You may be getting pop-ups in Chrome because the pop-up blocker program hasn’t been properly configured. Chrome features only two pop-up blocker settings: “Allow all sites to show pop-ups” and “Do not allow any site to show pop-ups (recommended).” The latter option must be selected to block pop-ups.
Why am I getting pop-up ads all of a sudden?
They are caused by third-party apps installed on your phone. Ads are a way for app developers to make money, and the more ads that are displayed, the more money the developer makes.
Select Site Settings > Pop-up and redirects, and turn on the toggle. On an iPhone or iPad, open Chrome, tap on the three-dot button, and then Settings. Tap on Content Settings > Block pop-ups, and turn off the option.
What is Chrome virus?
What Is the Chromium Virus? The Chromium virus is a malicious web browser that is created using the Chromium code. It is able to overwrite the Chrome browser and replace the original shortcuts with fake ones.
Will uninstalling Chrome get rid of malware?
After you uninstall and install Chrome again and log into your Google account, it will restore any settings, extensions, and potentially malware from the cloud backup. So if resetting browser settings and removing extensions didn’t help, reinstalling Chrome won’t remove malware either.
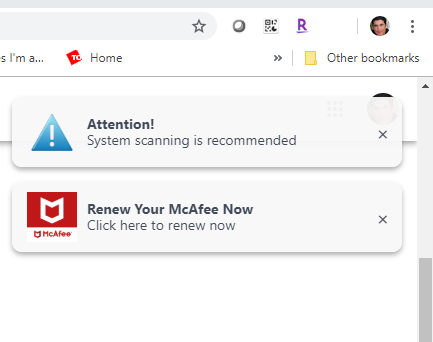
Why do I keep getting a pop-up saying I have a virus?
When Google says you have a virus on your phone, you are being scammed. Specifically, cybercriminals are trying to trick you into installing malware, submitting personal data, or paying for virus removal. Unfortunately, fake virus warnings on Android phones are very common these days.
Are Chrome virus notifications real?
Be aware, however, that “Google Chrome Warning Alert” is a scam. Criminals attempt to scare victims and trick them into paying for technical services that are not required. This malware does not exist and you should never attempt to contact these people.
Is Google Chrome safe from viruses?
Does Chrome have virus protection? Yes, it includes a built-in antivirus for Windows. Chrome Cleanup can quickly scan your PC for suspicious applications and not only.
Is the Chrome browser safe?
Google Chrome is by all accounts a secure browser, with features like Google Safe Browsing, which helps protect users by displaying an impossible-to-miss warning when they attempt to navigate to dangerous sites or download dangerous files. In fact, both Chrome and Firefox have rigorous security in place.
Can opening an email give you a virus?
Can I get a virus by reading my email messages? Most viruses, Trojan horses, and worms are activated when you open an attachment or click a link contained in an email message. If your email client allows scripting, then it is possible to get a virus by simply opening a message.
Can you block all ads on Google?
If you use Google Chrome, use the Adblock Plus extension to get rid of all annoying advertising. Adblock Plus blocks all annoying ads on the web, like YouTube video ads, flashy banner ads, Facebook ads and much more. It even blocks pop-ups which are not blocked by your browser.
Why are ads appearing on Google?
Ads are necessary for many websites to provide services or information at no cost. Ads also help Google provide many services at no cost. As an ad network, Google connects: People who own websites with ad space.
Can I stop Google Ads at any time?
With a Google Ads account, advertisers can customize their budgets and targeting, and start or stop their ads at any time.
How do I stop Windows 10 popups?
In Edge, go to Settings and more at the top of your browser. Select Settings > Cookies and site permissions. Under All permissions, select Pop-ups and redirects. Turn on the Block (recommended) toggle.
What is pop blocker on browser?
A pop-up blocker is any program that prohibits a pop-up at some point in time. This may consist of multiple internet windows, or actual pop-ups caused by coding on a webpage. Generally, pop-up blockers are installed to avoid pop-up ads from webpages.
Is it safe to use Chrome now?
Google Chrome is by all accounts a secure browser, with features like Google Safe Browsing, which helps protect users by displaying an impossible-to-miss warning when they attempt to navigate to dangerous sites or download dangerous files. In fact, both Chrome and Firefox have rigorous security in place.
Can you get malware from Chrome?
Google Chrome includes a feature to synchronize your browser data between computers, including web browser extensions. This is a convenient feature, but when malware infects your Google Chrome browser, it can hitch a ride on the sync data and become difficult to remove with anti-virus programs.
Has Chrome been hacked?
G oogle has announced that Google Chrome has been successfully hacked as it discovers 30 security flaws–seven of which pose a “high” threat to users. In a blog post, Google revealed that a new update will make improvements for Windows, Mac, and Linux, to fix the security issues after the hack.
Why do you need to delete Google Chrome?
The tech giant recently issued a warning to its 2.6billion users about a security flaw in the browser that could be exploited by hackers. While Google has maintained that it is working hard to protect users’ security, cyber experts say it’s time to leave Chrome behind.
Does Chrome have built in virus protection?
Does Chrome have inbuilt Antivirus? YES, Google Chrome comes with an inbuilt Malware scanner. It can search and report the malicious files and applications that are causing the trouble on your system or browser. However, this inbuilt anti-malware only comes with the Windows version of Google Chrome.
What will happen if I uninstall Google Chrome?
If you delete profile information when you uninstall Chrome, the data won’t be on your computer anymore. If you are signed in to Chrome and syncing your data, some information might still be on Google’s servers. To delete, clear your browsing data.
Are pop-ups malware?
Any form of malware can open a pop-up window that contains ads. This is possible because it takes a computer program to display pop-ups and all types of malware are computer programs. If you see pop-up ads while browsing the Web, they may come from a variety of sources that may include your own computer.