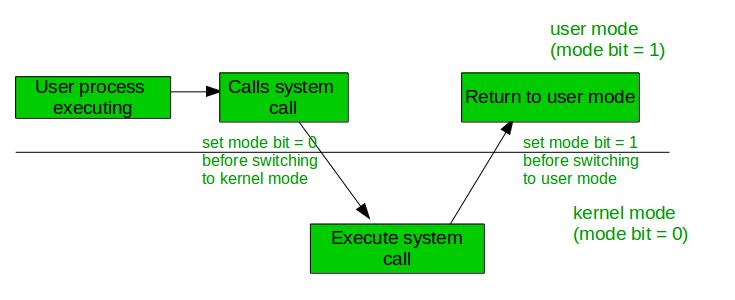
The dual-mode operations in the operating system protect the operating system from illegal users. We accomplish this defense by designating some of the system instructions as privileged instructions that can cause harm. The hardware only allows for the execution of privileged instructions in kernel mode.
What is the need of dual mode operation?
The dual-mode operation is used to provide protection and security to the user program and also to the operating system. Actually, the operating system decides the instruction has to be executed in which particular mode. Mode bit is required to identify in which particular mode the current instruction is executing.
What is dual mode system?
Dual mode refers to mobile devices that function on two different bearer technologies, such as GSM and WCDMA, or 1x and WCDMA.
What is the need of dual mode operation?
The dual-mode operation is used to provide protection and security to the user program and also to the operating system. Actually, the operating system decides the instruction has to be executed in which particular mode. Mode bit is required to identify in which particular mode the current instruction is executing.
How the operating system protects the CPU?
CPU protection: CPU usage is protected by using the timer device, the associated timer interrupts, and OS code called the scheduler. While running in user mode, the CPU cannot change the timer value or turn off the timer interrupt, because these require privileged operations.
What are the two modes of operation?
There are two modes of operation in the operating system to make sure it works correctly. These are user mode and kernel mode.
What are the three main purposes of an operating system?
An operating system has three main functions: (1) manage the computer’s resources, such as the central processing unit, memory, disk drives, and printers, (2) establish a user interface, and (3) execute and provide services for applications software.
What is meant by CPU protection?
CPU protection protects the CPU of the node that it is configured on from a DOS attack by limiting the amount of traffic coming in from one of its ports and destined to the CPM (to be processed by its CPU) using a combination of the configurable limits.
What is the need of memory protection?
The main purpose of memory protection is to prevent a process from accessing memory that has not been allocated to it. This prevents a bug or malware within a process from affecting other processes, or the operating system itself.
What is the importance of system calls?
System call provides the services of the operating system to the user programs via Application Program Interface(API). It provides an interface between a process and operating system to allow user-level processes to request services of the operating system. System calls are the only entry points into the kernel system.
What are the goals of operating system?
Objectives of Operating System To provide users a convenient interface to use the computer system. To act as an intermediary between the hardware and its users, making it easier for the users to access and use other resources. To manage the resources of a computer system.
Which of the following is the advantage of multiprocessor systems?
The advantages of the multiprocessing system are: Increased Throughput − By increasing the number of processors, more work can be completed in a unit time. Cost Saving − Parallel system shares the memory, buses, peripherals etc. Multiprocessor system thus saves money as compared to multiple single systems.
What is the need of dual mode operation?
The dual-mode operation is used to provide protection and security to the user program and also to the operating system. Actually, the operating system decides the instruction has to be executed in which particular mode. Mode bit is required to identify in which particular mode the current instruction is executing.
What are the things that operating system must protect?
Operating System – The OS must protect itself from security breaches, such as runaway processes ( denial of service ), memory-access violations, stack overflow violations, the launching of programs with excessive privileges, and many others.
How does OS provides protection and security to the system?
The most common techniques used to protect operating systems include the use of antivirus software and other endpoint protection measures, regular OS patch updates, a firewall for monitoring network traffic, and enforcement of secure access through least privileges and user controls.
What system is for protection?
The immune system protects your child’s body from outside invaders. These include germs such as bacteria, viruses, and fungi, and toxins (chemicals made by microbes). The immune system is made up of different organs, cells, and proteins that work together.
What is the purpose of mode of operation?
Mode of operation means a condition or manner in which a unit may operate or function while on location or in transit.
Why are two modes user and kernel mode needed?
Why are two modes (user and kernel) needed? User mode prohibits the user from accessing certain areas of memory and executing certain instructions to protect the OS. Kernel mode gives full access to the OS to allow it to do what it needs to do.
What is the use of operation modes?
An operation mode defines a resource configuration for the instances in your system. It can be used to determine which instances are started and stopped, and how the individual services are allocated for each instance in the configuration.
What is the most important purpose of an operating system?
The operating system (OS) manages all of the software and hardware on the computer. It performs basic tasks such as file, memory and process management, handling input and output, and controlling peripheral devices such as disk drives and printers.
What is the purpose of protection?
Protection refers to keeping something or someone safe. Through protection, we shelter and defend things. Since protecting is to shelter from harm, protection is the act of doing so. Children are under the protection of their parents, who keep them safe.
Why protection system is required in a computer?
Computer security is important because it keeps your information protected. It’s also important for your computer’s overall health; proper computer security helps prevent viruses and malware, which allows programs to run quicker and smoother.