firewall IP address?
To find the IP address of your firewall’s internal interface, check the default gateway (also known as the default route) on the computers behind the firewall. On Windows XP, for example, use the “route PRINT” command and check the “Gateway” column for the “Network Destination” of 0.0. 0.0.
How to use VPN to break a firewall on your phone?
Popular VPNs like NordVPN OR ExpressVPN are some of the popular choices of VPN services people prefer to have over anything else. If you are looking to break a firewall, you can do that through VPN services. Here are the steps to have an active VPN on your phone. Download the VPN by choosing the VPN service that you find suitable.
Can VPNs bypass firewalls?
VPN s don’t so much bypass firewalls as they tunnel through them. Almost all VPNs have a tunneling protocol that masks your traffic, giving you complete anonymity and security while browsing the web. By connecting to a server in a location of your choosing, you will receive a new IP address.
How to bypass a firewall?
The key to bypassing firewalls of all types is to choose a VPN with the right security protocols and encryption. It’s also essential that you go for a service that has servers near you to increase your internet speed as well as in locations where you’d like to access content.
Can VPNs be blocked?
Websites and companies can block groups of IP addresses of more popular VPNs, but nobody has the time or the energy to block all VPNs. If the VPN you are using gets blocked, try switching to a lesser-known VPN (you can check our article on the best VPN Free trials for this purpose).