Google added this network monitoring warning as part of the Android KitKat (4.4) security enhancements. This warning indicates that a device has at least one user-installed certificate, which could be used by malware to monitor encrypted network traffic.
Is someone monitoring my Internet?
Internet Service Providers (ISPs) can see everything you do online. They can track things like which websites you visit, how long you spend on them, the content you watch, the device you’re using, and your geographic location.
Is my Internet activity being monitored on my phone?
To check your mobile data usage on Android, go to Settings > Network & Internet > Data Usage. Under Mobile, you’ll see the total amount of cellular data being used by your phone. Tap Mobile Data Usage to see how your data use has changed over time. From here, you can identify any recent spikes.
How do I know if my IP address is being tracked?
The Netstat command works best when you have as few applications opened as possible, preferably just one Internet browser. The Netstat generates a list of Internet Protocol (IP) addresses that your computer is sending information to.
How do I remove Kaspersky filter?
Go to the Network settings section. Clear the Monitor all ports for the applications from the list recommended by Kaspersky checkbox. Click Save and restart the computer.
Can someone spy on you through Wi-Fi?
By just listening to existing Wi-Fi signals, someone will be able to see through the wall and detect whether there’s activity or where there’s a human, even without knowing the location of the devices. They can essentially do a monitoring surveillance of many locations. That’s very dangerous.”
How can I see who is on my network?
How to access a list of connected devices. The most accurate way to access a list of connected devices is to log into your router’s settings page. If your router was provided by your internet service, such as Spectrum, you may be able to easily log into your account to find this info.
Can someone monitor your internet activity through Wi-Fi?
Well, the short answer to the question is yes. Almost every Wi-Fi router keeps logs of the websites the connected devices are visiting. Only the Wi-Fi owner has the permission to check out the logs of the Wi-Fi router to understand which connected user visited which websites.
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.
Should I be worried if someone has my IP address?
No, you shouldn’t worry if someone has your IP address. If someone has your IP address, they could send you spam or restrict your access to certain services. In extreme cases, a hacker might be able to impersonate you. However, all you need to do to fix the problem is change your IP address.
Can someone spy on me with my IP address?
A hacker may spy on your IP address to track your events and use your IP address to their advantage. Intruders can use sophisticated techniques along with your IP address to hack your systems. As a user, you would want to browse the Internet with full freedom and having no fear of any privacy invasions.
Can someone track my browsing history?
Vulnerabilities. Private browsing is not secure, nor is it completely private. It’s a feature of your Web browser, which means that other applications can still access your online activity. If a keylogger or spyware is installed on your machine, someone can use these programs to track your private browsing activity.
Can my neighbor see my internet activity?
The short answer is, “Absolutely!” Whoever provides you with your internet connection can monitor all of the traffic that goes across your use of that connection.
Can someone spy on me with my IP address?
A hacker may spy on your IP address to track your events and use your IP address to their advantage. Intruders can use sophisticated techniques along with your IP address to hack your systems. As a user, you would want to browse the Internet with full freedom and having no fear of any privacy invasions.
Should I disable Kaspersky?
Important: Kaspersky Lab strongly advises against disabling protection or protection components, because disabling them may lead to infection of your computer and data loss.
Can a router be used as a listening device?
Home routers from 10 manufacturers, including Linksys, DLink, and Belkin, can be turned into covert listening posts that allow the Central Intelligence Agency to monitor and manipulate incoming and outgoing traffic and infect connected devices.
Can the WiFi owner see what I search?
— Can WiFi owner see what I search? The answer is “NO” unless you use some outdated search engine from the past. Today all contemporary web-searches have HTTPS enabled on their sites so all data inside all of the search engine pages are encrypted and no WiFi owner can see what you searched.
What can WiFi owner see?
Wi-Fi owners can actually see more than you think they can. With access to the right tools and software, a Wi-Fi owner can see sites you’ve visited, the date and time of visiting said sites, and even your duration of staying on a site. The Wi-Fi owner needs to first sign in to their router to access browsing activity.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.
What number do you call to see if your phone is tapped?
You can use secret USSD codes to maintain your security and privacy. Just go to your keypad interface and type in either *#21*, *#67#, or *#62# then tap the dial icon. If one doesn’t work, try another.
How do I know if someone is tracking my location?
Android and iPhone’s iOS do not notify or give an indication when someone checks your location. There is a brief icon displayed in the notification bar when GPS is used by location services. Any number of apps or system processes trigger a location check.
Does *# 21 tell you if your phone is tapped?
The code does not show if a phone has been tapped How-to Geek described the *#21# feature as an “interrogation code” that allow users to view their call forwarding setting from the phone app. “These are not related at all.
What does “networks may be monitored” mean?
When a security certificate is added to your phone (either manually by you, maliciously by another user, or automatically by some service or site you’re using) and it is not issued by one of these pre-approved issuers, then Android’s security feature springs into action with the warning “Networks May Be Monitored.”…
Why does my Android phone keep saying network may be monitored?
For the error message you are getting, when a security certificate is added to your phone (either manually by you, by another user, or automatically by some service or site you are using) and it is not issued by a pre-approved (by Google) issuer, then Android’s default security setting is to display the warning that “Networks May Be Monitored”.
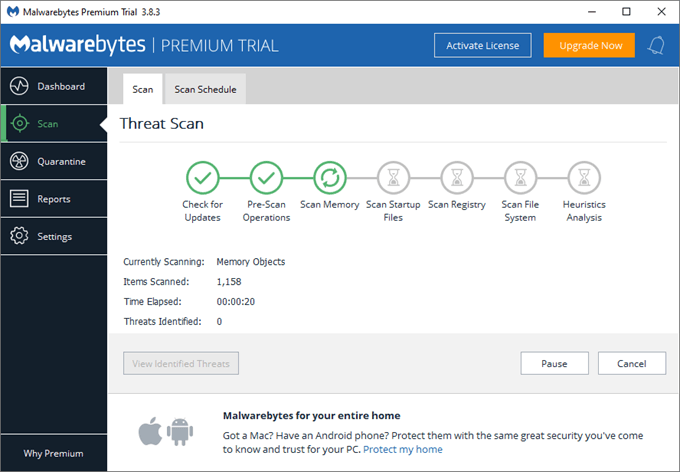
How to know if your computer is not being monitored?
Here are 7 different ways to confirm if your computer is free from being monitored or not. 1. Monitoring processes from Windows Task Manager Press Ctrl + Alt + Del Key together to start Windows Security. Select Task Manager to open the Task Manager Window. If it is the minimal view, Click on More details to open the detailed view.
What is a network monitoring tool?
Sometimes the interface uses a proprietary program running on a client on the local network. Many network monitoring tools provide a web interface to manage the application. Some even provide a mobile device interface that can set and manage alerts and display snapshots or graphs of monitored elements.