The Google Chrome pop-up virus is a common and frustrating malware on Android phones. The most common cause for this virus is downloading apps from third-party or unknown sources which contain the malware. The most important thing is to NOT tap anywhere on the pop-up!
Is the Chrome virus notification real?
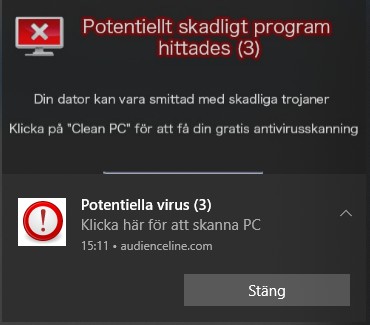
“Google Chrome Warning Alert” is a fake error message displayed by a malicious website that users often visit inadvertently – they are redirected by various potentially unwanted programs (PUPs) that infiltrate systems without consent.
Why do I keep getting messages from Chrome?
By default, Chrome alerts you whenever a website, app, or extension wants to send you notifications. You can change this setting at any time. When you browse sites with intrusive or misleading notifications, Chrome automatically blocks notifications and recommends you continue to block these notifications.
Why am I getting Google Chrome pop up ads?
You may be getting pop-ups in Chrome because the pop-up blocker program hasn’t been properly configured. Chrome features only two pop-up blocker settings: “Allow all sites to show pop-ups” and “Do not allow any site to show pop-ups (recommended).” The latter option must be selected to block pop-ups.
Is Trojan virus real?
Trojan viruses are a type of malware that invade your computer disguised as real, operational programs.
Why do I keep getting virus alerts on my computer?
So, if you see a pop-up window in your web browser that says “Virus Alert from Microsoft,” it means you’re on a website that hosts dangerous pop-ups, or you have adware/potentially unwanted programs (PUPs) infecting your computer.
What is Chrome virus?
What Is the Chromium Virus? The Chromium virus is a malicious web browser that is created using the Chromium code. It is able to overwrite the Chrome browser and replace the original shortcuts with fake ones.
Will uninstalling Chrome get rid of malware?
After you uninstall and install Chrome again and log into your Google account, it will restore any settings, extensions, and potentially malware from the cloud backup. So if resetting browser settings and removing extensions didn’t help, reinstalling Chrome won’t remove malware either.
What is the most damaging computer virus?
Can you remove a trojan virus?
Trojan viruses can be removed in various ways. If you know which software contains the malware, you can simply uninstall it. However, the most effective way to remove all traces of a Trojan virus is to install antivirus software capable of detecting and removing Trojans.
What is a Trojan warning?
What is the Trojan Spyware Alert scam? Scammers behind this tech support scam attempt to trick unsuspecting visitors into believing that their computers are infected with a Trojan and/or Spyware and calling the provided number.
How do I check for malware on Chrome?
To run a scan, you need to open Chrome’s settings. To do so, click on the triple-dot icon in the top-right corner, then click “Settings”. Once in the settings, you should run a quick “Safety check”, to do so, click on “Check now” in the “Safety check” subsection, which is third from the top.
Can Chrome get a virus?
Scanning for viruses can be done very easily on Google Chrome. In this guide, we have explained how viruses can be caught and removed from Windows, Mac, and Android. How do I fix the redirect virus in Chrome?
How long does it take for Google Chrome to check for harmful software?
Chrome generally takes two to five minutes to check for harmful software. You can speed up the process by clearing your cache first. If the CleanUp Tool detects any suspicious programs or extensions, it will prompt you to remove them.
What happens if I reset and clean up Chrome?
Resetting Chrome will restore your home page and search engine to their default settings. It will also disable all browser extensions and clear out your cookie cache. But your bookmarks and saved passwords will remain, at least in theory. You may want to save your bookmarks before performing a browser rest.
How do you tell if Chrome has been hijacked?
The most obvious sign that your browser has been exploited is that your homepage is different from what it used to be or toolbars that you don’t recognize have appeared. You might also see new favorites or bookmarks just below the address bar or if you manually look through the bookmarks.
How did my browser get hijacked?
The browser hijacking software could be bundled with a browser extension or be part of the software. Browser hijackers can also originate from shareware, freeware, adware and spyware infections. Browser hijackers are likely to be downloaded unintentionally by the user.
Is my browser hacked?
One of the most common symptoms of browser hijacking is discovering that your homepage has been reset. If your browser displays an unfamiliar website after launch, particularly one that is pornographic or advertising fake security software, this is almost definitely the work of a hijacker.
Why do I still get pop-ups when I have them blocked?
If you still get pop-ups after disabling them: You may have previously subscribed to receive notifications from a site. You can block notifications if you don’t want any communications from a site to show up on your screen. Your computer or phone may be infected by malware.
Is the ILOVEYOU virus still around?
What did the ILOVEYOU virus do?
ILOVEYOU could — and did — destroy all kinds of files including photographs, audio files and documents. Affected users who didn’t have backup copies lost them permanently. In March 1999, similar to ILOVEYOU, the Melissa virus also replicated itself by using Outlook address books.
Who created ILOVEYOU virus?
Onel de Guzman, a then-24-year-old resident of Manila, Philippines, created the malware.