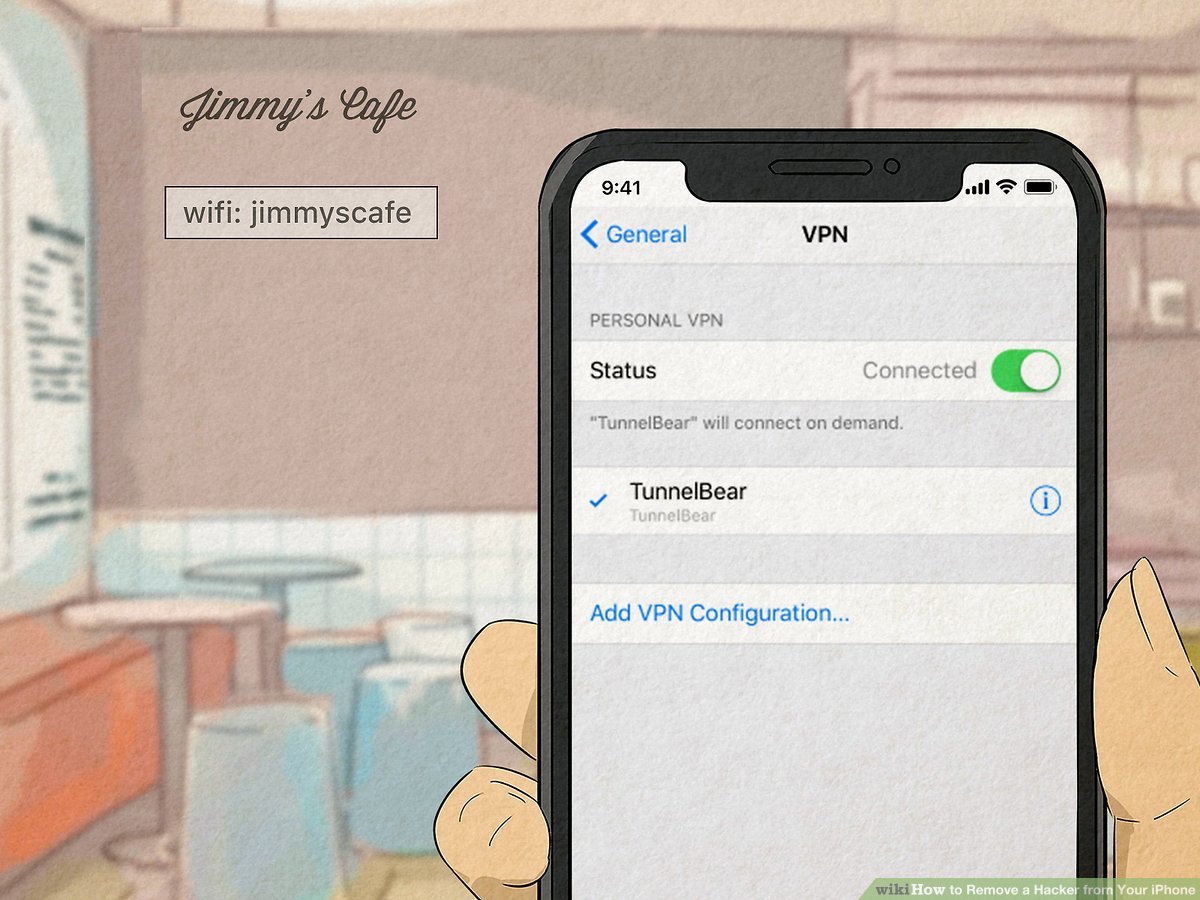
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device.Resetting your phone will remove any hackers that may be on your device. However, it is important to note that resetting your phone will also remove any other data that is stored on the device. What Can A Hacker See On Your Phone?
Does restarting my phone get rid of hackers?
With such a powerful tool at their disposal, Marczak said rebooting your phone won’t do much to stop determined hackers. Once you reboot, they could simply send another zero-click. “It’s sort of just a different model, it’s persistence through reinfection,” he said.
Can you get a hacker out of your phone?
Fix a hacked Android phone with a factory reset A factory reset is a simple procedure that completely cleans your phone’s internal storage. A factory reset deletes not only your photos, videos, messages, and other personal data, but also wipes out malware that lets hackers in.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.
What does *# 21 do to your phone?
We rate the claim that dialing *#21# on an iPhone or Android device reveals if a phone has been tapped FALSE because it is not supported by our research.
Can someone hack your phone just by knowing your number?
Two-factor authentication. It’s important to reiterate that it’s not possible for someone to just simply type your number into some shady software and click “HACK”. There is usually a process of tricking you into doing something as mentioned above.
Should I reset my iPhone if hacked?
If you suspect your iPhone has been hacked, you should reset your phone to its factory settings. What do you have to do to prevent another attack? Never connect to a free Wi-Fi Do not jailbreak your phone Delete any apps on your phone you do not recognize Do not download illegitimate apps, like the flashlight app.
Does resetting phone delete everything?
To remove all data from your phone, you can reset your phone to factory settings. Factory resets are also called “formatting” or “hard resets.” Important: You’re using an older Android version.
Can someone hack my iPhone and change my passcode?
The simple answer to this question is – If you have a fully updated, newer iPhone then there is no publicly known way for someone to hack or brute force an iPhone passcode. This highlights why it’s important to ensure that you keep your phone updated as regularly as possible.
Can you tell if your phone is being monitored?
Yes, there are signs that will tell you when your phone is being monitored. These signs include overheating of your device, the battery draining fast, receiving odd text messages, hearing weird sounds during calls, and random reboots of your phone.vor 4 Tagen
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.
What is this code * * 4636 * *?
Android code: *#*#4636#*#* This code will open up a menu that shows information about your phone’s data usages. Here’s how you can retrieve deleted text messages on your iPhone.
Can hackers see you through your phone camera?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Who is accessing my phone?
Open the Android Settings app. Tap “Mobile Network” (It’s in the “Network & Internet” section.) On the Mobile Network screen, tap “App Data Usage.” Here, you can view your current cellular app data usage.
What happens if you dial *# 31?
If you want to hide the caller ID dial *31# and press call button. This code allows you to check which number your phone is currently forwarding calls to when you’re busy or reject a call.
What is *# 62 code used for?
*#21# – By dialling this USSD code, you would get to know if your calls have been diverted somewhere else or not. *#62# – With this, you can know if any of your calls – voice, data, fax, SMS etc, has been forwarded or diverted without your knowledge.
What is *# 0011?
*#0011# This secret code is used to show the status information for your GSM Network. *#*#4636#*#* Displays all the user statistics from the beginning of time and the essential Phone Information. *#12580*369# this secret code checks software and hardware information.
Should I change my phone number after being scammed?
If you’ve experienced identity theft, you should probably change your phone number. It’s a massive inconvenience, but the pros will outweigh the cons. Let’s understand why. Most people upgrade their smartphone every two years — especially if they’re on a contract plan.
Why am I getting spam calls all of a sudden? Usually it’s because your number has been sold in a group list of phone numbers to other scammers. Remember, you can always report spam calls to the Better Business Bureau and also the Federal Trade Commission.vor 4 Tagen
What’s the worst thing you can do with someone’s phone number?
Some of this information may seem innocent enough, but in the wrong hands, it can expose you to criminal activity. Hackers, identity thieves, and scammers can use your phone number to find out where you are (and where you’ll be), impersonate you, hijack your phone, or use your accounts.
Can someone hack my phone from a text message?
Android phones can get infected by merely receiving a picture via text message, according to research published Monday. This is likely the biggest smartphone flaw ever discovered.
What can a hacker do with your email address?
It may give them information they need to steal money or uncover other personal information that can then be sold on the web. They can also mine your contacts list to send out phishing emails and/or malware to compromise even more accounts or defraud the people you know!
Will restoring the iPhone get rid of hackers?
Restoring the iPhone will remove anything that was on it, and return it to factory condition. Q: will a reset get rid of hackers? A forum where Apple customers help each other with their products. Learn more. Sign up with your Apple ID to get started.
How to remove hacking attack from Android phone?
To restore to factory settings, follow the steps below to remove the hacker from your Android phone. Navigate to settings⇒Find backup & reset⇒Tap factory data reset to reset phone⇒Enter the passcode to erase everything⇒Then, select reboot your phone⇒Finally, restore your phone’s data.
What to do if your phone has been hacked?
Malware phones have this issue depending on your phone carrier. Most cellphone company is breached and compromised internally or externally depending on the competence of your cellphone carrier’s security team. You can do a network reset to reconnect to your cellphone carrier whenever your hacked, factory resets is a temporary fix.
Does factory resetting your phone get rid of viruses?
Bottom Line Though Factory Resetting is an excellent option to boost your phone and get rid of malicious files and programs, it does not always guarantee virus removal. Hard resetting a device is an extreme step; therefore, it is advised to try out every other option and then go for the factory reset if all other ways failed.