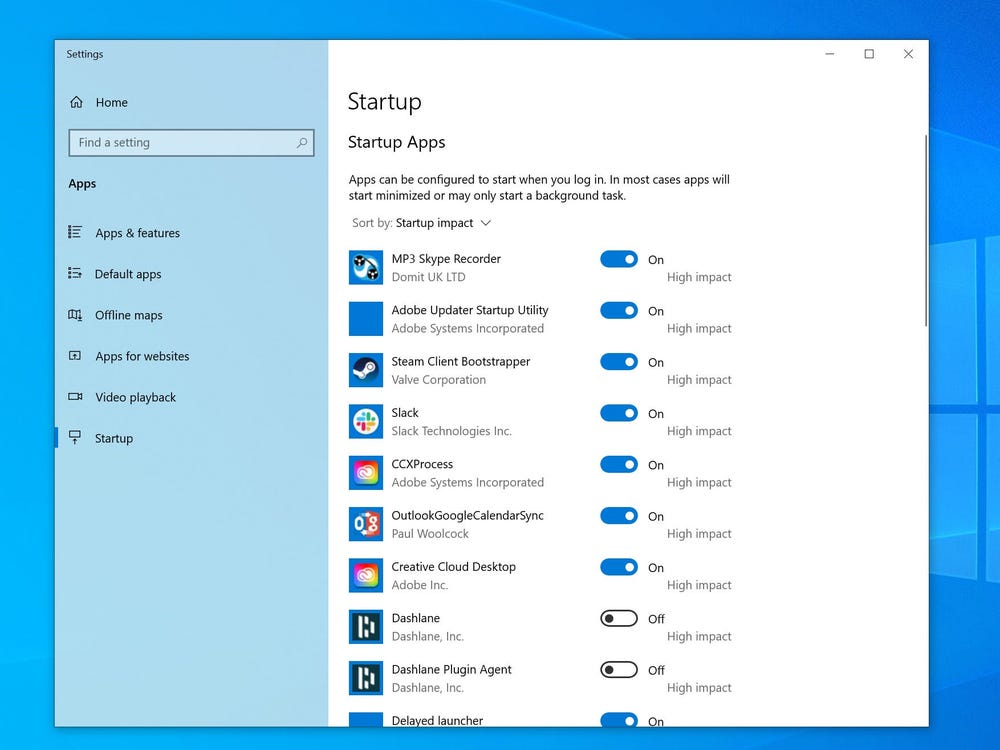
A slow computer is often caused by too many programs running simultaneously, taking up processing power and reducing the PC’s performance. Some programs will continue running in the background even after you have closed them or will start automatically when you boot up your computer.
How do you find out what is slowing down my PC?
Windows has a built-in diagnostics tool called Performance Monitor. It can review your computer’s activity in real time or through your log file. You can use its reporting feature to determine what’s causing your PC to slow down. To access Resource and Performance Monitor, open Run and type PERFMON.
Why is my computer running so slow all of a sudden?
In addition to bad network drivers, faulty or missing drivers for any hardware elements can cause your computer to run slowly. The most likely culprits are chipset, hard drive and hard drive controllers, and graphics card drivers. If you suspect a driver issue, first turn to Device Manager.
Why is my computer so slow all of a sudden Windows 10?
One reason your Windows 10 PC may feel sluggish is that you’ve got too many programs running in the background — programs that you rarely or never use. Stop them from running, and your PC will run more smoothly.
What files can I delete to speed up my computer?
Temporary files like internet history, cookies, and caches take up a ton of space on your hard disk. Deleting them frees up valuable space on your hard disk and speeds up your computer.
How do you check if my computer has a virus?
To run it, go to “Windows Security” > “Virus & threat protection” > “Scan options,” and select “Microsoft Defender Offline scan.” After clicking the “Scan now” button, your computer will restart into a special mode to do a scan. Once it’s done, your computer will restart again, bringing you back to Windows.
Will resetting PC remove virus?
Running a factory reset, also referred to as a Windows Reset or reformat and reinstall, will destroy all data stored on the computer’s hard drive and all but the most complex viruses with it. Viruses can’t damage the computer itself and factory resets clear out where viruses hide.
Is McAfee a good antivirus?
McAfee’s antivirus scanner scored an impressive 100% malware detection rating in all of my tests across Windows, Mac, Android, and iOS devices. It was able to identify and block both simple and sophisticated threats, including viruses, trojans, spyware, ransomware, and cryptojackers.
What are the most common ways to be infected by a computer virus?
Methods of Malware and Virus Infection and Spread Downloading infected files as email attachments, from websites or through filesharing activities. Clicking on links to malicious websites in emails, messaging apps or social network posts.
Can you get a virus without downloading anything?
Yes, you can get a virus just from visiting a website. These days, it’s very easy to be overconfident in our abilities to avoid computer viruses. After all, many of us were told that we simply had to avoid files and programs we didn’t recognize. If an email came through that looked fishy, we didn’t open them.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Can you tell if someone is remotely accessing your computer?
You can use the Windows Task Manager on your computer to assess whether any programs have been opened on your computer without your knowledge. If you see programs in use that you did not execute, this is a strong indication that remote access has occurred.
Who is the No 1 hacker in world?
Kevin Mitnick is the world’s authority on hacking, social engineering, and security awareness training. In fact, the world’s most used computer-based end-user security awareness training suite bears his name. Kevin’s keynote presentations are one part magic show, one part education, and all parts entertaining.
How do hackers take control of your computer?
Another common way that hackers use to gain control of your computers is by sending out Trojan Viruses disguised as email attachments. Hackers typically send out these messages to 1000s of users with enticing headings and an attachment which they are hoping you will open.
Does restarting your PC delete everything?
Simply restarting your computer does not remove any of your important files and installed applications.
Why you should reset your PC?
Speeds up Performance – Reboots are known to keep computers running quickly. By flushing the RAM, your computer can run a lot faster without all those temporary files piled onto your PC’s memory.
Which is better Norton or McAfee?
If you don’t have time to read the full McAfee vs Norton comparison, I can tell you that the winner is Norton. It boasts superior malware protection results from independent labs and better additional security features such as a VPN, cloud backup and webcam protection.
How much does McAfee renewal cost?
See System Requirements for additional information. Free Trial Terms: At the end of your trial period you will be charged $39.99 for the first term. After the first term, you will be automatically renewed at the renewal price (currently $124.99/yr). We will charge you 7-days before renewal.
Can a computer get a virus without internet?
Yes,you will able to get the virus from devices like pen drives,dvd, etc to your system without using internet and without using any background programs as well.
Can just opening an email give you a virus?
Can I get a virus by reading my email messages? Most viruses, Trojan horses, and worms are activated when you open an attachment or click a link contained in an email message. If your email client allows scripting, then it is possible to get a virus by simply opening a message.
Can you get a virus on your phone by visiting a website?
Can phones get viruses from websites? Clicking dubious links on web pages or even on malicious advertisements (known as malvertising) can download malware to your cell phone. Similarly, downloading software from these websites can also lead to malware being installed on your Android phone or iPhone.
What if I accidentally clicked on a suspicious link?
If you suspect your device has been compromised after clicking on a phishing link, the first thing you should do is disconnect your device from the internet and all other networks. This will prevent malware from spreading to synchronized devices.